A customer asks you to perform a high-level review of their upcoming WAN refresh for remote sites. The review is specially focused on their retail store operations consisting of 500+ locations connected via multipoint IPsec VPN solution. Which routing protocol would be valid but would also be the most restrictive for the expansion of this deployment model?
Which mechanism enables small, unmanaged switches to plug into ports of access switches without risking switch loops?
Cost is often one of the motivators for a business to migrate from a traditional network to a software-defined network. Which design decision is directly influenced by CAPEX drivers?
Company XYZ is running BGP as their routing protocol. An external design consultant recommends that TCP Path MTU Discovery be enabled. Which effect will this have on the network?
As a network designer, you need to support an enterprise with hundreds of remote sites connected over a single WAN network that carries different types of traffic, including VoIP, video, and data applications. Which of the following design considerations will not impact design decision?
Company XYZ is running OSPF in their network. They have merged with another company that is running EIGRP as the routing protocol. Company XYZ now needs the two domains to talk to each other with redundancy, while maintaining a loop-free environment. The solution must scale when new networks are added into the network in the near future. Which technology can be used to meet these requirements?
Which three tools are used for ongoing monitoring and maintenance of a voice and video environment? (Choose three.)
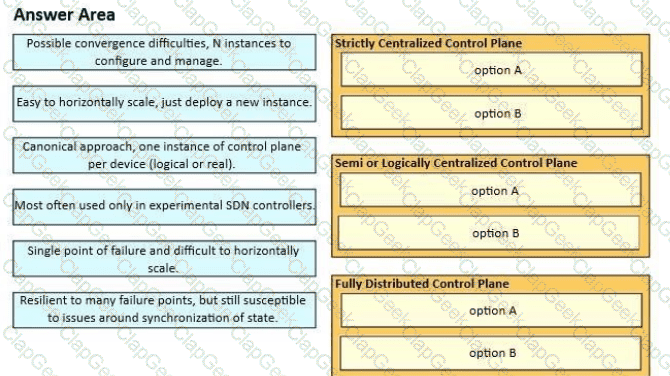
Network operators have many options available, from fully centralized to fully distributed control planes, and each approach has its own set of characteristics. Drag and drop the characteristics from the left onto the corresponding approach on the right.
What are two examples of components that are part of an SDN architecture? (Choose two.)
A business customer deploys workloads in the public cloud but now faces governance issues related to IT traffic flow and data security. Which action helps identify the issue for further resolution?
Drag and drop the QoS technologies from the left onto the correct capabilities on the right

A product manufacturing organization is integrating cloud services into their IT solution. The IT team is working on the preparation phase of the implementation approach, which includes the Define Strategy step. This step defines the scope of IT, the application, and the service. What is one topic that should be considered in the Define Strategy step?
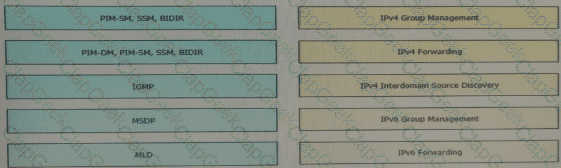
Drag and drop the multicast protocols from the left onto the current design situation on the right.
Company XYZ is running a redundant private WAN network using OSPF as the underlay protocol. The current design accommodates for redundancy in the network, but it is taking over 30 seconds for the network to reconverge upon failure. Which technique can be implemented in the design to detect such a failure in a subsecond?
Which aspect of BGP-LS makes it scalable in large networks when multiarea topology information must be gathered?
QUESTION 69 Refer to the exhibit. AJI links are P2P Layer 3. A high availability application is synchronizing data between host A and host B. To increase chance of delivery the same data is sent twice from host A on two different NICs toward the two NICs on host B.
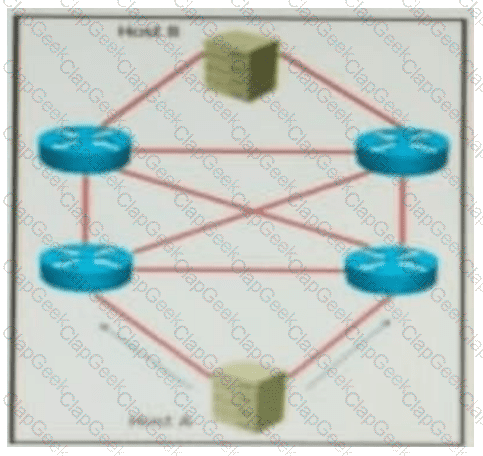
Refer to the exhibit. All links are P2P Layer 3. A high availability application is synchronizing data between Host A and Host B. To increase the chance of delivery, the same data is sent twice from Host A on two different NICs toward the two NICs on Host B.
