Select two statements that correctly describe the capabilities of the Distribution Constructor.
You are troubleshooting the Oracle Solaris11 Automated Installer (AI), which is not connecting with the IPS software repository.
Which three steps will help determine the cause of DNS name resolution failure?
Your server hangs intermittently and you believe it may be due to either faulty hardware or a driver. The support technician has told you to generate a live core dump of all memory pages for further analysis Your dump configuration is:
Dump content: kernel pages
Dump device: /dev/zvol/dsk/rpool/dump (dedicated)
Savecore directory: /var/crash
Savecore enabled: yes
Save compressed: on
You don't have enough space on the current dump device, so you need to store the dump on /dev/zvol/dsk/pool2/dump
Which option would you select to change the dump location for the next core dump and capture the content of all memory pages as requested by the support technician?
After installing the OS, you boot the system and notice that the syslogd daemon is not accepting messages from remote systems.
Which two options should you select to modify the syslogd daemon configuration so that it accepts syslog messages from remote systems? (Choose two.)
You want the system to generate core files when an application crashes, but you want only root to be able to view the core files. The current core configuration is:
global core file pattern: /var/core/core %f.%p
global core file content: default
init core file pattern: /var/core/pprocess/core.%f.%pp
init core file content: default
global core dumps: enabled
per—process core dumps: enabled
global setid core dumps disabled
per-process setid core dumps: disabled
global core dump logging disabled
Select the option that describes the change that needs to be made to the core dump configuration to meet this requirement.
The following information is displayed about the compress/zjp software package, which Is currently installed on this system:
NAME (PUBLISHER)VERSIONIFO
Compress/zip3.1.2-0.175.0.0.0.0.537if-
NAMEVERSIONDATECOMMENT
Compress/zip3.109 Dec 2011 04:50:38 ESTNone
Which statement describes the information that is displayed tor the compress/zip software package?
Which command should you choose to display the current parameters for the FSS scheduler?
You want to deploy oracle Solaris 11 with the automated installer (AI). You need to make sure that your server and network meet the requirements for using AI.
