A company's primary performance objective Is flexibility. Which of the following measurements is most important?
During a security incident investigation, a security analyst discovered an unauthorized module was compiled into an application package as part of the application assembly phase. This incident occurred immediately prior to being digitally signed and deployed using a deployment pipeline.
Which of the following security controls would BEST prevent this type of incident in the future?
Which of the following statements is an advantage of a fourth-party logistics (4PL) provider?
Under which of the following conditions is excess capacity most likely a good substitute for safety stock?
A cloud-based web application requires the use of cryptographic keys to encrypt user-uploaded files at rest. Where is the safest place to store these cryptographic keys?
Which of the following concepts MOST accurately refers to an organization's ability to fully understand the health of the data in its system at every stage of the lifecycle?
A work center has 3 machines that are all run at the same time with a single worker. The work center has an efficiency of 75% and a utilization of 100%. What is the work center's capacity in standard hours for an 8-hour shift?
An attacker wants to decrypt a message and has no knowledge of what may have been in the original message. The attacker chooses to use an attack that will exhaust the keyspace in order to decrypt the message. What type of cryptanalytic attack is the attacker using?
Marketing has requested a significant change in the mix for a product family. The requested change falls between the demand and the planning time fences. The most appropriate action by the master scheduler is to:
Which security audit phase is MOST important to ensure correct controls are applied to classified data in a production environment?
Which of the physiological biometric scanning methods is considered the MOST invasive?
The horizon for forecasts that are input to the sales and operations planning (S&OP) process should be long enough that:
A systems engineer has been tasked by management to provide a recommendation with a prioritized, focused set of actions to help the organization stop high-risk cyber attacks and ensure data security. What should the systems engineer recommend the organization use to accomplish this?
Long lead-time items with stable demand would best be supported by a supply chain:
After a recent cybersecurity incident, a manufacturing organization is interested in further hardening its Identity and Access Management (IAM) solution. Knowing that the organization limits the use of personal devices in the facility, which could BEST be implemented to enhance the manufacturing organization's IAM solution?
In the context of mobile device security, which of the following BEST describes why a walled garden should be implemented?
A company is having trouble with raw material deliveries and has decided to develop a supplier certification program. The certification process most appropriately would start with which of the following suppliers?
When assessing a new vendor as a possible business partner, what would BEST demonstrate that the vendor has a proactive approach to data security compliance?
Typically, rough-cut capacity planning (RCCP) in a job shop environment would review which of the following work centers to determine the ability to execute the plan?
Which specification enables organizations to ensure penetration test results are documented using open, machine-readable standards?
An agency has the requirement to establish a direct data connection with another organization for the purpose of exchanging data between the agency and organization systems. There is a requirement for a formal agreement between the agency and organization. Which source of standards can the system owners use to define the roles and responsibilities along with details for the technical and security requirements?
Which of the following presents the GREATEST benefit to an organization's security posture when a change management process is implemented?
Which of the following is typically used to control physical access to highly secure facilities?
Which of the following conditions is most likely to result in planned production that is greater than the total demand over the sales and operations planning (S&OP) horizon for a product family that is
made to stock?
Which of the following is MOST accurate when comparing patch management and vulnerability management?
An organization is updating an Application Programming Interface (API) to support requests coming from mobile applications distributed on public application stores. The API’s primary function is to supply confidential documents when users request them within the mobile application. Which approach would BEST respond to this use case?
Which of the following does a federated Identity Provider (IDP) need in order to grant access to identity information?
An organization processes healthcare data, stores credit card data, and must provide audited financial statements, each of which is controlled by a separate compliance standard. To support compliance against multiple standards and the testing of the greatest number of controls with a limited budget, how would the internal audit team BEST audit the organization?
An organization is working to secure its Supervisory Control And Data Acquisition (SCADA) system, Which monitors water supply to the city. What type of security should the organization ensure FIRST?
Which of the following is a document that will be obtained at the end of an asset’s lifecycle?
The primary outcome of frequent replenishments in a distribution requirements planning (DRP) system is that:
An organization provides customer call center operations for major financial service organizations around the world. As part of a long-term strategy, the organization plans to add healthcare clients to the portfolio. In preparation for contract negotiations with new clients, to which cybersecurity framework(s) should the security team ensure the organization adhere?