Which solution must be deployed in the network to ensure that any failure in the network does not trigger data loss on Host B?
Which development model is closely associated with traditional project management?
Which two statements explain the operation of BFD asynchronous mode? (Choose two.)
Company XYZ must design a strategy to protect their routers from DoS attacks, such as traffic destined to the router's own route processor, using separate control plane categories. Which two capabilities can be used to achieve this requirement? (Choose two.)
Which security architecture component offers streamlined security operations, ease of use, and visibility across all network security elements, independent of location or form factor?
Refer to the exhibit.
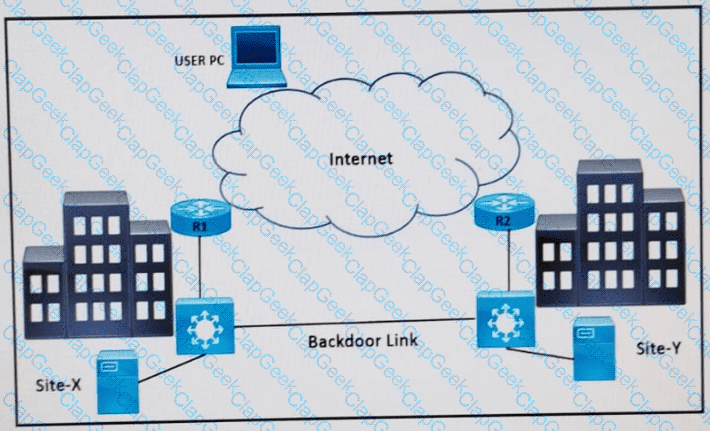
Refer to the exhibit. Two data center sites (X and Y) connect to the Internet and each other using a backdoor link. Both advertise the same IP prefix (100.75.10.0/23) to the Internet. Firewalls are behind R1 and R2.
Problem: When users attempt to reach 100.75.10.0/23, the return traffic is routed to Site-Y, regardless of where the session originated. This results in asymmetric traffic and potentially broken sessions due to firewall behavior.
Which design resolves the issue?
Which solution component helps to achieve comprehensive threat protection and compliance for migration to multicloud SDX architectures?
Company XYZ is running SNMPv1 in their network and understands that it has some flaws. They want to change the security design to implement SNMPv3 in the network. Which network threat is SNMPv3 effective against?
Which two application requirements are mandatory for traffic to receive proper treatment when placed in the priority queue? (Choose two.)
Company XYZ runs OSPF in their network. A design engineer decides to implement hot-potato routing architecture. How can this implementation be achieved?
A financial company requires that a custom TCP-based stock-trading application be prioritized over all other traffic for the business due to the associated revenue. The company also requires that VoIP be prioritized for manual trades. Which directive should be followed when a QoS strategy is developed for the business?
A company plans to use BFD between its routers to detect a connectivity problem inside the switched network. An IPS is transparently installed between the switches. Which packets should the IPS forward for BFD to work under all circumstances?
SDWAN networks capitalize the usage of broadband Internet links over traditional MPLS links to offer more cost benefits to enterprise customers. However, due to the insecure nature of the public Internet, it is mandatory to use encryption of traffic between any two SDWAN edge devices installed behind NAT gateways. Which overlay method can provide optimal transport over unreliable underlay networks that are behind NAT gateways?
A banking customer determines that it is operating POS and POI terminals that are noncompliant with PCI DSS requirements, as it is running TLSv1.0. The customer plans to migrate the terminals to TLSv1.2. What are two requirements to complete the migration? (Choose two.)
SDN emerged as a technology trend that attracted many industries to move from traditional networks to SDN. Which challenge is solved by SDN for cloud service providers?
