A multinational company with over 300,000 employees has recently deployed Cortex XDR in North America. The solution includes the Identity Threat Detection and Response (ITDR) add-on, and the Cortex team has onboarded the Cloud Identity Engine to the North American tenant. After waiting the required soak period and deploying enough agents to receive Identity and threat analytics detections, the team does not see user, group, or computer details for individuals from the European offices. What may be the reason for the issue?
A security audit determines that the Windows Cortex XDR host-based firewall is not blocking outbound RDP connections for certain remote workers. The audit report confirms the following:
All devices are running healthy Cortex XDR agents.
A single host-based firewall rule to block all outbound RDP is implemented.
The policy hosting the profile containing the rule applies to all Windows endpoints.
The logic within the firewall rule is adequate.
Further testing concludes RDP is successfully being blocked on all devices tested at company HQ.
Network location configuration in Agent Settings is enabled on all Windows endpoints.What is the likely reason the RDP connections are not being blocked?
A static endpoint group is created by adding 321 endpoints using the Upload From File feature. However, after group creation, the members count field shows 244 endpoints. What are two possible reasons why endpoints were not added to the group? (Choose two.)
A new parsing rule is created, and during testing and verification, all the logs for which field data is to be parsed out are missing. All the other logs from this data source appear as expected. What may be the cause of this behavior?
A Custom Prevention rule that was determined to be a false positive alert needs to be tuned. The behavior was determined to be authorized and expected on the affected endpoint. Based on the image below, which two steps could be taken? (Choose two.)
[Image description: A Custom Prevention rule configuration, assumed to trigger a Behavioral Indicator of Compromise (BIOC) alert for authorized behavior]
What is a benefit of ingesting and forwarding Palo Alto Networks NGFW logs to Cortex XDR?
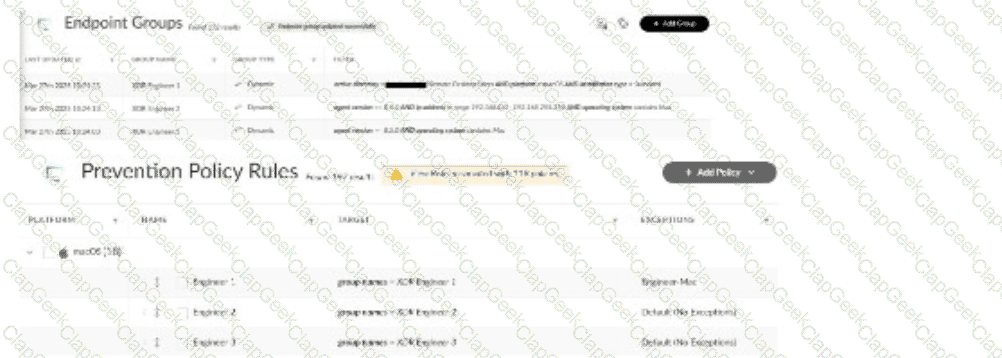
Multiple remote desktop users complain of in-house applications no longer working. The team uses macOS with Cortex XDR agents version 8.7.0, and the applications were previously allowed by disable prevention rules attached to the Exceptions Profile "Engineer-Mac." Based on the images below, what is a reason for this behavior?
Which statement describes the functionality of fixed filters and dashboard drilldowns in enhancing a dashboard’s interactivity and data insights?
Log events from a previously deployed Windows XDR Collector agent are no longer being observed in the console after an OS upgrade. Which aspect of the log events is the probable cause of this behavior?
In addition to using valid authentication credentials, what is required to enable the setup of the Database Collector applet on the Broker VM to ingest database activity?
An insider compromise investigation has been requested to provide evidence of an unauthorized removable drive being mounted on a company laptop. Cortex XDR agent is installed with default prevention agent settings profile and default extension "Device Configuration" profile. Where can an engineer find the evidence?


