When DKIM signing is configured, which DNS record must be updated to load the DKIM public signing key?
Which two features of Cisco Email Security are added to a Sender Group to protect an organization against email threats? (Choose two.)
Which action on the Cisco ESA provides direct access to view the safelist/blocklist?
An administrator needs to configure Cisco ESA to ensure that emails are sent and authorized by the owner of the domain. Which two steps must be performed to accomplish this task? (Choose two.)
Spammers routinely try to send emails with the recipient field filled with a list of all possible combinations of letters and numbers. These combinations, appended with a company domain name are malicious attempts at learning all possible valid email addresses. Which action must be taken on a Cisco Secure Email Gateway to prevent this from occurring?
Which two action types are performed by Cisco ESA message filters? (Choose two.)
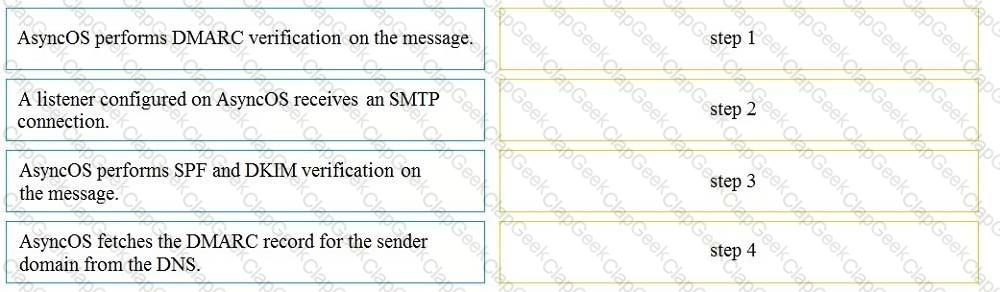
Drag and drop the AsyncOS methods for performing DMARC verification from the left into the correct order on the right.
Which type of attack is prevented by configuring file reputation filtering and file analysis features?
Which two certificate authority lists are available in Cisco ESA? (Choose two.)
Which two actions are configured on the Cisco ESA to query LDAP servers? (Choose two.)
A content dictionary was created for use with Forged Email Detection. Proper data that pertains to the CEO Example CEO:
Which action on the Cisco ESA provides direct access to view the safelist/blocklist?
Drag and drop the AsyncOS methods for performing DMARC verification from the left into the correct order on the right.

An email containing a URL passes through the Cisco ESA that has content filtering disabled for all mail policies. The sender is sampleuser@test1.com, the recipients are testuser1@test2.com, testuser2@test2.com, testuser3@test2.com, and mailer1@test2.com. The subject of the email is Test Document395898847. An administrator wants to add a policy to ensure that the Cisco ESA evaluates the web reputation score before permitting this email.
Which two criteria must be used by the administrator to achieve this? (Choose two.)
An administrator is trying to enable centralized PVO but receives the error, "Unable to proceed with Centralized Policy, Virus and Outbreak Quarantines configuration as esa1 in Cluster has content filters / DLP actions available at a level different from the cluster level."
What is the cause of this error?
Refer to the exhibit.
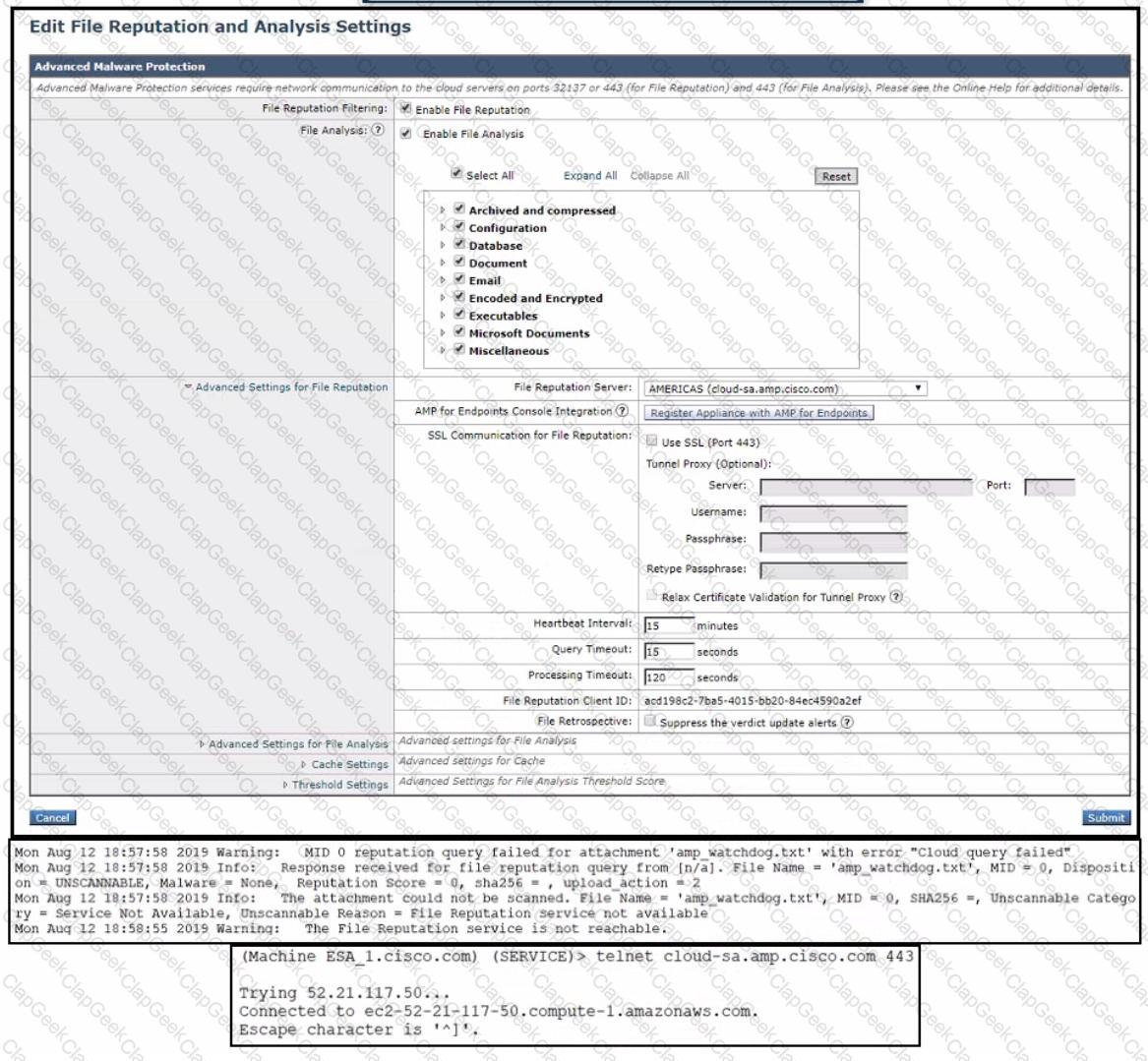
