Layer 2 mapping information is announced by an interface without receiving a request for the mapping first.
Which term describes this event?
A BIG-IP administrator is interested in using some of the vCMP
What should impact the administrator's decision?
In an active/standby high-availability mode, what causes a standby unit to assume the active role?
A BIG IP Administrator reviews the Virtual Server configuration and sees the object status represented by a blue square tor an unknown status.How should the administrator change the unknown status?
A new virtual server is being tested to replace http://myapp.mydomain.com. The original virtual server is still on use. And the new virtual server is on a different ip address. What should be done to test this new virtual server using the fully quailed domain name for this application?
Which Datalink sublayer has the primary funcl.cn of proving node lo node flow and error control?
A web administrator has added content to a web application, but users are unable to access the new content What could be preventing them from accessing the content?
HTTP pool attached to a Virtual Server has three members
Pool member A default HTTP monitor in red
Pool member 6 custom HTTP monitor in green
Pool member C does not monitor
Which pool members participate in the load balancing?
A Network Administrator needs a new networking device can perform NAT to connect several devices on a computer network.
What is the most appropriate device for this requirement?
A BIG-IP Administrator needs to upgrade an HA pair to a more recent TMOS version. The administrator is unsure if the BlG-IP is currently supported How should the administrator verity that the HA pair is under a valid support contract?
A BIG IP Administrator wants to add a new VLAN (VLAN 40) to an LACP trunk (named LACP01) connected to the BIG IP device, Multiple other VLANs exist on LACP01.Which TMSH command should the BIG IP Administrator issue to add the new VLAN lo the existing LAC?
A BIG IP Administrator wants to add a new VLAN (VLAN 40) to an LACP trunk (named IACP01) connected to the BIG IP device Multiple other VLANs exist on LACP01. Which TMSH command should the BIG IP Administrator issue to add the new VLAN to the existing LAC?
An application has a mix of both and short and long lived connections. Which algorithm would provide and event distributionof all connections across the pool?
The use of attack signature within an intrusion Detection System (IDS) is an application of which security model?
An administrator finds a new vulnerability in a web application and needs to rapidly mitigate the threat. Which F5 feature provides this functionality?
An organization needs to cryptographically sign its domains. Which F5 product provides this functionality?
The 2001:db8: : IP6 address block is allocated to a load balancer for use as virtual server addresses. The address block is routed to a balancer self IP address using a static route. What is the correct representation for the last address in the address block that a virtual server can use?
A company is creating a new department for Security Engineering and needs to create a segregated network segment with only 24 IPS.
What should be configured?
An administrator is given the IP Address of 192.168.100.124 and needs 64 subnets.
How many hosts per network are allowed?
A user fails to provide credentials when requesting a web resource that requires authentication. Which HTTP response code does the server send?
BIG-IP Administrator runs the command ITconfig from the BIG-IP command the line end sees a high number of collisions. What is the likely cause?
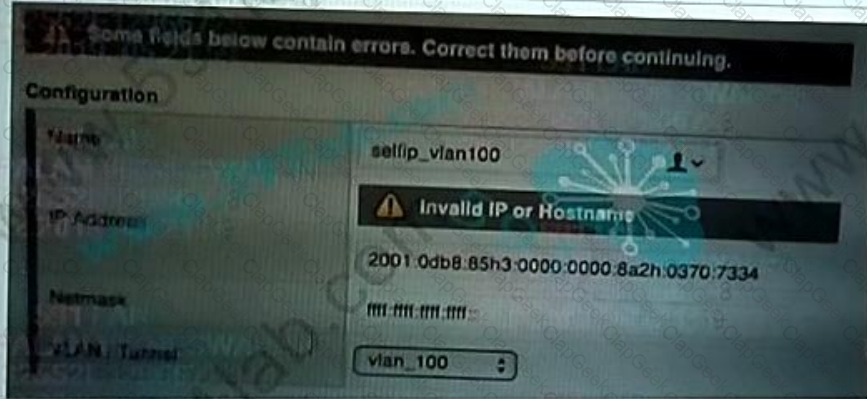
An administrate receives an error message when attempting to create a self-IP address on a BIG-IP appliance Which address should the administrator use to resolve the issue?
A 2001 0db8.85a3 0000 0000 8a2e 0370 7334
B. 2001:db8:85a3 Bd3.Ba2e.370 7334
C. 2001:0db8:85i3:0000:0000: : 8a2i:0370:7334
What should a BIG-IP Administrator configure to minimize impact during a failure?
An administrator notices the following log message generated by a BIG IP system " diskmonitor 011d005: Disk partition shared has less than 30% tree" Which command should the administrator use to troubleshoot the problem?
A client’s operating system needs to make sure that data received from a server is mapped to the application that requested it.
How does it complete this mapping?
A BIG-IP Administrator needs to make sure that requests from a single user are directed to the server that was initially selected (unless that server is marked down). What should the administrator configure?
A BIG-IP Administrator needs a solution to tunnel traffic and transmit encrypted connections over the Internet using only a standard browser and common ports and protocols. Which solution should the administrator select?
An administrator is designing a remote host connection using an ICMP based network troubleshooting utility and receive an ICMP error diagram with the following error code.
11. Times exceeded
What does this mean?
A server is capable of handling more connections than other servers in the same pool. Which load distribution method should the administrator choose?
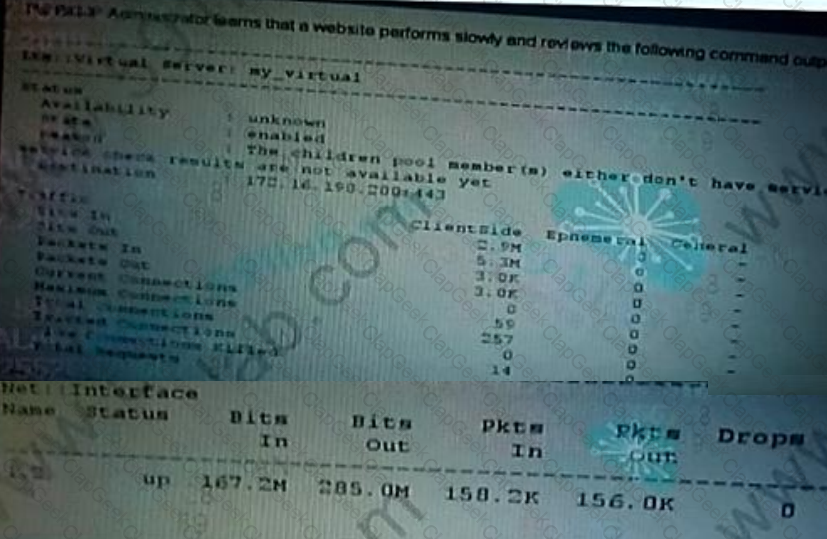
What should the administrator investigate first to address this traffic slownes