An Agile for Infrastructure transition often means dismantling traditional IT hierarchies and rebuilding it to align with business objectives and workflows. Organizations are seeing the benefits of using automation tools in the network such as faster, more efficient, and more effective delivery of products and services. Which two components help increase overall productivity and improve company culture? (Choose two.)
A customer migrates from a traditional Layer 2 data center network into a new SDN-based spine-and-leaf VXLAN EVPN data center within the same location. The networks are joined to enable host migration at Layer 2. Which activity should be completed each time a legacy network is migrated?
Identity and access management between multiple users and multiple applications has become a mandatory requirement for Company XYZ to fight against ever-increasing cybersecurity threats. To achieve this, federated identity services have been deployed to provide Single Sign-On and Multi-Factor Authentication. Which protocol can be used by Company XYZ to provide authentication and authorization services?
Company XYZ wants to prevent switch loops caused by unidirectional point-to-point link conditions on Rapid PVST+ and MST. Which technology can be used in the design to meet this requirement?
Company XYZ network runs IPv4 and IPv6 and they want to introduce a multidomain, multicast-based network. The new design should use a flavor of PIM that forwards traffic using SPT. Which technology meets this requirement?
In an OSPF network with routers connected together with Ethernet cabling, which topology typically takes the longest to converge?
If the desire is to connect virtual network functions together to accommodate different types of network service connectivity, what must be deployed?
What is the most important operational driver in building a resilient and secure modular network design?
You are designing the QoS policy for a company that is running many TCP-based applications. The company is experiencing tail drops for these applications. The company wants to use a congestion avoidance technique for these applications. Which QoS strategy can be used?
What are two primary design constraints when a robust infrastructure solution is created? (Choose two.)
Refer to the exhibit.
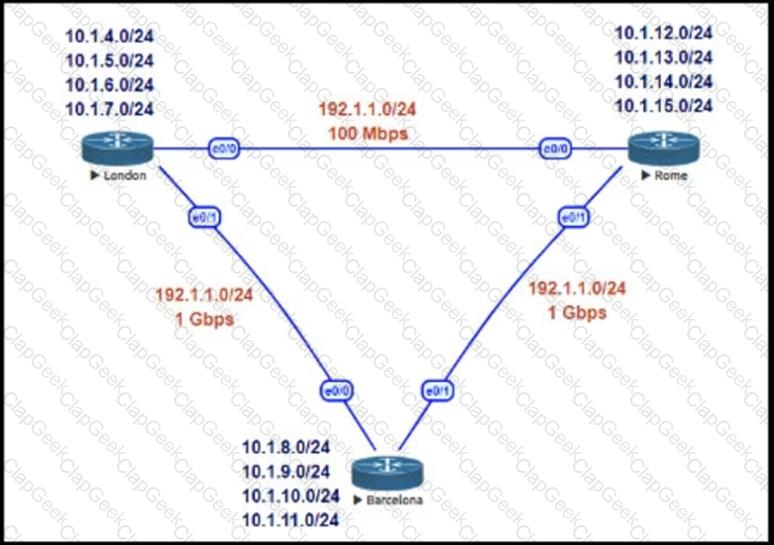
This network is running EIGRP as the routing protocol and the internal networks are being advertised in EIGRP. Based on the link speeds, all traffic between London and Rome is getting propagated via Barcelona and the direct link between London and Rome is not being utilized under normal working circumstances. The EIGRP design should allow for efficiency in the routing table by minimizing the routes being exchanged. The link between London and Rome should be utilized for specific routes. Which two steps accomplish this task? (Choose two.)
A customer migrates from a traditional Layer 2 data center network into a new SDN-based spine-and-leaf VXLAN EVPN data center within the same location. The networks are joined to enable host migration at Layer 2. What is the final migration step after hosts have physically migrated to have traffic flowing through the new network without changing any host configuration?
Which two mechanisms avoid suboptimal routing in a network with dynamic mutual redistribution between multiple OSPFv2 and EIGRP boundaries? (Choose two.)
An architect prepares a network design for a startup company. The design must meet business requirements while the business grows and divests due to rapidly changing markets. What is the highest priority in this design?
A company requires an RPO of less than 10 seconds to ensure business continuity. Which technology should be deployed?
