Upon submission of an assessment object by the assessor, how many days does HITRUST take to either accept or reject the assessment?
For the maturity levels "Measured" and "Managed," any score above 50% requires the following supporting documentation. (Select all that apply)
The Subscribers Comments field should be populated with the rationale for any requirement statement marked not-applicable (N/A).
The HITRUST CSF applies to covered information across all transmission and storage methods.
A pharmacy that accepts Medicare/Medicaid and also takes credit cards should include which regulatory factors in their assessment?
If an organization requires an assessment with the highest level of assurance, which assessment type should they choose?
MyCSF analytics can be used to visualize data within an assessment object as well as across all assessment objects within an organization.
The AI Risk Assessment compliance factor is used to obtain the HITRUST AI Security Certification. [0007]
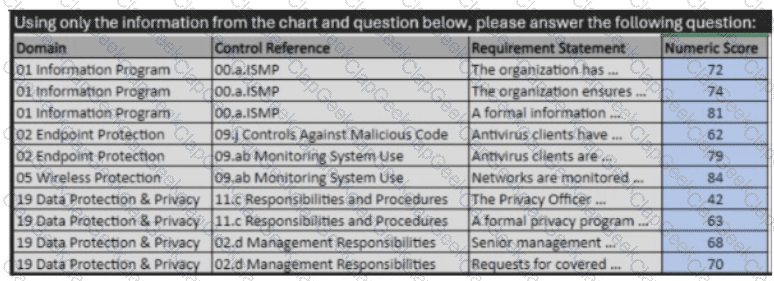
If a requirement statement beginning with "The Privacy Officer..." scored a 50 instead of 42, would the overall assessment achieve certification?
The concept of HITRUST CSF risk levels was adapted from what security standard?
Select the four general risk factor categories used when scoping r2 assessments.
A sample of laptops is being selected to ensure AV software has been properly installed/configured. Where should the population be pulled from? [0173]
It is possible to test only privacy-related requirements to obtain a HITRUST privacy certification.
Which of the following are appropriate types of inheritance within MyCSF? (Select all that apply) [0061]
After completion of a Validated Assessment, all remediated CAPs can be removed from the final report.
What characteristics would allow grouping of multiple like components together?
What is an example of a secondary scoping component that could be related to the requirement statement that reads:
"The organization destroys (e.g., disk wiping, degaussing, shredding, disintegration, grinding, incineration, pulverization, or melting) media containing sensitive information when it is no longer needed for business or legal reasons."
How would you score implemented coverage for one system if two of four evaluative elements were in place?
Gaps with required CAPS must have documented remediation plans within the assessment object before submission to HITRUST QA.
Measured and Managed Maturity Levels can be scored for some, but not all, requirements in an r2 assessment object.
During a HITRUST Assessment, what percentage of External Assessor hours must be performed by a CCSFP?
For an r2 assessment, to obtain a Validated Report with Certification, each domain must score at least a 71 or higher.
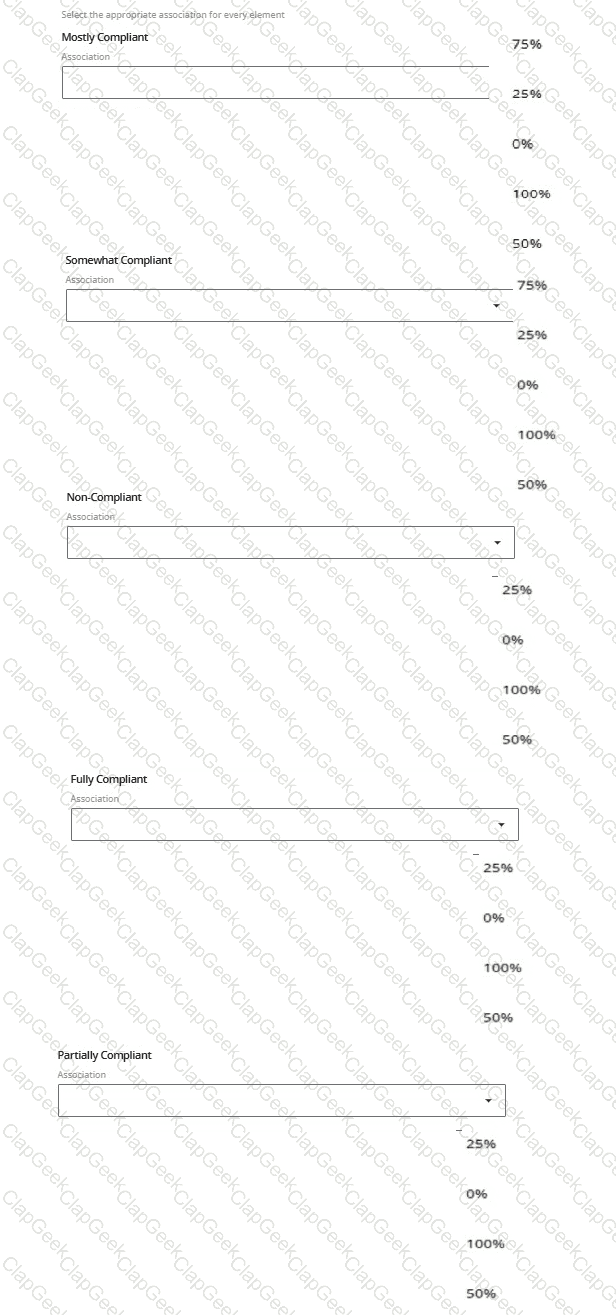
Enter the value assigned to each of the following scoring levels on the HITRUST Scoring Rubric.
If an organization has a policy against uploading sensitive data to third parties, what option would facilitate providing evidence to the HITRUST QA team to support maturity level scoring?
Using only the information from the chart and question below, please answer the following question:
Domain
Control Reference
Requirement Statement
Numeric Score
01 Information Program
00.a.ISMP
The organization has...
72
01 Information Program
00.a.ISMP
The organization ensures...
74
01 Information Program
00.a.ISMP
A formal information...
81
02 Endpoint Protection
09.j Controls Against Malicious Code
Antivirus clients have...
62
02 Endpoint Protection
09.ab Monitoring System Use
Antivirus clients are...
79
05 Wireless Protection
09.ab Monitoring System Use
Networks are monitored...
84
19 Data Protection & Privacy
11.c Responsibilities and Procedures
The Privacy Officer...
42
19 Data Protection & Privacy
11.c Responsibilities and Procedures
A formal privacy program...
63
19 Data Protection & Privacy
02.d Management Responsibilities
Senior management...
68
19 Data Protection & Privacy
02.d Management Responsibilities
Requests for covered...
70
Assuming no Implementation score achieved 100% on any requirement statement and assuming all Control References are required for certification, this assessment will contain a required Corrective Action Plan (CAP)? [0193]
When an assessor has completed reviewing and agreeing with Requirement Statement scoring, the assessor must save the results. This action will mark the Requirement Statement as "Assessor Review Complete". [0049]
How large would the sample size be for a manual control with a population of 56 unique items?
What are HITRUST Assurance Advisories designed to provide? (Select all that apply) [0051]
When testing, can you sample across a population of ungrouped primary components within an assessment's scope?


