What happens when an internal user is configured with an external identity store for authentication, but an engineer uses the Cisco ISE admin portal to select an internal identity store as the identity source?
An administrator is editing a csv list of endpoints and wants to reprofile some of the devices indefinitely before importing the list into Cisco ISE. Which field and Boolean value must be changed for the devices before the list is reimported?
Which Cisco ISE deployment model provides redundancy by having every node in the deployment configured with the Administration. Policy Service, and Monitoring personas to protect from a complete node failure?
An engineer is configuring a guest password policy and needs to ensure that the password complexity requirements are set to mitigate brute force attacks. Which two requirement complete this policy? (Choose two)
An ISE administrator must change the inactivity timer for MAB endpoints to terminate the authentication session whenever a switch port that is connected to an IP phone does not detect packets from the device for 30 minutes. Which action must be taken to accomplish this task?
ESTION NO: 100
An organization wants to improve their BYOD processes to have Cisco ISE issue certificates to the BYOD endpoints. Currently, they have an active certificate authority and do not want to replace it with Cisco ISE. What must be configured within Cisco ISE to accomplish this goal?
An administrator is configuring posture with Cisco ISE and wants to check that specific services are present on the workstations that are attempting to access the network. What must be configured to accomplish this goal?
Refer to the exhibit.
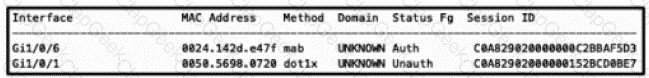
An engineer is configuring a client but cannot authenticate to Cisco ISE During troubleshooting, the show authentication sessions command was issued to display the authentication status of each port Which command gives additional information to help identify the problem with the authentication?
An engineer deploys Cisco ISE and must configure Active Directory to then use information from Active Directory in an authorization policy. Which two components must be configured, in addition to Active Directory groups, to achieve this goat? (Choose two )
A Cisco device has a port configured in multi-authentication mode and is accepting connections only from hosts assigned the SGT of SGT_0422048549 The VLAN trunk link supports a maximum of 8 VLANS What is the reason for these restrictions?
An administrator must configure Cisco ISE to send CoA requests to a Cisco switch using SNMP. These configurations were already performed:
enabled SNMP on the switch
added the switch to Cisco ISE
configured a network device profile
configured the NAD port detection method
configured the operation to be performed on the switch port
configured an authorization profile
Which two configurations must be performed to send the CoA requests? (Choose two.)
There are several devices on a network that are considered critical and need to be placed into the ISE database and a policy used for them. The organization does not want to use profiling. What must be done to accomplish this goal?
An engineer is assigned to enhance security across the campus network. The task is to enable MAB across all access switches in the network. Which command must be entered on the switch to enable MAB?
Using the SAK Active Directory Federation Services server. The configurations were performed:
• created a new SAML Identity provider profile in Cisco ISE
• exported the service provider Information
• configured all the required Active Directory Federation Services configurations
• Imported the Active Directory Federation Services metadata
• configured groups in the new SAML identity
• added attributes to the new SAML identity provider profile
• configured Advanced Settings in the new SAML identity provider profile
Which two actions must be taken to complete the configuration? (Choose two.)
An engineer is working with a distributed deployment of Cisco ISE and needs to configure various network probes to collect a set of attributes from the endpoints on the network. Which node should be used to accomplish this task?
An engineer must use Cisco ISE to provide network access to endpoints that cannot support 802.1X. The endpoint MAC addresses must be allowlisted by configuring an endpoint identity group. These configurations were performed:
Configured an identity group named allowlist
Configured the endpoints to use the MAC address of incompatible 802.1X devices
Added the endpoints to the allowlist identity group
Configured an authentication policy for MAB users
What must be configured?
An engineer wants to use certificate authentication for endpoints that connect to a wired network integrated with Cisco ISE. The engineer needs to define the certificate field used as the principal username. Which component would be needed to complete the configuration?
Which two VMware features are supported on a Cisco ISE virtual appliance? (Choose two.)
An administrator is troubleshooting an endpoint that is supposed to bypass 802 1X and use MAB. The endpoint is bypassing 802.1X and successfully getting network access using MAB. however the endpoint cannot communicate because it cannot obtain an IP address. What is the problem?
Which term refers to an endpoint agent that tries to join an 802 1X-enabled network?
TION NO: 33
Which portal is used to customize the settings for a user to log in and download the compliance module?
Which two values are compared by the binary comparison (unction in authentication that is based on Active Directory?
What are two components of the posture requirement when configuring Cisco ISE posture? (Choose two)
A network engineer must configure a policy rule to check the endpoint. The policy must ensure disk encryption is enabled and the appropriate antivirus software version is installed. Which configuration must the engineer apply to the rule?
