Refer to the exhibit.
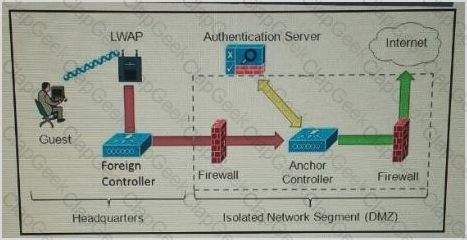
Which solution must be used to send traffic from the foreign wireless LAN controller to the anchor wireless LAN controller?
Which two options are considered risks or concerns when both the Internet and VPN service functions are on the same PE router? (Choose two.)
An operations engineer asks for your help with a new switching deployment. The engineer confirms that STP is enabled on an edge switch, and a particular port is connected to another switch. The switch is not receiving configuration BPDUs, although it appears that everything is functioning correctly in the network. What is the design explanation?
Your customer asks you to assist with their traffic policy design. They want to guarantee a minimum amount of bandwidth to certain traffic classes. Which technique would you advise them to implement?
Which three reasons to deploy an IDS sensor in promiscuous mode when you design a security solution are true? (Choose three.)
ACME Corporation is integrating IPv6 into their network, which relies heavily on multicast distribution of data. Which two IPv6 integration technologies support IPv6 multicast? (Choose two.)
The service provider that you work for wants to offer IPv6 internet service to its customers without upgrading all of its access equipment to support IPv6, which transition technology do you recommend?
Which option describes the fundamental design differences between an IP-based network design and a SAN-based?
Across a large WAN network, there will be new video traffic being distributed from a single source at any given time however, the video source might originate from different parts of the multicast domain at different times . Which multicast technology provides for this multicast traffic to be distributed with optimal path selection to the source?
Which solution prevents microloops from be formed during network convergence time?
Refer to the exhibit.
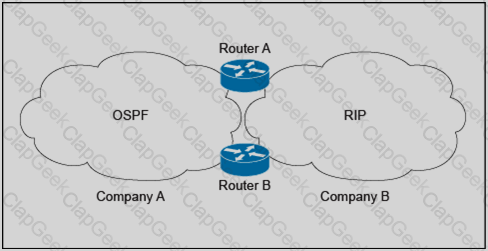
Company A is running a single-area OSPF, and Company B is running RIP as the IGP with no overlapping IP address spaces. Company A has just acquired Company B and both networks must be merged. Which three design components are recommended to guarantee connectivity and redundancy between the two networks? (Choose three.)
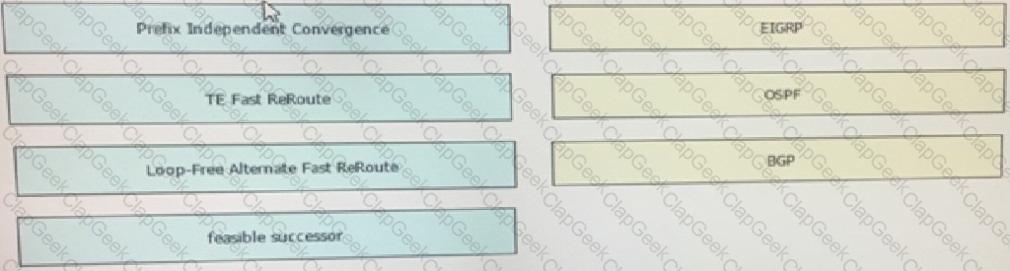
Drag and drop the Fast ReRoute mechanisms on the left to the correct routing protocols on the right. Not all options are used.
A company would like to distribute a virtual machine (VM) hosting cluster between three data centers with the capability to move VMs between sites. The connectivity between data centers is IP only and the new design should use the existing WAN. Which Layer 2 tunneling technology do you recommend?
Refer to the exhibit.
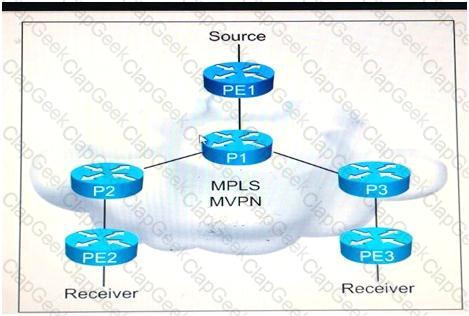
You are a network designer who is given these design requirements:
Multicast services must be provided for Layer 3 VPN customers
The same forwarding technology must be used as Layer 3 VPN unicast packets
Replication of multicast traffic is not allowed on the ingress PE
Which multicast VPN technology conforms to the design requirements?
Which technology , implemented on aggregation –edge nodes at the aggregation layer, provides per –tenant isolation at Layer 3 , with separate dedicated per-tenant routing and forwarding tables on the inside interfaces of firewall contexts?
