Which of the following is a standard Unix command that would most likely be used to copy raw file system data for later forensic analysis?
The previous system administrator at your company used to rely heavily on email lists, such as vendor lists and Bug Traq to get information about updates and patches. While a useful means of acquiring data, this requires time and effort to read through. In an effort to speed things up, you decide to switch to completely automated updates and patching. You set up your systems to automatically patch your production servers using a cron job and a scripted apt-get upgrade command. Of the following reasons, which explains why you may want to avoid this plan?
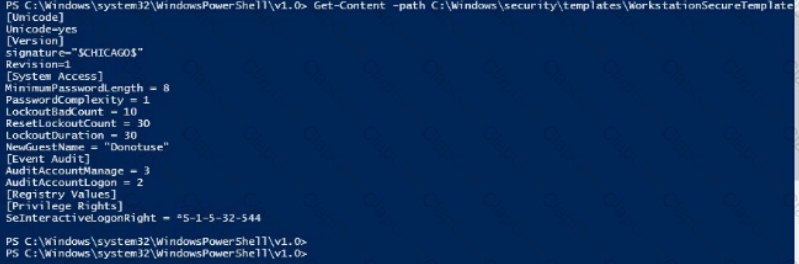
Use PowerShell ISE to
examineC:\Windows\security\templates\WorkstationSecureTemplate.inf. Which setting is configured in the template?

A simple cryptosystem that keeps the same letters and shuffles the order is an example of what?
What is the name of the command-line tool for Windows that can be used to manage audit policies on remote systems?
Against policy, employees have installed Peer-to-Peer applications on their workstations and they are using them over TCP port 80 to download files via the company network from other Peer-to-Peer users on the Internet. Which of the following describes this threat?
What is the unnoticed theft of sensitive data from a laptop owned by an organization's CEO an example of in information warfare?
Which of the following is the key point to consider in the recovery phase of incident handling?
Which of the following is the key point to consider in the recovery phase of incident handling?
What is the first thing that should be done during the containment step of incident handling?
You work as a Linux technician for Tech Perfect Inc. You have lost the password of the root. You want to provide a new password. Which of the following steps will you take to accomplish the task?
You are going to upgrade your hard disk's file system from FAT to NTFS. What are the major advantages of the NTFS file system over FAT16 and FAT32 file systems?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following statements about Secure Sockets Layer (SSL) are true? Each correct answer represents a complete solution. Choose two.
What does PowerShell remoting use to authenticate to another host in a domain environment?
What is the process of simultaneously installing an operating system and a Service Pack called?
You work as a Network Administrator for NetTech Inc. The company wants to encrypt its e-mails. Which of the following will you use to accomplish this?
Which of the following languages enable programmers to store cookies on client computers? Each correct answer represents a complete solution. Choose two.
If a DNS client wants to look up the IP address for good.news.com and does not receive an authoritative reply from its local DNS server, which name server is most likely to provide an authoritative reply?
Critical information is encrypted within an application accessible only to a small group of administrators, with a separate group of administrators holding the decryption keys. What Defense in Depth approach is being used?
To be considered a strong algorithm, an encryption algorithm must be which of the following?
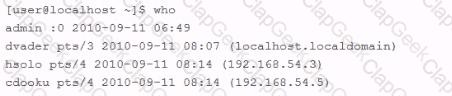
An employee is currently logged into the corporate web server, without permission. You log into the web server as 'admin" and look for the employee's username: "dmaul" using the "who" command. This is what you get back:
Which of the following would be used to explicitly deny the traffic from a foreign IP address scanning the EC2 Instances in a VPC?
You are responsible for a Microsoft based network. Your servers are all clustered. Which of the following are the likely reasons for the clustering?
Each correct answer represents a complete solution. Choose two.
You work as a Network Administrator for Net World Inc. The company has a Linux-based network. For testing purposes, you have configured a default IP-table with several filtering rules. You want to reconfigure the table. For this, you decide to remove the rules from all the chains in the table. Which of the following commands will you use?
What type of malware is a self-contained program that has the ability to copy itself without parasitically infecting other host code?
Which of the four basic transformations in the AES algorithm involves the leftward circular movement of state data?
Which of the following access control principles helps prevent collusion and detect abuse of access?
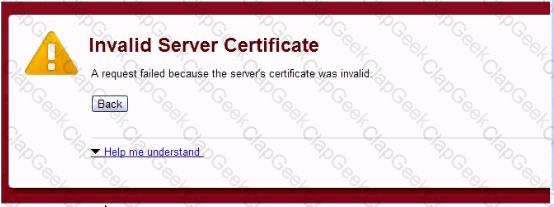
An employee attempting to use your wireless portal reports receiving the error shown below. Which scenario is occurring?
Which of the following elements is the most important requirement to ensuring the success of a business continuity plan?
Which of the following activities would take place during the containment phase?
Which of the following is a new Windows Server 2008 feature for the Remote Desktop Protocol (RDP)?
Your software developer comes to you with an application that controls a user device. The application monitors its own behavior and that of the device and creates log files. The log files are expected to grow steadily and rapidly. Your developer currently has the log files stored in the /bin folder with the application binary. Where would you suggest that the developer store the log files?
Your IT security team is responding to a denial of service attack against your server. They have taken measures to block offending IP addresses. Which type of threat control is this?
What file instructs programs like Web spiders NOT to search certain areas of a site?
You are reviewing a packet capture file from your network intrusion detection system. In the packet stream, you come across a long series of "no operation" (NOP) commands. In addition to the NOP commands, there appears to be a malicious payload. Of the following, which is the most appropriate preventative measure for this type of attack?