An organization’s external auditors have issued a management letter identifying significant deficiencies related to the effectiveness of the previous year’s global access certification. The organization wants to move from a department-based access control system to a Role-Based Access Control (RBAC) system. In addition to quickly and securely provisioning users by granting membership into predefined and approved roles, which of these presents the BEST reason to do so?
Exhibit:
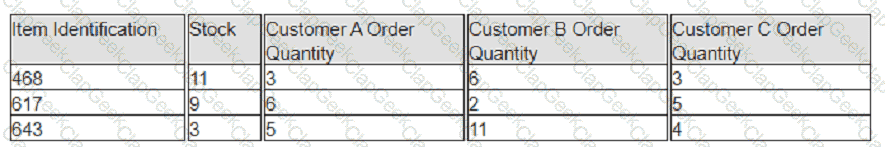
A company has prioritized customers A, B, and C, filling orders in that sequence. What are the impacts to customer service levels for customers B and C?
Which of the following mechanisms should a practitioner focus on for the MOST effective information security continuous monitoring?
A large organization that processes protected data issues preconfigured laptops to workers who then access systems and data based on their role. As their technology ages, these laptops are replaced with newer devices. What is the BEST solution to mitigate risk associated with these devices?
What are the FIRST two steps an organization should conduct to classify its assets?
An organization is migrating some of its applications to the cloud. The Chief Information Security Officer (CISO) is concerned about the accuracy of the reports showing which application should be migrated and how many applications reside on each server. As a result, the CISO is looking to establish asset management requirements. Which of these elements should be considered part of asset management requirements?
The Chief Security Officer (CSO) of an organization would like to have a network security assessment done by the security team. Which of the following is the FIRST step in the security testing methodology?
An information system containing Protected Health Information (PHI) will be accessed by doctors, nurses, and others working in a hospital. The same application will be used by staff in the pharmacy department only for dispensing prescribed medication. Additionally, patients can log in to view medical history. The system owner needs to propose an access control model that considers environment, situation, compliance, and security policies while dynamically granting the required level of access. Which access control model is the MOST suitable?
An organization has been struggling to improve their security posture after a recent breach. Where should the organization focus their efforts?
If the total part failure rate of a machine is 0.00055 failures per hour, what would be the mean time between failures (MTBF) in hours?
An information security auditor is creating an audit program to assess endpoint security controls for portable storage media movement. Which type of control will MOST likely be part of the program?
Endpoint security needs to be established after an organization procured 1,000 industrial Internet Of Things (IoT) sensors. Which of the following challenges are the security engineers MOST likely to face?
If organizational leadership determines that its required continuous monitoring plan is too costly for the organization, what action should be taken by leadership and the Authorizing Official (AO)?
A company assembles kits of hand tools after receipt of the order from distributors and uses two-level master scheduling. The appropriate levels of detail for the forecasts that are input to master scheduling would be total number of kits and:
Disaster Recovery Plan (DRP) training can be considered complete when the participants
A company selling seasonal products is preparing their sales and operations plan for the coming year. Their current labor staffing is at the maximum for their production facility and cannot meet the forecasted demand. The business plan shows they do not have the financial capability to add to the production facility. Which of the following actions would be most appropriate?
An organization suffered a loss to an asset at a frequency that was different than the initially estimated Annualized Rate of Occurrence (ARO). What is the appropriate course of action?
A security professional is accessing an organization-issued laptop using biometrics to remotely log into a network resource. Which type of authentication method is described in this scenario?
Which protocol is the BEST option to provide authentication, confidentiality, and data integrity between two applications?
A manufacturer begins production of an item when a customer order is placed. This is an example of a(n):
An OpenID Connect (OIDC) authorization server received two requests from a client. The server identifies the request as replay attack and rejects the request. Which of the following BEST describes these requests?
The question below is based on the following standard and actual data of a production order
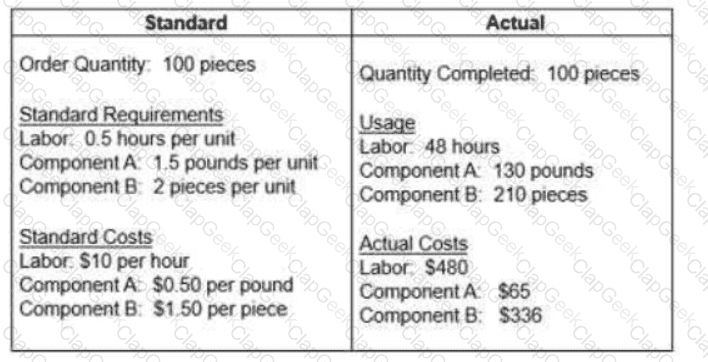
Which of the following statements about variances is true?