Software-defined networking architecture is used for cost-effective, adaptable, and easily manageable applications. In which two software-defined networks is SDN commonly used? (Choose two.)
You are designing the routing design for two merging companies that have overlapping IP address space. Which of these must you consider when developing the routing and NAT design?
Hybrid cloud computing allows organizations to take advantage of public and private cloud models. Which best practice should organizations follow to ensure data security in the private cloud?
What is a country-specific requirement that data is subject to the laws of the country in which it is collected or processed and must remain within its borders?
Refer to the exhibit.
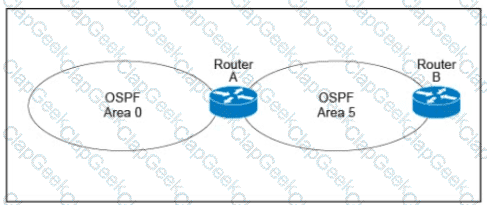
A customer runs OSPF with Area 5 between its aggregation router and an internal router. When a network change occurs in the backbone, Area 5 starts having connectivity issues due to the SPF algorithm recalculating an abnormal number of times in Area 5. You are tasked to redesign this network to increase resiliency on the customer network with the caveat that Router B does not support the stub area. How can you accomplish this task?
A multicast network is using Bidirectional PIM. Which two combined actions achieve high availability so that two RPs within the same network can act in a redundant manner? (Choose two)
Company XYZ was not satisfied with the reconvergence time OSPF is taking. BFD was implemented to try to reduce the reconvergence time, but the network is still experiencing delays when having to reconverge. Which technology will improve the design?
What are two examples of business goals to be considered when a network design is built? (Choose two.)
Company XYZ needs advice in redesigning their legacy Layer 2 infrastructure. Which technology should be included in the design to minimize or avoid convergence delays due to STP or FHRP and provide a loop-free topology?
Which two aspects are considered when designing a dual hub dual DMVPN cloud topology? (Choose two.)
What is a disadvantage of the traditional three-tier architecture model when east-west traffic between different pods must go through the distribution and core layers?
How can EIGRP topologies be designed to converge as fast as possible in the event of a point-to-point link failure?
Company XYZ wants to secure the data plane of their network. Which two technologies can be included in the security design? (Choose two)
What is a disadvantage of the traditional three-tier architecture model when east-west traffic between different pods must go through the distribution and core layers?
You are designing a new Ethernet-based metro-area network for an enterprise customer to connect 50 sites within the same city. OSPF will be the routing protocol used. The customer is primarily concerned with IPv4 address conservation and convergence time. Which two combined actions do you recommend? (Choose two)
When planning their cloud migration journey, what is crucial for virtually all organizations to perform?
Refer to the exhibit.
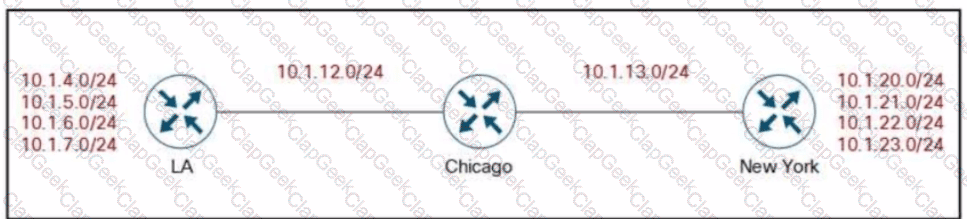
Company XYZ’s BGP topology is as shown in the diagram. The interface on the LA router connected toward the 10.1.5.0/24 network is faulty and is going up and down, which affects the entire routing domain. Which routing technique can be used in the routing policy design so that the rest of the network is not affected by the flapping issue?
A network engineering team is in the process of designing a lab network for a customer demonstration. The design engineer wants to show that the resiliency of the MPLS Traffic Engineering Fast Reroute solution has the same failover/failback times as a traditional SONET/SDH network (around 50 msec). In order to address both link failure and node failure within the lab topology network, which type of the MPLS TE tunnels must be considered for this demonstration?
Which three Cisco products are used in conjunction with Red Hat to provide an NFVi solution? (Choose three.)
A European national bank considers migrating its on-premises systems to a private cloud offering in a non-European location to significantly reduce IT costs. What is a primary factor prior to migration?
