Cindy just joined a company's IT Audit Department and needs CyberArk Identity access to perform her daily job activities.
Which administrative right(s) should she be assigned to match her job requirement?
A user wants to install the CyberArk Identity mobile app by using a QR code.
Arrange the steps to do this in the correct sequence.

Which 2FA/MFA options can fulfill the "Something you are" requirement? (Choose two.)
Your team is deploying endpoint authentication onto the corporate endpoints within an organization. Enrollment details include when the enrollment must be completed, and the enrollment code was sent out to the users. Enrollment can be performed in the office or remotely (without the assistance of an IT support engineer). You received feedback that many users are unable to enroll into the system using the enrollment code.
What can you do to resolve this? (Choose two.)
You get the following error: "Not Authorized. You do not have permission to access this feature".
What is most likely the cause of the error?
An organization previously allowed users to add their personal apps on the Identity User Portal. This will soon be disabled due to policy changes.
What is the impact to the users for personal apps previously added to the User Portal?
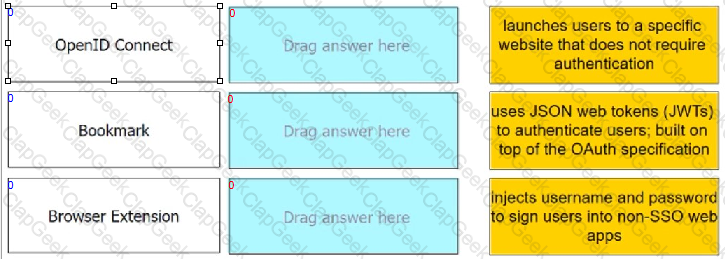
Match each Web App Connector to the phrase that best describes its service offering.
As part of an ongoing incident investigation, you want to examine all data/events that are relevant to updating user profiles.
Which dataset from the UBA portal should you use?
When logging on to the User Portal, which authentication methods can enable the user to bypass authentication rules and default profile? (Choose two.)
Your organization wants to implement passwordless authentication for business critical web applications. CyberArk Identity manages access to these applications.
What can you do to facilitate the enforcement of this passwordless authentication initiative? (Choose two.)