The demand for an item has increasing forecast error, whereas all other factors remain constant. Which of the following remains constant while maintaining the same customer service level?
What is the BEST protection method to ensure that an unauthorized entry attempt would fail when securing highly sensitive areas?
An organization has integrated its enterprise resource planning system into its centralized Identity and Access Management (IAM) system to automate provisioning of access. A security audit revealed that privileged access granted within the ERP system is not visible in the IAM system. Which of the following controls BEST mitigates this risk?
Small, independent demands for components and subassemblies typically arise from which of the following sources?
An information security professional is tasked with configuring full disk encryption on new hardware equipped with a Trusted Platform Module (TPM). How does TPM further enhance the security posture of full disk encryption if configured properly?
The security department was notified about vulnerabilities regarding users' identity verification in a web application. Which of the following vulnerabilities is the security professional MOST likely to test?
Which of the following is a PRIMARY benefit of sharing assessment results among key organizational officials across information boundaries?
Which of the following design considerations would offer the BEST protection against unauthorized access to the facility?
At which Open Systems Interconnection (OSI) layer does User Datagram Protocol (UDP) function?
What is the PRIMARY benefit an organization obtains by adapting a cybersecurity framework to their cybersecurity program?
A hot Disaster Recovery (DR) data center is the victim of a data breach. The hackers are able to access and copy 10GB of clear text confidential information. Which of the following could have decreased the amount of exposure from this data breach?
An organization has network services in a data center that are provisioned only for internal use, and staff at offices and staff working from home both use the services to store sensitive customer data. The organization does not want the Internet Protocol (IP) address of the service to receive traffic from users not related to the organization. Which technology is MOST useful to the organization in protecting this network?
Which of the following procedures should be defined when establishing information and asset handling requirements?
A cybersecurity analyst is responsible for identifying potential security threats and vulnerabilities in the organization's software systems. Which action BEST demonstrates the understanding and application of threat modeling concepts and methodologies?
Which of the following ensures privileges are current and appropriately reflect an individual’s authorized roles and responsibilities?
Which of the following vulnerability types is also known as a serialization flaw and affects the integrity of two processes interacting with the same resource at the same time?
In conducting a new corporate payroll system security review, which of the following individuals should answer questions regarding the data classification?
Which of the following should be done FIRST when implementing an Identity And Management (IAM) solution?
An organization is aiming to be System and Organization Controls (SOC) 2 certified by an audit organization to demonstrate its security and availability maturity to its sub service organizations. Which type of audit does this engagement BEST describe?
A cybersecurity professional has been tasked with instituting a risk management function at a new organization. Which of the following is the MOST important step the professional should take in this endeavor?
Health information stored in paper form may be destroyed using which of the following methods?
An organization's security policy requires remote hosts to be authenticated before they can access network resources. Which of the following is the BEST option for the organization to enforce its policy?
Which of the following stock location systems would you use in a repetitive manufacturing, lean environment?
An organization is looking to integrate security concepts into the code development process early in development to detect issues before the software is launched. Which advantage does the organization gain from using Static Application Security Testing (SAST) techniques versus dynamic application security testing techniques?
An executive wants to ensure that risk related to information operations is managed in accordance with the enterprise's risk management thresholds. What is the BEST way to ensure this consistently occurs?
A low-cost provider strategy works best when which of the following conditions are met?
The production plan relates to a firm's financial planning because it is used to:
Which software development methodology is an iterative customer-value-centric approach which helps teams deliver value to their customers faster and with fewer problems?
Which of the following is the MOST effective practice for tracking organizational assets when removed from the premises?
A third-party vendor is procured to conduct a non-financial audit. Which report evaluates the effectiveness of the controls?
The master schedule is an Important tool in the sales and operations planning (S&OP) process because it:
Which of the following tools is used to evaluate the impact that a production plan has on capacity?
An attacker was able to identify an organization’s wireless network, collect proprietary network resource information, and capture several user credentials. The attacker then used that information to conduct a more sophisticated and impactful attack against the organization. Which method did the attacker MOST likely use to gather the initial information?
