A cloud administrator learns that a major version update. 4.6.0. is available for a business-critical application. The application is currently on version 4.5.2. with additional minor versions 3, 4, and 5 available. The administrator needs to perform the update while minimizing downtime. Which of the following should the administrator do first?
A banking firm's cloud server will be decommissioned after a successful proof of concept using mirrored data. Which of the following is the best action to take regarding the storage used on the decommissioned server?
A cloud engineer has provisioned a VM for a high-frequency trading application. After the VM is put into production, users report high latency in trades. The engineer checks the last six hours of VM metrics and sees the following:
• CPU utilization is between 30% to 60%.
• Networkln is between 50Kbps and 70Kbps.
• NetworkOut is between 3.000Kpbs and 5.000Kbps.
• DiskReadOps is at 30.
• DiskWriteOps is at 70
• Memory utilization is between 50% and 70%.
Which of the following steps should the engineer take next to solve the latency issue?
A company's VMs that are created using the noncritical application tag are automatically shut down at 5:00 p.m. using a cronjob. Which of the following actions would allow a cloud engineer to stop all unresponsive instances with the least effort in case the automation fails?
A cloud engineer is reviewing the following Dockerfile to deploy a Python web application:

Which of the following changes should the engineer make lo the file to improve container security?
A systems administrator notices a surge of network traffic is coming from the monitoring server. The administrator discovers that large amounts of data are being downloaded to an external source. While investigating, the administrator reviews the following logs:
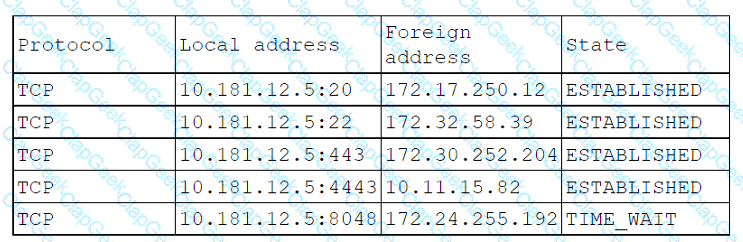
Which of the following ports has been compromised?
A cloud solutions architect needs to design a solution that will collect a report and upload it to an object storage service every time a virtual machine is gracefully or non-gracefully
stopped. Which of the following will best satisfy this requirement?
Which of the following technologies should be used by a person who is visually impaired to access data from the cloud?
A cloud solution needs to be replaced without interruptions. The replacement process can be completed in phases, but the cost should be kept as low as possible. Which of the
following is the best strategy to implement?
A cloud security analyst is looking for existing security vulnerabilities on software applications. Which of the following describes this vulnerability management phase?
A cloud engineer is reviewing a disaster recovery plan that includes the following requirements:
• System state, files, and configurations must be backed up on a weekly basis.
• The system state, file, and configuration backups must be tested annually.
Which of the following backup methods should the engineer implement for the first week the plan is executed?
A video surveillance system records road incidents and stores the videos locally before uploading them to the cloud and deleting them from local storage. Which of the following
best describes the nature of the local storage?
An e-commerce company is migrating from an on-premises private cloud environment to
a public cloud IaaS environment. You are tasked with right-sizing the environment to
save costs after the migration. The company's requirements are to provide a 20% overhead above the average resource consumption, rounded up.
INSTRUCTIONS
Review the specifications and graphs showing resource usage for the web and database servers. Determine the average resource usage and select the correct specifications from the available drop-down options.