An administrator has configured File Reputation and File Analysis on the Cisco Secure Email Gateway appliance however it does not function as expected What must be configured on the appliance for this to function?
The CEO sent an email indicating that all emails containing a string of 123ABCDEFGHJ cannot be delivered and must be sent into quarantine for further inspection. Given the requirement, which regular expression should be used to match on that criteria?
A network administrator notices that there are a high number of queries to the LDAP server. The mail logs show an entry “550 Too many invalid recipients | Connection closed by foreign host.”
Which feature must be used to address this?
When the spam quarantine is configured on the Cisco Secure Email Gateway, which type of query is used to validate non administrative user access to the end-user quarantine via LDAP?
What must be configured to allow the Cisco ESA to encrypt an email using the Cisco Registered Envelope Service?
Refer to the exhibit.
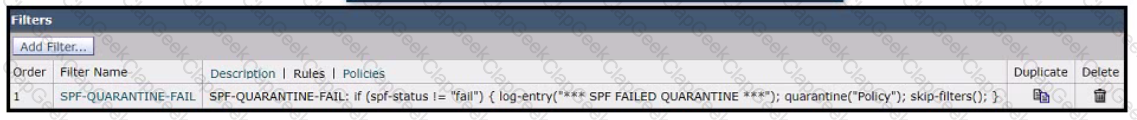
A network engineer must set up a content filter to find any messages that failed SPF and send them into quarantine The content filter has been set up and enabled, but all messages except those that have failed SPF are being sent into quarantine. Which section of the filter must be modified to correct this behavior?
Which two features are applied to either incoming or outgoing mail policies? (Choose two.)
Which method enables an engineer to deliver a flagged message to a specific virtual gateway address in the most flexible way?
An engineer deploys a Cisco Secure Email Gateway appliance with default settings in an organization that permits only standard H feature does not work. Which additional action resolves the issue?
An Encryption Profile has been set up on the Cisco ESA.
Drag and drop the steps from the left for creating an outgoing content filter to encrypt emails that contains the subject "Secure:" into the correct order on the right.

An organization has multiple Cisco Secure Email Gateway appliances deployed, resulting in several spam quarantines to manage. To manage the quarantined messages, the administrator enabled the centralized spam quarantine on the Cisco Secure Email and Web Manager appliance and configured the external spam quarantine on the Cisco Secure Email Gateway appliances. However, messages are still being directed to the local quarantine on the Cisco Secure Email Gateway appliances What change is necessary to complete the configuration?
Which action do Outbreak Filters take to stop small-scale and nonviral attacks, such as phishing scams and malware distribution sites?