In preparing for a facility location decision, proximity to suppliers would be classified as which kind of criteria?
The Business Continuity Plan (BCP) has multiple components. The information security plan portion must prioritize its efforts. Which 3 aspects of information security MUST be prioritized?
An organization wants to ensure the security of communications across its environment. What is the BEST way to provide confidentiality of data from handheld wireless devices to the internal network?
A newer automotive supplier has not fully developed its information technology (IT) systems. The supplier has Just received a contract from a large automotive manufacturer which requires the supplier to use electronic data interchange (EDI) transactions for receiving orders, sending advance ship notices (ASNs), and receiving invoice payments. What strategy can the supplier adopt to immediately meet the EDI requirements?
Which of the following is a threat modeling methodology used for accessing threats against applications and Operating Systems (OS)?
During a threat modeling exercise using the Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege (STRIDE) framework, it was identified that a web server allocates a socket and forks each time it receives a request from a user without limiting the number of connections or requests.
Which of the following security objectives is MOST likely absent in the web server?
How would blockchain technology support requirements for sharing audit information among a community of organizations?
To ensure the quality of its newly developed software, an organization is aiming to deploy an automated testing tool that validates the source code. What type of testing BEST supports this capability?
An organization recently created a new accounting department, and that department is critical in the event of a disaster for the operations to continue. Which steps should the organization take to create a Business Continuity Plan (BCP)?
A startup organization has been growing rapidly and is planning to open a new office on another continent. Until infrastructure for the new office can be built, the organization is setting up remote access to the existing network. Which of the following is the MOST important secure implementation to complete during the expansion?
Which of the following are compromised in an untrusted network using public key cryptography when a digitally signed message is modified without being detected?
In Company XYZ, transaction-costing capability has been Integrated into the shop floor reporting system. A batch of 20 units was started in production. At the fourth operation, 20 units are reported as complete. At the fifth operation, 25 units are reported as complete. When all operations are complete, 20 units are checked into the stockroom. If the error at the fifth operation is undetected, which of the following conditions will be true?
Which of the following situations is most likely to occur when using a push system?
A security engineer needs to perform threat modeling on a microprocessor design for an Internet of Things (IoT) application. Using the MITRE Common Weakness Enumeration (CWE) catalog for hardware, a risk analysis is performed. What kind of threat modeling approach would be BEST to identify entry points into the system based on motivation?
Network Access Control (NAC) is used to perform what function for computers joining the network?
An organization wants to implement Zero Trust (ZT). The Information Technology (IT) department is already using Multi-Factor Authentication (MFA) and Identity and Access Management (IAM). Which of the following would be the BEST solution for the organization to implement in order to have a ZT network?
Which of the following is the fundamental difference between finite loading and other capacity planning approaches?
Which of the following factors typically would distort a sales forecast that is based solely on shipment history?
When conducting a vulnerability test using a scanner tool, which unintended consequence can occur?
An organization is considering options to outsource their Information Technology (IT) operations. Although they do not sell anything on the Internet, they have a strong requirement in uptime of their application. After evaluating the offerings received by the Cloud Service Provider (CSP), the IT manager decided it was mandatory to develop processes to continue operations without access to community or public cloud-based applications. Which of the following arguments MOST likely led the IT manager to make this decision?
An organization has been struggling to improve their security posture after a recent breach.
Where should the organization focus their efforts?
The Chief Information Security Officer (CISO) for an international organization with offices operating globally has been tasked with developing a new data encryption policy that can be applied to all areas of the business. What is the MOST important factor that must be considered?
A healthcare organization is preparing an exercise test plan of its Disaster Recovery Plan (DRP) for the Electronic Medical Record (EMR) application. The Business Continuity (BC) analyst is reviewing the requirements of the DRP. The EMR must provide basic charting services within 4 hours, must not lose more than 15 minutes of data, and must be fully functional within 12 hours. At the completion of the exercise, the analyst is preparing a lessons learned report and notes that the EMR was available after 3 hours and 25 minutes of data was lost. Which PRIMARY requirement needs to be addressed because of the exercise?
Which of the following trade-offs should be evaluated when determining where to place inventory in a multi-echelon supply chain network?
Which of the following inventory management techniques is most responsive to changes in demand levels?
Which of the following is the MOST significant flaw when using Federated Identity Management (FIM)?