A Company has these requirements for access to their wireless and wired corporate LANs using 802.1x
Clients devices that corporate assets and have joined the active directory domain are allowed access
Personal devices must be not allowed access
Clients and access servers must be mutually authenticated.
Which solution meets these requirements?
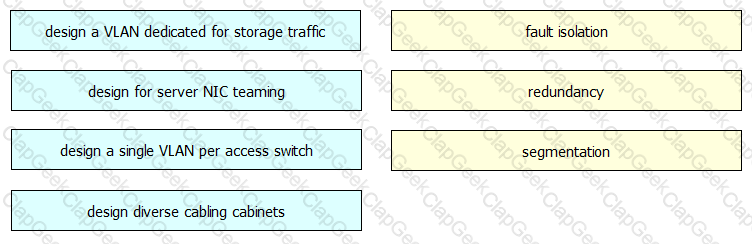
You are designing a new data center network. Drag and drop new data center requirements on the left into the appropriate design principle on the right.
You are hired to assist an enterprise customer to design their global WAN network. A protected DWDM circuit with disjoint fiber routes and guaranteed restoration times is ordered to connect two hub sites. Which option is a BFD design consideration in relation to protected DWDM?
Which major block is not included in the ETSI network Function Virtualization reference framework?
Refer to the exhibit.
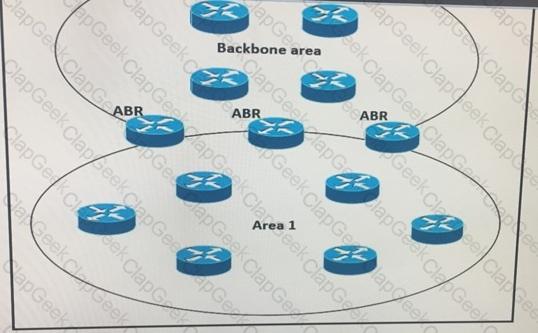
Which impact of using three or more ABRs between the backbone area and area 1 is true?
Which options do you investigate first when designing fast network convergence?
Refer to the Exhibit.
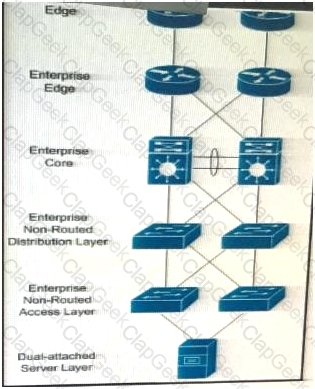
In which three Layers should you use nonstop Forwarding to reduce service impact in case of failure? (Choose three)
Which three network management requirements are common practices in network design? (Choose three)
A data center provider has designed a network using these requirements
Two data center sites are connected to the public internet
Both data centers are connected to different Internet providers
Both data centers are also directly connected with a private connection for the internal traffic can also be at this direct connection The data center provider has only /19 public IP address block
Under normal conditions, Internet traffic should be routed directly to the data center where the services are located. When one Internet connections fails to complete traffic for both data centers should be routed by using the remaining Internet connection in which two ways can this routing be achieved? (Choose two)
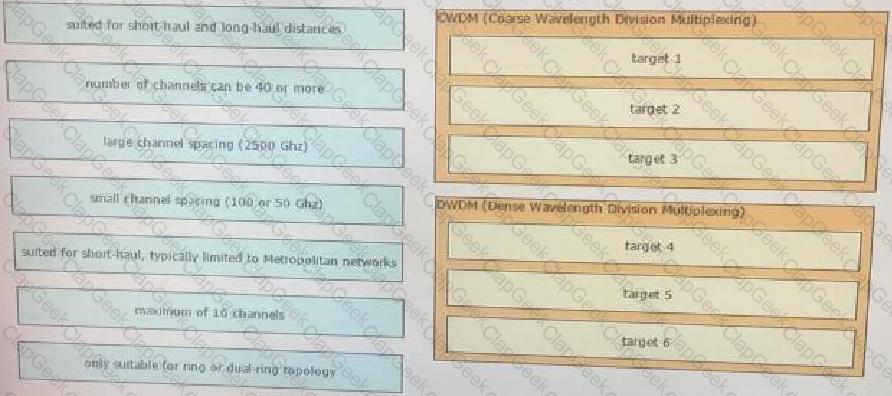
Drag and drop the optical technology design characteristics on the left to the correct optical technologies on the right. Not all options are used.
What is a design aspect regarding multicast transport for MPLS Layer 3 VPNs using the Rosen Draft implementation?
VPLS is implemented in a Layer 2 network with 2000 VLANs. Which must be the primary concern to ensure successful deployment of VPLS?
Which two options are IoT use cases that require the low-latency and high reliability that 5G networks provide? (Choose two)