Choose the three options that describe; the requirements for using AI.
You upgraded your server to Oracle Solaris 11 and you imported zpool (pool1) that was created in Solaris 10. You need to create an encrypted ZFS file system in pool1, but first you need to make sure that your server supports ZFS encryption.
Which four statements are true for support of ZFS encryption?
You have been tasked with creating a dedicated virtual network between two local zones within a single system. In order to isolate the network traffic from other zones on that system.
To accomplish this, you will create__________.
alice is a user account used by Alice on a Solaris 11 system.
sadmin is a role account on the same system.
Your task is to add the command /usr/sbin/cryptoadm to the Network management profile, so that Alice can execute it, while assuming the sadmin role.
Select the three activities necessary to accomplish this.
View the Exhibit
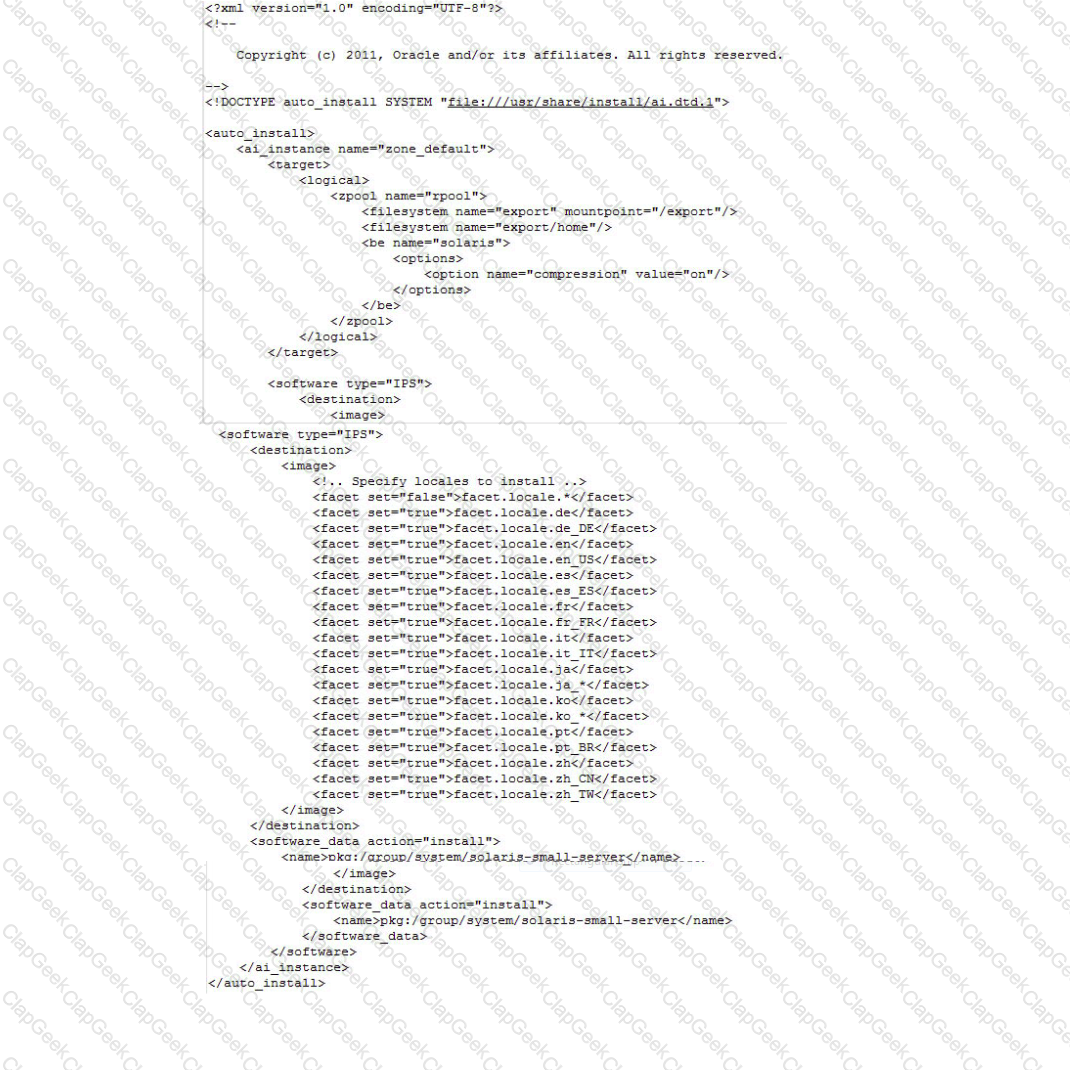
The file came from your Automated Installer (Al) Install server.
The file is_______.
You have a Solaris 10 system with a host name of sysA and it uses LDAP as a naming service. You have created a flash archive of sysA and you want to migrate this system to an Oracle Solaris 11 server as a solarislO branded zone The zone status on the Oracle Solaris 11 server is:
-zonel 0incomplete/zone/zone1solaris10 excl
Select the option that will force the non-global zone to prompt you for a host name and name service the first time it is booted.
Review the zonestat command:
zonestate - q physical - memory -R high -z -p -p “zones” 10 24h 60m
Select the option that correctly describes the information that is displayed by this command.
Review the output from a ZFS file system:
NAMEPROPERTYVALUESOURCE
pool1/encryptencryptionaes-256-ccmlocal pool1/encryptkeysourceraw,file///mykeylocal
You need to recreate the pooM/encrypt file system exactly as it is listed above Which two commands can you use to recreate the pooM/encrypt file system?
(Choose two.)
You are using this rule file with the Basic Audit Reporting Tool (BART) to detect inappropriate file system changes.
CHECK all IGNORE dirmtime
/etc/acct /etc/security /etc/notices IGNORE contents
/export/home/alice IGNORE mtime size contents
A/ar CHECK
/var/tmp IGNORE all
Identify the two correct statements describing the attributes recorded. (Choose two.)