An organization is implementing Zero Trust Network Access (ZTNA) and needs a strategy to measure device trust for employee laptops. Which measurement strategy is BEST suited and why?
Which of the following should recommendations from a Plan Of Action And Milestones (POA&M) be based on?
A security team member is assessing an organization’s backup strategy that follows the 3-2-1 rule. How many different types of media should they inspect to validate?
An executive is approved to travel to a high-risk country. What is the BEST action the organization can take to ensure the executive’s safety and security?
Which of the following is the BEST option for a security director to use in order to mitigate the risk of inappropriate use of credentials by individuals with administrative rights?
In a rapidly changing business environment, a primary advantage of an effective customer relationship management (CRM) program is:
A planner has chosen to increase the order point for a raw material. Which of the following costs is most likely to increase?
What is the FIRST element that must be evaluated in a security governance program?
A web developer was recently asked to create an organization portal that allows users to retrieve contacts from a popular social media platform using Hypertext Transfer Protocol Secure (HTTPS). Which of the following is BEST suited for authorizing the resource owner to the social media platform?
What General Data Protection Regulation (GDPR) principle says that data should be collected lawfully and with the person’s consent?
In which of the following environments is capable-to-promise (CTP) more appropriate than available-to-promise (ATP)?
Which of the following planes directs the flow of data within a Software-Defined Networking (SDN) architecture?
Which of the following BEST describes how an Application Programming Interface (API) gateway fits into an application architecture?
An organization has a legacy application used in production. Security updates are no longer provided, which makes the legacy application vulnerable. The legacy application stores Social Security numbers and credit card numbers. Which actions will BEST reduce the risk?
A security practitioner has been asked to investigate the presence of customer Personally Identifiable Information (PII) on a social media website. Where does the practitioner begin?
A company decided not to pursue a business opportunity In a foreign market due to political Instability and currency fluctuations. Which risk control strategy did this business utilize?
Which technology is BEST suited to establish a secure communications link between an individual’s home office and the organization’s Local Area Network (LAN)?
An organization is migrating its access controls to a certificate-based authentication system.
What will need to be established to verify the identity of all users connecting to the network before rolling out the system?
Which of the following BEST describes web service security conformance testing as it relates to web services security testing?
Additional requirements that are outside the original design are being added to a project, increasing the timeline and cost of the project.
What BEST describes the requirement changes that are happening?
Bad actors with little expense can easily make calls. Which social engineer strategy is a telecommunications ONLY risk concept?
The planned channels of Inventory disbursement from one or more sources to field warehouses are known as:
An information security professional is considering what type of classification label to place on an organization’s software code in order to implement proper access controls. The code is considered intellectual property data and would have a catastrophic impact to the organization if compromised or destroyed. Which of the following would be the MOST appropriate classification label to apply?
A large volume of outbound Transmission Control Protocol (TCP) connections from the same source Internet Protocol (IP) address was observed at a satellite office firewall. Which of the following is the MOST likely explanation?
Open Authorized (OAuth) has been chosen as technology to use across applications in the enterprise. Which of the following statements is TRUE about an OAuth token?
What is an important countermeasure to consider when hardening network devices and servers to reduce the effectiveness of unauthorized network scanning?
Which of the following factors is the MOST important consideration for a security team when determining when determining whether cryptographic erasure can be used for disposal of a device?
Which of the following terms below BEST describes the measure of confidence that the security features, practices, procedures, and architecture of an information system accurately mediates and enforces security policy?
A company that uses concurrent engineering is likely to experience which of the following outcomes in the first period of a product's life cycle?
Which of the following statements best characterizes enterprise resources planning (ERP) systems?
Which threat modeling methodology is focused on assessing risks from organizational assets?
Capacity requirements planning (CRP) is applicable primarily In companies operating In an environment where:
Which of the following is the BEST solution to implement to mitigate the risk of data breach in the event of a lost or stolen mobile device?
Which of the following environments is most suitable for the use of kanban systems?
Which of the following BEST represents a security benefit of Software-Defined Networking (SDN)?
An independent risk assessment determined that a hospital's existing policies did not have a formal process in place to address system misuse, abuse, or fraudulent activity by internal users. Which of the following would BEST address this deficiency in the Corrective Action Plan?
Which of the following mechanisms are PRIMARILY designed to thwart side channel attacks?