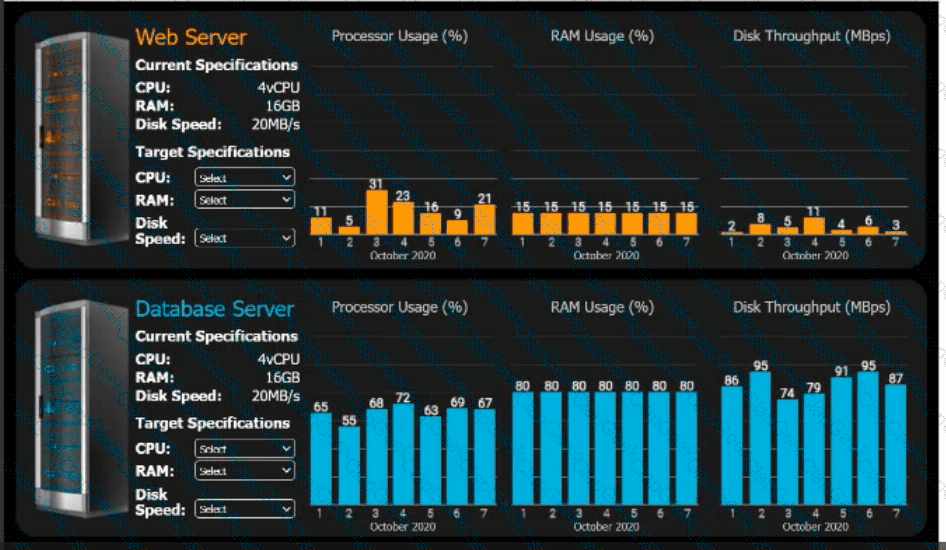
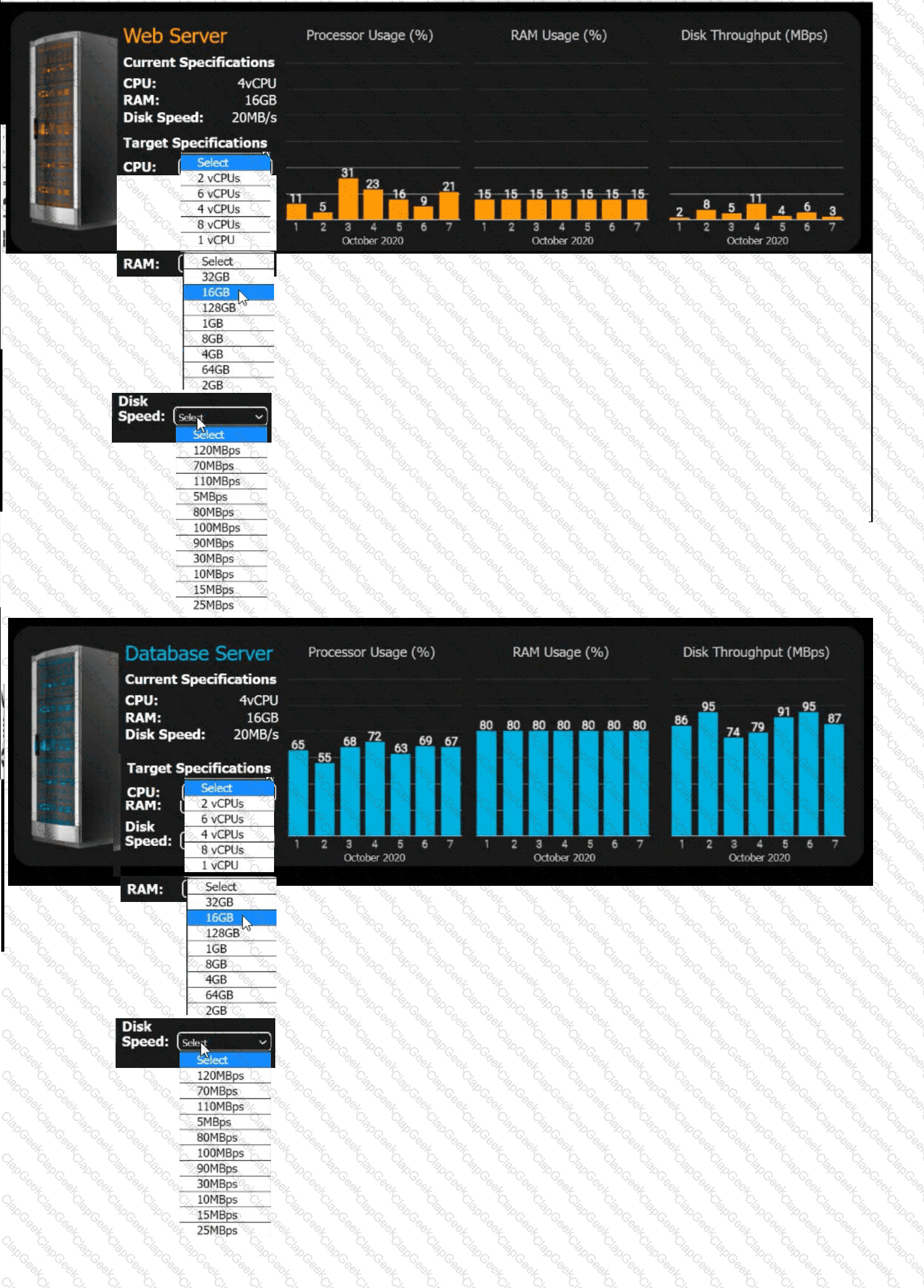
Which of the following situations would require a project manager to revise the communication plan during a project's execution?
