An organization is distributed across several sites. Each site is connected to the main HQ using site-to-site VPNs implemented using Secure Firewall Threat Defense. Which functionality must be implemented if the security manager wants to send SaaS traffic directly to the internet?
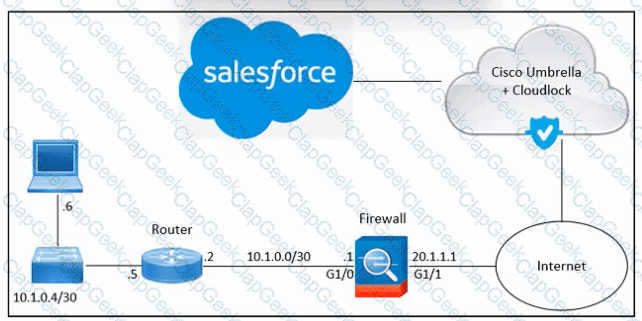
Refer to the exhibit. An engineer must enable access to Salesforce using Cisco Umbrella and Cisco Cloudlock. These actions were performed:
From Salesforce, add the Cloudlock IP address to the allow list
From Cloudlock, authorize Salesforce
However, Salesforce access via Cloudlock is still unauthorized. What should be done to meet the requirements?
An engineer configures trusted endpoints with Active Directory with Device Health to determine if an endpoint complies with the policy posture. After a week, an alert is received by one user, reporting problems accessing an application. When the engineer verifies the authentication report, this error is found:
"Endpoint is not trusted because Cisco Secure Endpoint check failed, Check user's endpoint in Cisco Secure Endpoint."
Which action must the engineer take to permit access to the application again?
An administrator received an incident report indicating suspicious activity of a user using a corporate device. The manager requested that the credentials of user user1@cisco.com be reset and synced via the Active Directory. Removing the account should be avoided and used for further investigation on data leak. Which configuration must the administrator apply on the Duo Admin Panel?
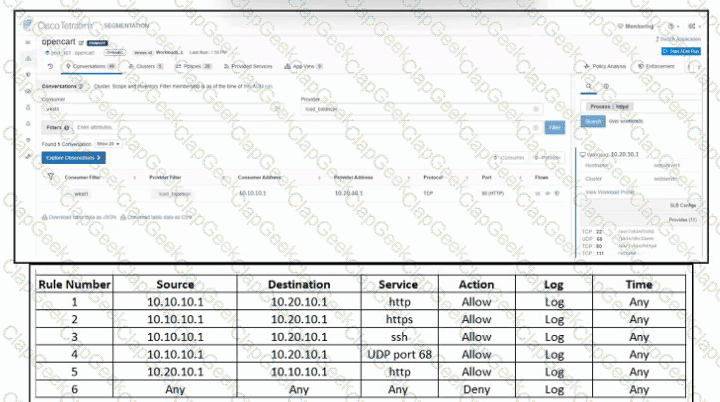
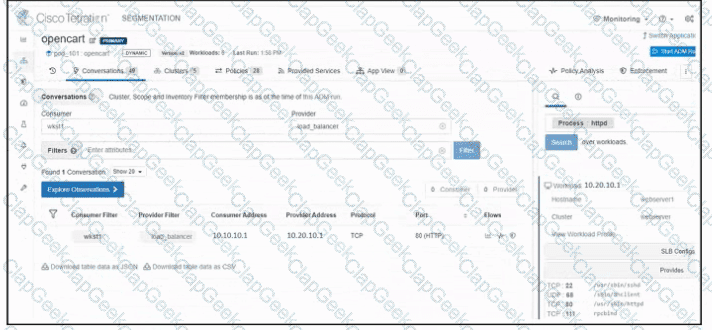
Refer to the exhibit. An engineer must create a firewall policy to allow web server communication only. The indicated firewall policy was applied; however, a recent audit requires that all firewall policies be optimized. Which set of rules must be deleted?
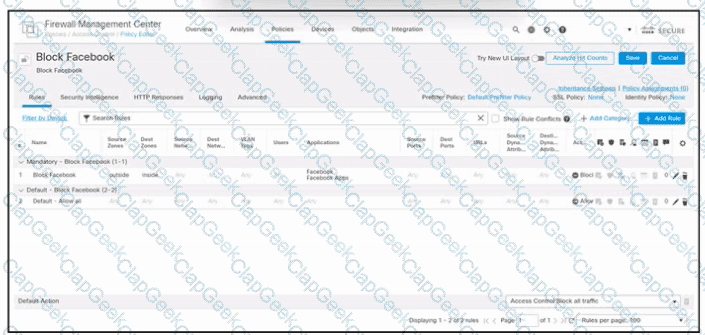
Refer to the exhibit. An engineer must block internal users from accessing Facebook and Facebook Apps. All other access must be allowed. The indicated policy was created in Cisco Secure Firewall Management Center and deployed to the internet edge firewall; however, users still can access Facebook. Which two actions must be taken to meet the requirement? (Choose two.)
