An organization requires that BYOD devices be enrolled in Systems Manager before they gain access to the network. Part of the enrollment includes pushing out the corporate SSID preshared key, corporate email settings, and some business-sensitive PDFs. When a user leaves the organization, which Systems Manager feature allows the removal of only the MDM-delivered content from the user's device?
When an SSID is configured with Sign-On Splash page enabled, which two settings must be configured for unauthenticated clients to have full network access and not be allow listed? (Choose two.)
Company iPads are enrolled in Systems Manager without supervision, and profiles are pushed through Systems Manager.
Which outcome occurs when a user attempts to remove the “Meraki Management” profile on an iPad?
Which VLAN is used to source pings across the site-to-site VPN when using the MX Live tools?
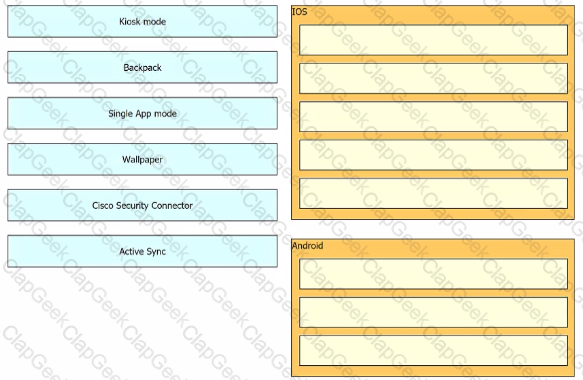
Drag and drop the settings from the left onto the OS system or systems that support it on the right Settings can be used more than once.
Refer to the exhibit.
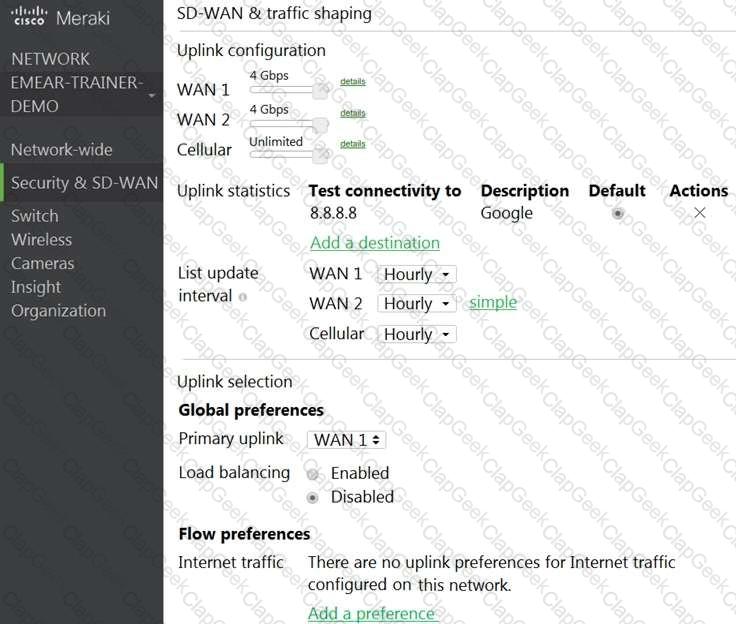
Which two actions are required to optimize load balancing asymmetrically with a 4:1 ratio between links? (Choose two.)
What is out of scope when considering the Best practices for high-density wireless designs?
What is the role of the Meraki Dashboard as the service provider when using SAML for single sign-on to the Dashboard?
Which configuration step is necessary when automatic updating is required of iOS apps provisioned through Systems Manager that are found in the App Store?
Refer to the exhibit.
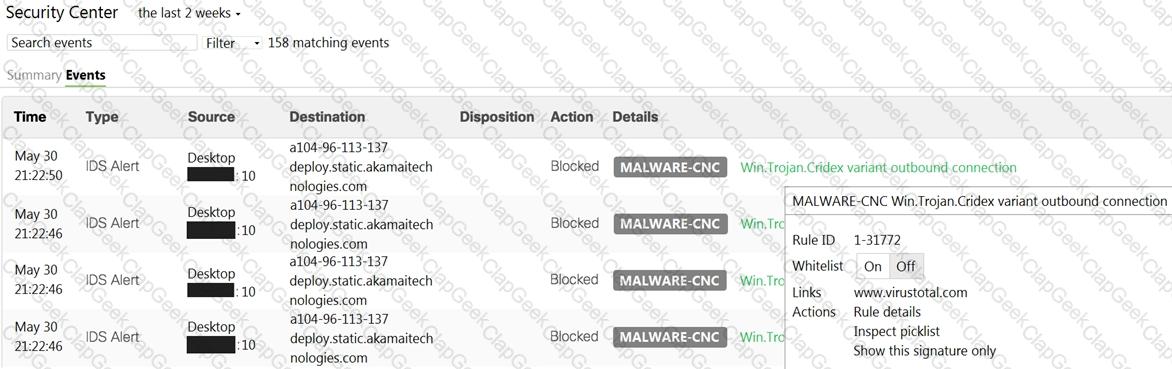
Which IDS/IPS mode is the MX Security Appliance configured for?
A Cisco Meraki MX security appliance is trying to route a packet to the destination IP address of 172.18.24.12. Which routes contained in its routing table does it select?
What are two methods of targeting and applying management profiles to System Manager clients? (Choose two.)
Refer to the exhibit.

For an AP that displays this alert, which network access control method must be in use?
A Cisco Meraki MV camera is monitoring an office and its field of vision currently captures work desks and employee computer screens. However, recording employee computer screens is prohibited by local regulation.
Which feature in Dashboard can be used to preserve the current position of the camera while also meeting regulation requirements?