Which of the following strategies requires the development of new code before an application can be successfully migrated to a cloud provider?
A cloud engineer wants to implement a disaster recovery strategy that:
. Is cost-effective.
. Reduces the amount of data loss in case of a disaster.
. Enables recovery with the least amount of downtime.
Which of the following disaster recovery strategies best describes what the cloud engineer wants to achieve?
A DevOps engineer is performing maintenance on the mail servers for a company's web application. Part of this maintenance includes checking core operating system updates. The servers are currently running version 3.2 of the operating system. The engineer has two update options—one to version 4.1 and the other to version 3.7. Both versions are fully supported by the operating system manufacturer. Which of the following best describes the action the engineer should take?
Which of the following requirements are core considerations when migrating a small business's on-premises applications to the cloud? (Select two).
A company wants to create a few additional VDIs so support vendors and contractors have a secure method to access the company's cloud environment. When a cloud
administrator attempts to create the additional instances in the new locations, the operation is successful in some locations but fails in others. Which of the following is the
most likely reason for this failure?
A high-usage cloud resource needs to be monitored in real time on specific events to guarantee its availability. Which of the following actions should be used to meet this requirement?
A software engineer is integrating an application lo The cloud that is web socket based. Which of the following applications is the engineer most likely deploying?
Which of the transfer when comparing a multiregional to a single-region cloud platform design?
A company recently migrated to a public cloud provider. The company's computer incident response team needs to configure native cloud services tor detailed logging. Which of the following should the team implement on each cloud service to support root cause analysis of past events? {Select two).
Which of the following do developers use to keep track of changes made during software development projects?
Which of the following would allow a cloud engineer to flatten a deeply nested JSON log to improve readability for analysts?
An organization's internal security team mandated that public cloud resources must be accessible only by a corporate VPN and not by direct public internet access. Which of the
following would achieve this objective?
A cloud engineer is troubleshooting a connectivity issue. The application server with IP 192.168.1.10 in one subnet is not connecting to the MySQL database server with IP 192.168.2 20 in a different subnet. The cloud engineer reviews the following information:
Application Server Stateful Firewall
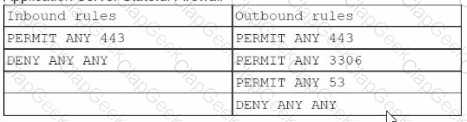
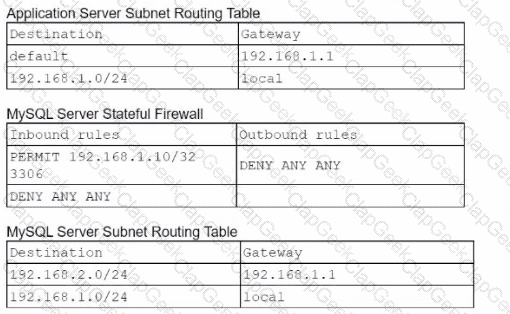
Which of the following should the cloud engineer address lo fix the communication issue?
Which of the following network types allows the addition of new features through the use of network function virtualization?