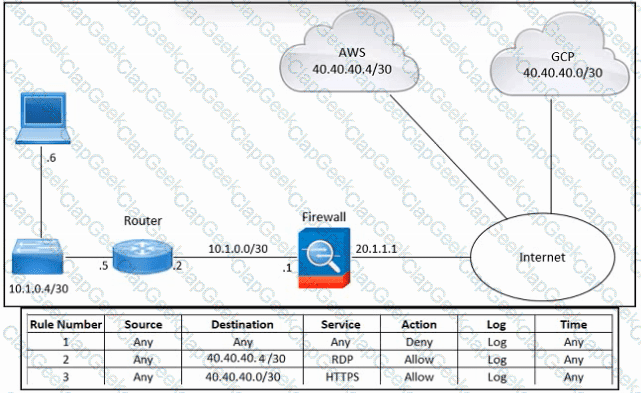
Refer to the exhibit. An engineer must provide RDP access to the AWS virtual machines and HTTPS access to the Google Cloud Platform virtual machines. All other connectivity must be blocked. The indicated rules were applied to the firewall; however, none of the virtual machines in AWS and Google Cloud Platform are accessible. What should be done to meet the requirement?
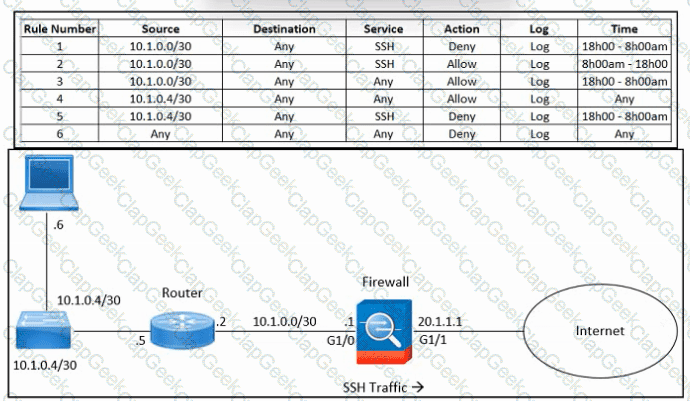
Refer to the exhibit. An engineer must troubleshoot an issue with excessive SSH traffic leaving the internal network between the hours of 18:00 and 08:00. The engineer applies a policy to the Cisco ASA firewall to block outbound SSH during the indicated hours; however, the issue persists. What should be done to meet the requirement?

Refer to the exhibit. An engineer must create a policy in Cisco Secure Firewall Management Center to prevent restricted users from being able to browse any business or mobile phone shopping websites. The indicated policy was applied; however, the restricted users still can browse on the mobile phone shopping websites during business hours. What should be done to meet the requirement?
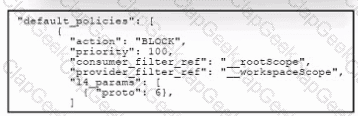
Refer to the exhibit. An engineer configured a default segmentation policy in Cisco Secure Workload to block SMTP traffic. During testing, it is observed that the SMTP traffic is still allowed. Which action must the engineer take to complete the configuration?
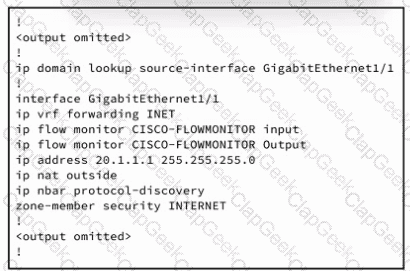
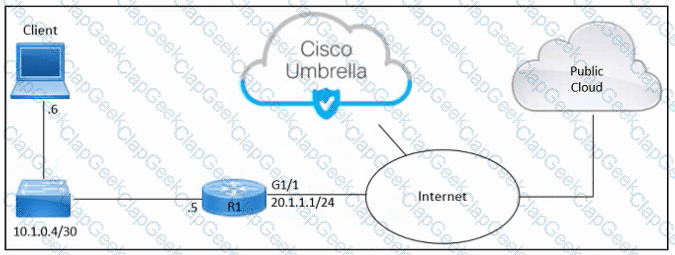
Refer to the exhibit. An engineer must connect an on-premises network to the public cloud using Cisco Umbrella as a Cloud Access Security Broker. The indicated configuration was applied to router R1; however, connectivity to Umbrella fails with this error: %OPENDNS-3-DNS_RES_FAILURE. Which action must be taken on R1 to enable the connection?
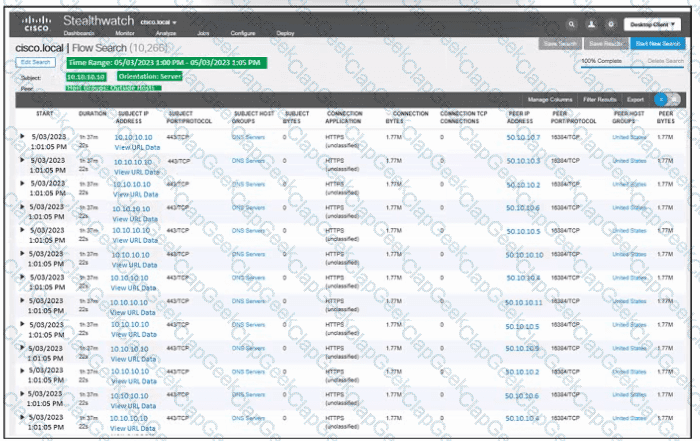
Refer to the exhibit. An engineer must troubleshoot an incident by using Cisco Secure Cloud Analytics. What is the cause of the issue?