An administrator wants to configure network device administration and is trying to decide whether to use TACACS* or RADIUS. A reliable protocol must be used that can check command authorization Which protocol meets these requirements and why?
NO: 184
An engineer builds a five-node distributed Cisco ISE deployment The first two deployed nodes are responsible for the primary and secondary administration and monitoring personas Which persona configuration is necessary to have the remaining three Cisco ISE nodes serve as dedicated nodes in the Cisco ISE cube that is responsible only for handling the RADIUS and TACACS+ authentication requests, identity lookups, and policy evaluation?
A)

B)
C)
D)
What is an advantage of TACACS+ versus RADIUS authentication when reviewing reports in Cisco ISE?
A network administrator has just added a front desk receptionist account to the Cisco ISE Guest Service sponsor group. Using the Cisco ISE Guest Sponsor Portal, which guest services can the receptionist provide?
A new employee just connected their workstation to a Cisco IP phone. The network administrator wants to ensure that the Cisco IP phone remains online when the user disconnects their Workstation from the corporate network Which CoA configuration meets this requirement?
On which port does Cisco ISE present the Admin certificate for posture and client provisioning?
An administrator replaced a PSN in the distributed Cisco ISE environment. When endpoints authenticate to it, the devices are not getting the right profiles or attributes and as a result, are not hitting the correct policies. This was working correctly on the previous PSN. Which action must be taken to ensure the endpoints get identified?
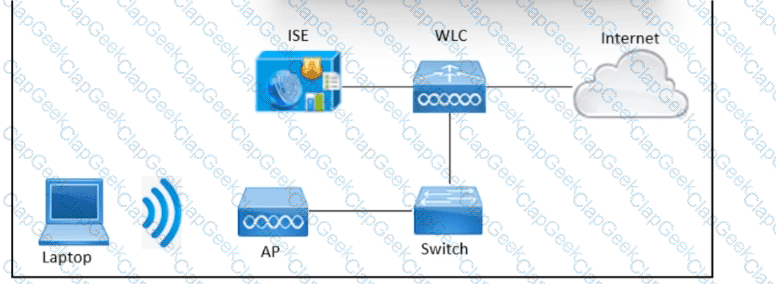
Refer to the exhibit. An engineer needs to configure central web authentication on the Cisco Wireless LAN Controller to use Cisco ISE for all guests connected to the wireless network. The components are configured already:
• Cisco Wireless LAN Controller is fully configured
• authorization profile on the Cisco ISE
• authentication policy on the Cisco ISE
Which component would be configured next on Cisco ISE?
A network administrator is configuring authorization policies on Cisco ISE There is a requirement to use AD group assignments to control access to network resources After a recent power failure and Cisco ISE rebooting itself, the AD group assignments no longer work What is the cause of this issue?
An administrator is configuring a new profiling policy within Cisco ISE The organization has several endpoints that are the same device type and all have the same Block ID in their MAC address. The profiler does not currently have a profiling policy created to categorize these endpoints. therefore a custom profiling policy must be created Which condition must the administrator use in order to properly profile an ACME Al Connector endpoint for network access with MAC address
An engineer is working on a switch and must tag packets with SGT values such that it learns via SXP. Which command must be entered to meet this requirement?
An administrator is adding network devices for a new medical building into Cisco ISE. These devices must be in a network device group that is identifying them as "Medical Switch" so that the policies can be made separately for the endpoints connecting through them. Which configuration item must be changed in the network device within Cisco ISE to accomplish this goal?
Which file extension is required when deploying Cisco ISE using a ZTP configuration file in Microsoft Hyper-V?
Which two ports must be open between Cisco ISE and the client when you configure posture on Cisco ISE? (Choose two).
An engineer needs to configure a compliance policy on Cisco ISE to ensure that the latest encryption software is running on the C drive of all endpoints. Drag and drop the configuration steps from the left into the sequence on the right to accomplish this task.
Which two methods should a sponsor select to create bulk guest accounts from the sponsor portal? (Choose two )
An engineer is configuring a dedicated SSID for onboarding devices. Which SSID type accomplishes this configuration?
What must be configured on the Cisco ISE authentication policy for unknown MAC addresses/identities for successful authentication?
An engineer is configuring posture assessment for their network access control and needs to use an agent that supports using service conditions as conditions for the assessment. The agent should be run as a background process to avoid user interruption but when it is run. the user can see it. What is the problem?
An engineer is implementing Cisco ISE and needs to configure 802.1X. The port settings are configured for port-based authentication. Which command should be used to complete this configuration?
An engineer is starting to implement a wired 802.1X project throughout the campus. The task is for failed authentication to be logged to Cisco ISE and also have a minimal impact on the users. Which command must the engineer configure?