An organization's critical data was exfiltrated from a computer system in a cyberattack. A cloud analyst wants to identify the root cause and is reviewing the following security logs of
a software web application:
"2021/12/18 09:33:12" "10. 34. 32.18" "104. 224. 123. 119" "POST / login.php?u=administrator&p=or%201%20=1"
"2021/12/18 09:33:13" "10.34. 32.18" "104. 224. 123.119" "POST /login. php?u=administrator&p=%27%0A"
"2021/12/18 09:33:14" "10. 34. 32.18" "104. 224. 123. 119" "POST /login. php?u=administrator&p=%26"
"2021/12/18 09:33:17" "10.34. 32.18" "104. 224. 123.119" "POST / login.php?u=administrator&p=%3B"
"2021/12/18 09:33:12" "10.34. 32. 18" "104. 224. 123. 119" "POST / login. php?u=admin&p=or%201%20=1"
"2021/12/18 09:33:19" "10.34.32.18" "104. 224. 123.119" "POST / login. php?u=admin&p=%27%0A"
"2021/12/18 09:33:21" "10. 34. 32.18" "104.224. 123.119" "POST / login. php?u=admin&p=%26"
"2021/12/18 09:33:23" "10. 34. 32.18" "104. 224. 123.119" "POST / login. php?u=admin&p=%3B"
Which of the following types of attacks occurred?
Which of the following migration types is best to use when migrating a highly available application, which is normally hosted on a local VM cluster, for usage with an external user population?
Which of the following best describes a system that keeps all different versions of a software separate from each other while giving access to all of the versions?
A network administrator is budding a site-to-site VPN tunnel from the company's headquarters office 10 the company's public cloud development network. The network administrator confirms the following:
The VPN tunnel is established on the headquarter office firewall.
While inside the office, developers report that they cannot connect to the development network resources.
While outside the office on a client VPN, developers report that they can connect to the development network resources.
The office and the client VPN have different IP subnet ranges.
The firewall flow logs show VPN traffic is reaching the development network from the office.
Which of the following is the next step the next network administrator should take to troubleshoot the VPN tunnel?
Which of the following cloud deployment strategies is best for an organization that wants to run open-source workloads with other organizations that are sharing the cost?
A cloud engineer wants to replace the current on-premises. unstructured data storage with a solution in the cloud. The new solution needs to be cost-effective and highly scalable. Which of the following types of storage would be best to use?
An organization needs to retain its data for compliance reasons but only when required. Which of the following would be the most cost-effective type of tiered storage?
Which of the following are best practices when working with a source control system? (Select two).
A technician receives an email from a vendor who is requesting payment of an invoice for human resources services. The email contains a request for bank account numbers. Which of the following types of attacks does this behavior most likely indicate?
A group of cloud administrators frequently uses the same deployment template to recreate a cloud-based development environment. The administrators are unable to go back and
review the history of changes they have made to the template. Which of the following cloud resource deployment concepts should the administrator start using?
Which of the following is an auditing procedure that ensures service providers securely manage the data to protect the interests of the organization and the privacy of its clients?
A security analyst confirms a zero-day vulnerability was exploited by hackers who gained access to confidential customer data and installed ransomware on the server Which of the following steps should the security analyst take? (Select two).
An DevOps engineer is receiving reports that users can no longer access the company's web application after hardening of a web server. The users are receiving the following error:
ERR_SSLJ/ERSION_OR_CIPHER_MISMATCH.
Which of the following actions should the engineer take to resolve the issue?
Which of the following is a customer be responsible for in a provider-managed database service? (Select two).
A cloud engineer needs to integrate a new payment processor with an existing e-commerce website. Which of the following technologies is the best fit for this integration?
Which of the following is a field of computer science that enables computers to identify and understand objects and people in images and videos?
A cloud engineer needs to deploy a new version of a web application to 100 servers. In the past, new version deployments have caused outages. Which of the following deployment types should the cloud engineer implement to prevent the outages from happening this time?
A cloud consultant needs to modernize a legacy application that can no longer address user demand and is expensive to maintain. Which of the following is the best migration
strategy?
A company's website suddenly crashed. A cloud engineer investigates the following logs:
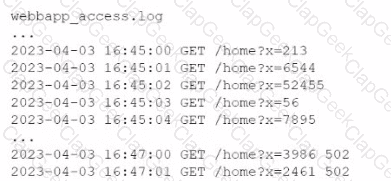
Which of the following is the most likely cause of the issue?