Company XYZ is designing the IS-IS deployment strategy for their multiarea IS-IS domain. They want IS-IS neighbor relationships minimized on each segment and the LSDB size optimized. Which design can be used?
Company XYZ is revisiting the security design for their data center because they now have a requirement to control traffic within a subnet and implement deep packet inspection. Which technology meets the updated requirements and can be incorporated into the design?
An enterprise has identified these causes for inefficient CAPEX spending:
CAPEX planning is driven by technology and not by business objectives.
The CAPEX planning team lacks the data it needs to perform due diligence tasks.
The organizational structure lacks sufficient accountability and incentives.
Which corporate cultural change contributes to improving the effectiveness of CAPEX spending?
A healthcare provider discovers that protected health information of patients was altered without patient consent. The healthcare provider is subject to HIPAA compliance and is required to protect PHI data. Which type of security safeguard should be implemented to resolve this issue?
Which issue poses a challenge for security architects who want end-to-end visibility of their networks?
When a company network architect is working on a new network design, they are expected to ensure that business requirements and technical aspects are factored in, but often there are other factors that come into play as well. Which non-business constraint must also be considered throughout the design phase?
A network architect is designing a policy where database applications access the internet directly, while other traffic routes through the data center, with dynamic path switching based on performance. Which solution meets these requirements?
The network designer needs to use GLOP IP addresses to make them unique within their ASN. Which multicast address range will be considered?
Which protocol does an SD-Access wireless Access Point use for its fabric data plane?
Which three elements help network designers to construct secure systems that protect information and resources (such as devices, communication, and data) from unauthorized access, modification, inspection, or destruction? (Choose three.)
Refer to the exhibit.
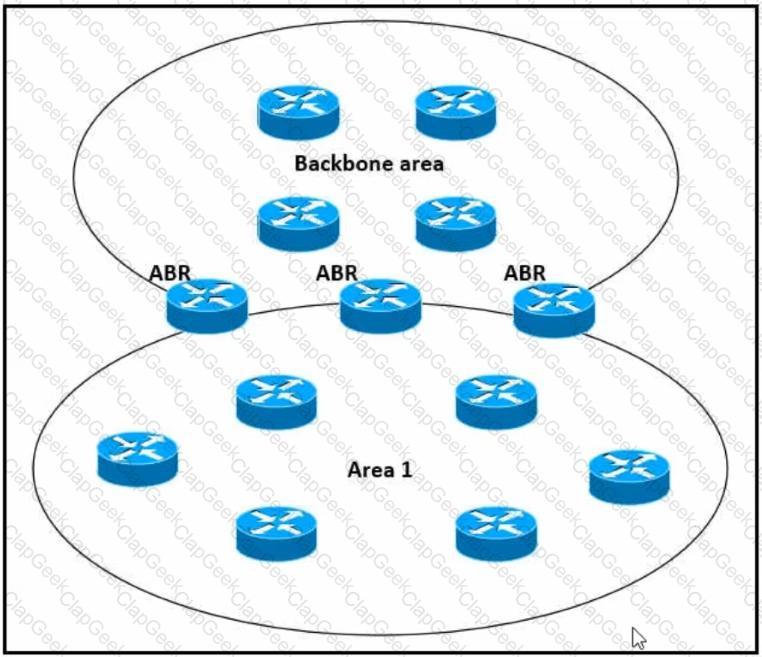
Which impact of using three or more ABRs between the backbone area and area 1 is true?
A legacy enterprise is using a Service Provider MPLS network to connect its head office and branches. They want to extend the existing IP CCTV network to a new branch without routing changes or IP address changes. What is the best approach?
Which architecture does not require an explicit multicast signaling protocol, such as PIM or P2MP, to signal the multicast state hop-by-hop, but instead uses a link state protocol to advertise the multicast forwarding state?
Company XYZ wants to deploy OSPF. The design plan requires that two OSPF networks be mutually redistributed at multiple locations and ensure end-to-end connectivity to all of the company's networks. Which technology can be used to fulfill the requirements while avoiding the creation of routing loops?
A business invests in SDN and develops its own SDN controller that, due to budget constraints, runs on a single controller. The controller actively places an exclusive lock on the configuration of the devices to ensure it is the only source of changes to the environment. What is the result if the controller fails?