An engineer needs to configure a new certificate template in the Cisco ISE Internal Certificate Authority to prevent BYOD devices from needing to re-enroll when their MAC address changes. Which option must be selected in the Subject Alternative Name field?
A security administrator is using Cisco ISE to create a BYOD onboarding solution for all employees who use personal devices on the corporate network. The administrator generates a Certificate Signing Request and signs the request using an external Certificate Authority server. Which certificate usage option must be selected when importing the certificate into ISE?
An administrator must deploy the Cisco Secure Client posture agent to employee endpoints that access a wireless network by using URL redirection in Cisco ISE. The compliance module must be downloaded from Cisco and uploaded to the Cisco ISE client provisioning resource. What must be used to upload the compliance module?
What allows an endpoint to obtain a digital certificate from Cisco ISE during a BYOD flow?
A Cisco ISE administrator needs to ensure that guest endpoint registrations are only valid for one day When testing the guest policy flow, the administrator sees that the Cisco ISE does not delete the endpoint in the Guest Endpoints identity store after one day and allows access to the guest network after that period. Which configuration is causing this problem?
An engineer is deploying Cisco ISE in a network that contains an existing Cisco Secure Firewall ASA. The customer requested that Cisco TrustSec be configured so that Cisco ISE and the firewall can share SGT information.
Which protocol must be configured on Cisco ISE to meet the requirement?
Which action must be taken before configuring the Secure Client Agent profile when creating the Secure Client configuration for ISE posture services?
An engineer is deploying a new Cisco ISE environment for a company. The company wants the deployment to use TACACS+. The engineer verifies that Cisco ISE has a Device Administration license. What must be configured to enable TACACS+ operations?
An engineer must use Cisco ISE profiler services to provide network access to Cisco IP phones that cannot support 802.1X. Cisco ISE is configured to use the access switch device sensor information — system-description and platform-type — to profile Cisco IP phones and allow access.
Which two protocols must be configured on the switch to complete the configuration? (Choose two.)
An engineer is configuring the remote access VPN to use Cisco ISE for AAA and needs to conduct posture checks on the connecting endpoints After the endpoint connects, it receives its initial authorization result and continues onto the compliance scan What must be done for this AAA configuration to allow compliant access to the network?
Which two features must be used on Cisco ISE to enable the TACACS. feature? (Choose two)
Users in an organization report issues about having to remember multiple usernames and passwords. The network administrator wants the existing Cisco ISE deployment to utilize an external identity source to alleviate this issue. Which two requirements must be met to implement this change? (Choose two.)
An engineer is configuring sponsored guest access and needs to limit each sponsored guest to a maximum of two devices. There are other guest services in production that rely on the default guest types. How should this configuration change be made without disrupting the other guest services currently offering three or more guest devices per user?
An engineer is designing a BYOD environment utilizing Cisco ISE for devices that do not support native supplicants Which portal must the security engineer configure to accomplish this task?
What must match between Cisco ISE and the network access device to successfully authenticate endpoints?
An engineer tests Cisco ISE posture services on the network and must configure the compliance module to automatically download and install on endpoints Which action accomplishes this task for VPN users?
An engineer is configuring a new Cisco ISE node. Context-sensitive information must be shared between the Cisco ISE and a Cisco ASA. Which persona must be enabled?
Which configuration is required in the Cisco ISE authentication policy to allow Central Web Authentication?
Drag the Cisco ISE node types from the left onto the appropriate purposes on the right.
What is the maximum number of PSN nodes supported in a medium-sized deployment?
A user is attempting to register a BYOD device to the Cisco ISE deployment, but needs to use the onboarding policy to request a digital certificate and provision the endpoint. What must be configured to accomplish this task?
An administrator is configuring the Native Supplicant Profile to be used with the Cisco ISE posture agents and needs to test the connection using wired devices to determine which profile settings are available. Which two configuration settings should be used to accomplish this task? (Choose two.)
Which RADIUS attribute is used to dynamically assign the inactivity active timer for MAB users from the Cisco ISE node'?
An administrator is configuring a Cisco WLC for web authentication Which two client profiling methods are enabled by default if the Apply Cisco ISE Default Settings check box has been selected'? (Choose two.)
A network administrator notices that after a company-wide shut down, many users cannot connect their laptops to the corporate SSID. What must be done to permit access in a timely manner?
Which CLI command must be configured on the switchport to immediately run the MAB process if a non-802.1X capable endpoint connects to the port?
MacOS users are complaining about having to read through wordy instructions when remediating their workstations to gam access to the network Which alternate method should be used to tell users how to remediate?
What are two benefits of TACACS+ versus RADIUS for device administration? (Choose two )
What must be configured on the WLC to configure Central Web Authentication using Cisco ISE and a WLC?
Which two external identity stores are supported by Cisco ISE for password types? (Choose two.)