An organization is hosting a seminar with eight individuals who need to connect to their own dedicated VM. The technician used the following VM configurations:
IP address: DHCP
NIC: 1Gbps
Network: 10.1.10.0/29
Several users are unable to access their VMs. Which of the following best describes the reason?
For compliance purposes, a cloud developer at an insurance company needs to save all customer policies for more than ten years. Which of the following options is the most cost-
efficient tier to save the data in the cloud?
A newly configured VM fails to run application updates despite having internet access. The updates download automatically from a third-party network. Given the following output:
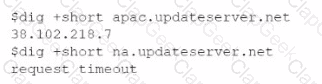
Which of the following troubleshooting steps would be best to take?
A security engineer Identifies a vulnerability m a containerized application. The vulnerability can be exploited by a privileged process to read tie content of the host's memory. The security engineer reviews the following Dockerfile to determine a solution to mitigate similar exploits:

Which of the following is the best solution to prevent similar exploits by privileged processes?
A cloud engineer was deploying the company's payment processing application, but it failed with the following error log:
ERFOR:root: Transaction failed http 429 response, please try again Which of the following are the most likely causes for this error? (Select two).
A highly scored negative risk causes a risk trigger, but the issue has not started yet. Which of the following is the next step the project team should take?
An e-commerce store is preparing for an annual holiday sale. Previously, this sale has increased the number of transactions between two and ten times the normal level of
transactions. A cloud administrator wants to implement a process to scale the web server seamlessly. The goal is to automate changes only when necessary and with minimal cost.
Which of the following scaling approaches should the administrator use?
A bank informs an administrator that changes must be made to backups for long-term reporting purposes. Which of the following is the most important change the administrator
should make to satisfy these requirements?
A SaaS provider introduced new software functionality for customers as part of quarterly production enhancements. After an update is implemented, users cannot locate certain transactions from an inbound integration. During the investigation, the application owner finds the following error in the logs:
Error: REST API - Deprecated call is no longer supported in this release.
Which of the following is the best action for the application owner to take to resolve the issue?
The PMO wants to streamline the routing and approval of project activities to provide up-to-date visibility of the status. Which of the following collaboration tools would be most appropriate to use?
An administrator is setting up a cloud backup solution that requires the following features:
• Cost effective
• Granular recovery
• Multilocation
Which of the following backup types best meets these requirements?
A project team is reviewing the project plan and related documents and identifies tasks that could be spread into smaller deliverables. Which of the following documents should the team edit first?
A cross-site request forgery vulnerability exploited a web application that was hosted in a public laaS network. A security engineer determined that deploying a WAF in blocking mode at a CDN would prevent the application from being exploited again. However, a week after implementing the WAF, the application was exploited again. Which of the following should the security engineer do to make the WAF control effective?
A cloud administrator deploys new VMs in a cluster and discovers they are getting IP addresses in the range of 169.254.0.0/16. Which of the following is the most likely cause?
A cloud deployment uses three different VPCs. The subnets on each VPC need to communicate with the others over private channels. Which of the following will achieve this objective?
Which of the following describes the main difference between public and private container repositories?
A project manager is assigned to a project that has contracted with vendors. Which of the following actions should the project manager most frequently take? (Select two).
A critical security patch is required on a network load balancer in a public cloud. The organization has a major sales conference next week, and the Chief Executive Officer does not want any interruptions during the demonstration of an application behind the load balancer. Which of the following approaches should the cloud security engineer take?
Which of the following is used to deliver code quickly and efficiently across the development, test, and production environments?
A company just learned that the data in its object storage was accessed by an unauthorized party. Which of the following should the company have done to make the data unusable?
Which of the following integration systems would best reduce unnecessary network traffic by allowing data to travel bidirectionally and facilitating real-time results for developers who need to display critical information within applications?
A systems administrator is provisioning VMs according to the following requirements:
· A VM instance needs to be present in at least two data centers.
. During replication, the application hosted on the VM tolerates a maximum latency of one second.
· When a VM is unavailable, failover must be immediate.
Which of the following replication methods will best meet these requirements?