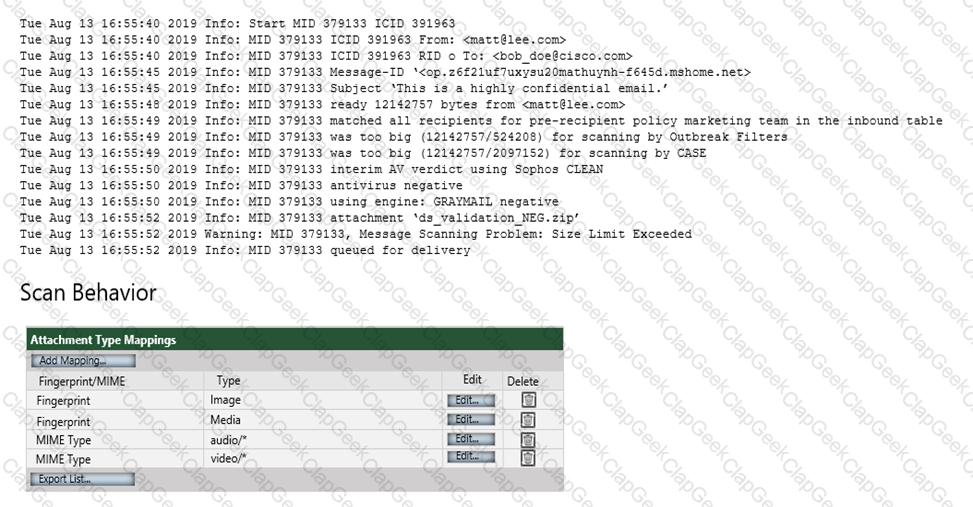
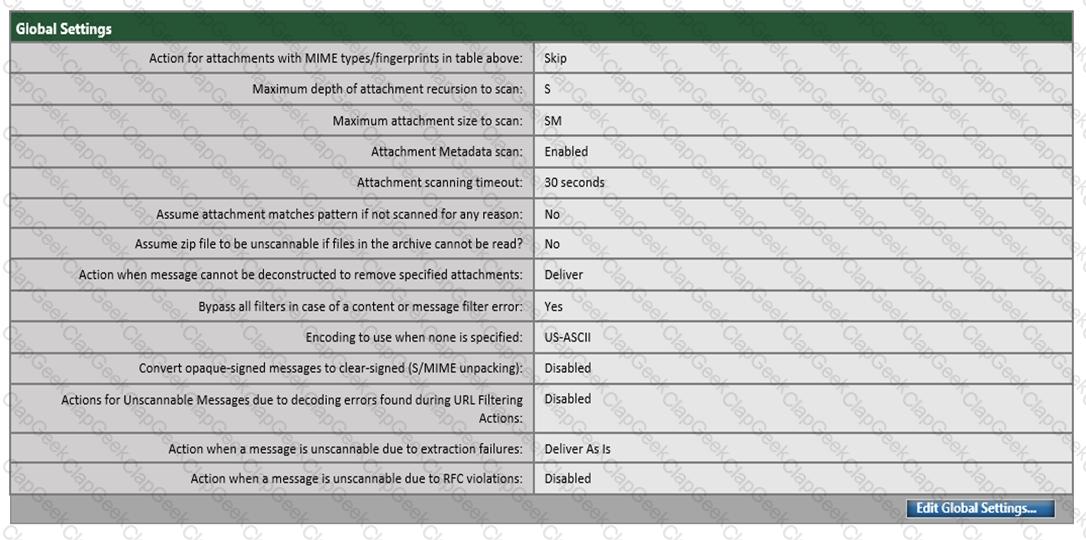
Refer to the exhibit. Which configuration on the scan behavior must be updated to allow the attachment to be scanned on the Cisco ESA?
An engineer wants to utilize a digital signature in outgoing emails to validate to others that the email they are receiving was indeed sent and authorized by the owner of that domain Which two components should be configured on the Cisco Secure Email Gateway appliance to achieve this? (Choose two.)
An administrator has created a content filter to quarantine all messages that result in an SPF hardfail to review the messages and determine whether a trusted partner has accidentally misconfigured the DNS settings. The administrator sets the policy quarantine to release the messages after 24 hours, allowing time to review while not interrupting business.
Which additional option should be used to help the end users be aware of the elevated risk of interacting with these messages?
Refer to the exhibit.

A network engineer must set up a content filter to find any messages that failed SPF and send them into quarantine The content filter has been set up and enabled, but all messages except those that have failed SPF are being sent into quarantine. Which section of the filter must be modified to correct this behavior?
What are two prerequisites for implementing undesirable URL protection in Cisco ESA? (Choose two.)
Which two factors must be considered when message filter processing is configured? (Choose two.)
A Cisco ESA administrator has noticed that new messages being sent to the Centralized Policy Quarantine are being released after one hour. Previously, they were being held for a day before being released.
What was configured that caused this to occur?
When outbreak filters are configured, which two actions are used to protect users from outbreaks? (Choose two.)