You have been tasked with designing a data center interconnect to provide business continuity. You want to encrypt the traffic over the DCI using IEEE 802.1AE MACsec to prevent the deployment of any firewall or IPS. Which two interconnect technologies support MACsec? (Choose two.)
VPLS is implemented in a Layer 2 network with 2000 VLANs. What is the primary concern to ensure successful deployment of VPLS?
Which two factors must be considered for high availability in campus LAN designs to mitigate concerns about unavailability of network resources? (Choose two.)
Company XYZ wants to redesign the Layer 2 part of their network to use all uplinks for increased performance, support host reachability with conversational learning, and avoid port-channels. Which other technique can be used?
You want to split an Ethernet domain in two.
Which parameter must be unique in this design to keep the two domains separated?
Which two foundational aspects of IoT are still evolving and being worked on by the industry at large? (Choose two)
Which two design options are available to dynamically discover the RP in an IPv6 multicast network? (Choose two)
Refer to the exhibit.
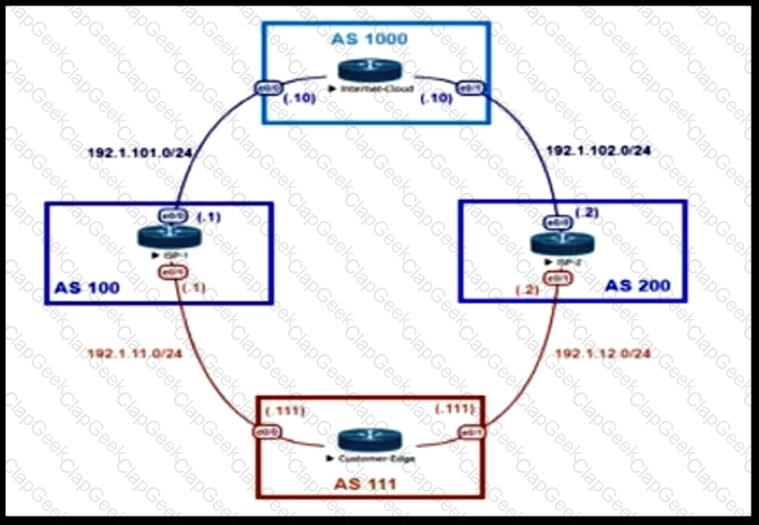
An engineer is designing the traffic flow for AS 111. Traffic from AS 111 should be preferred via AS 100 for all external routes. A method must be used that only affects AS 111. Which BGP attributes are best suited to control outbound traffic?
Which two statements describe the usage of the IS-IS overload bit technique? (Choose two.)
Router R1 is a BGP speaker with one peering neighbor over link "A". When link "A" fails, routing announcements are terminated, which results in the tearing down of the state for all BGP routes at each end of the link. What is this a good example of?
Company XYZ branch offices connect to headquarters using two links, MPLS and Internet. The company wants to design traffic flow so voice traffic uses MPLS and all other traffic uses either link, avoiding process switching. Which technique can be used?
A software-defined networking (SDN) controller learns network topology information by using BGP link-state sessions with the route reflectors of an MPLS-enabled network. The controller then uses the topology information to apply on-demand traffic policies to the network through a protocol that is supported from all Layer 3 routers. Each policy is represented as a RIB entry in the control plane of the router. Which SDN model has been implemented?
Refer to the table.
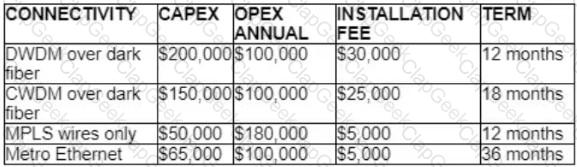
A customer investigates connectivity options for a DCI between two production data centers to aid a large-scale migration project. The migration is estimated to take 20 months to complete but might extend an additional 10 months if issues arise. All connectivity options meet the requirements to migrate workloads. Which transport technology provides the best ROI based on cost and flexibility?
What are two design constraints in a standard spine and leaf architecture? (Choose two.)
Company XYZ has two routing domains (EIGRP and OSPF). They want full reachability and need OSPF to see link costs added to external routes. How must redistribution be designed?


