The sqinet.oia file on the client contains this parameter setting:
SQLNET.ENCRYPTION_CLIEKT = REQUESTED
What value for the parameter sQLNET.ENCRYPTION _server In the sqlnet.ora file on the server will disable Encryption and Data Negotiation?
Examine these steps:
1. Run the DBSAT Collector
2. Run the DBSAT Discoverer
3. Run the DBSAT Reporter
Identify the minimum required steps for producing a report of schemas with sensitive data.
Which two authorization rights does a Database Vault realm owner have that a realm participant does not have?
Which four products, features, or methods can help facilitate compliance with various privacy-related regulatory requirements such as PCI-DSS and the EU GDPR?
Which two represent the set of users that are never affected by connect command rules?
What does the Application Data Modeling module of the Oracle Data Masking and Subsetting Pack search for?
The utl_http package is used to invoke REST API's to manage Oracle GoldenGate Microservlces Architecture components on host1.
You must use dbms__network_acl_admin to specify a range of ports to be used when connecting to host01.
What three requirements must you consider?
Examine these statements which execute successfully:
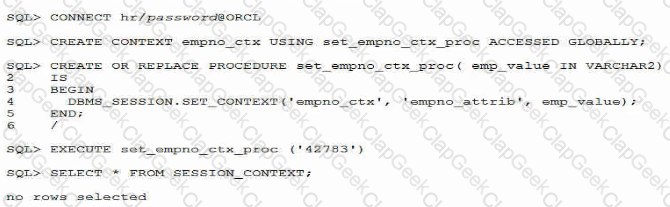
Which are the two reasons that no rows Are returned from the query?