A Host-based Intrusion Prevention System (HIPS) software vendor records how the Firefox Web browser interacts with the operating system and other applications, and identifies all areas of Firefox functionality. After collecting all the data about how Firefox should work, a database is created with this information, and it is fed into the HIPS software. The HIPS then monitors Firefox whenever it's in use. What feature of HIPS is being described in this scenario?
Which of the following works at the network layer and hides the local area network IP address and topology?
What is the most secure way to address an unused Windows service so it cannot be exploited by malware?
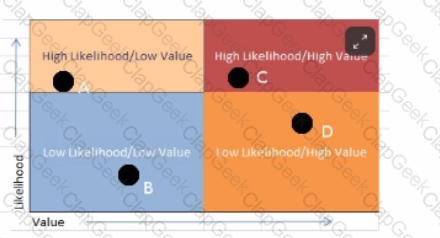
Analyze the screenshot below. In what order should the vulnerabilities be remediated?
What does an attacker need to consider when attempting an IP spoofing attack that relies on guessing Initial Sequence Numbers (ISNs)?
An attacker gained physical access to an internal computer to access company proprietary data. The facility is protected by a fingerprint biometric system that records both failed and successful entry attempts. No failures were logged during the time periods of the recent breach. The account used when the attacker entered the facility shortly before each incident belongs to an employee who was out of the area. With respect to the biometric entry system, which of the following actions will help mitigate unauthorized physical access to the facility?
What is the name of the Windows XP/2003 tool that you can use to schedule commands to be executed on remote systems during off-peak hours?
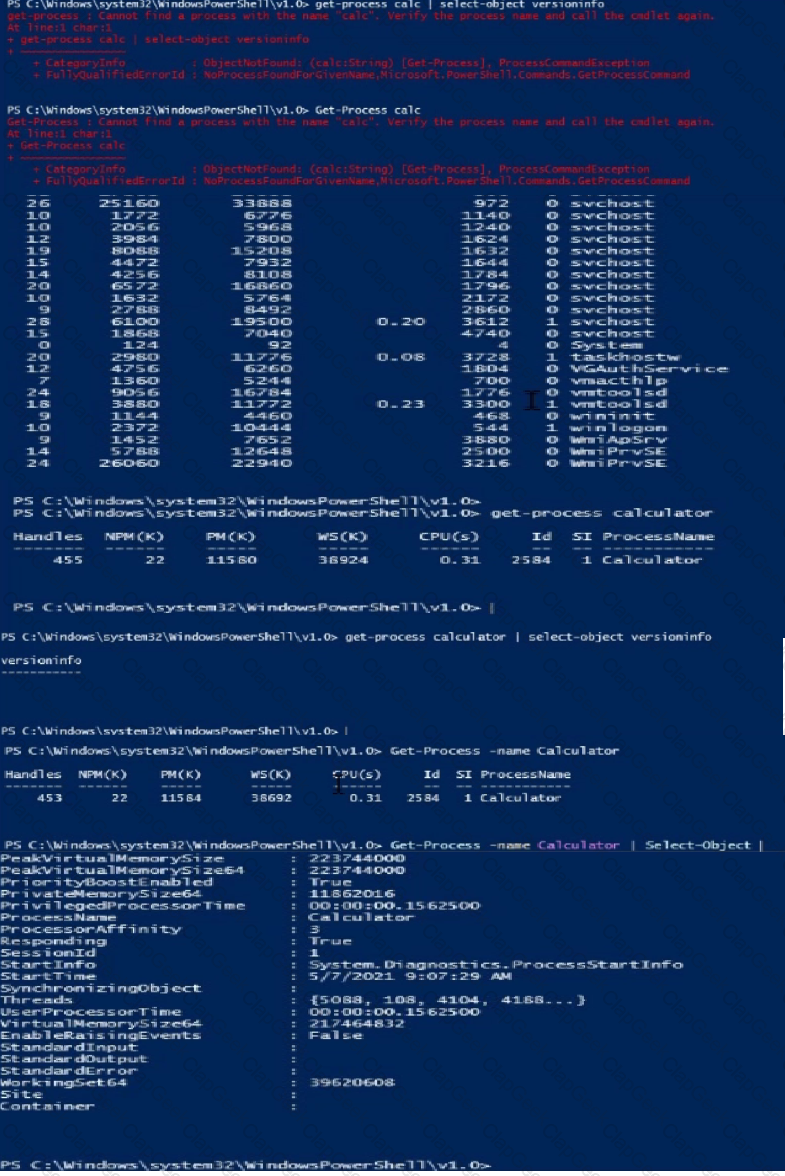
Launch Calculator (calc.exe). Using PowerShell, retrieve the Calculator Process Information. What is the value of the File Version property?
Hint: The process name of Calculator is calculator

Which of the following is a private, RFC 1918 compliant IP address that would be assigned to a DHCP scope on a private LAN?
A company disables cd drives for users; what defense strategy is this a part of?
What does the "x" character in the second field of the user account record of the /etc/passwd file indicate?
Which of the following consists of the security identifier number (SID) of your user account, the SID of all of your groups and a list of all your user rights?
Which of the following tasks is the responsibility of a Linux systems administrator who is deploying hardening scripts to his systems?
John works as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. John is working as a root user on the Linux operating system. He is currently working on his C based new traceroute program. Since, many processes are running together on the system, he wants to give the highest priority to the cc command process so that he can test his program, remove bugs, and submit it to the office in time. Which of the following commands will John use to give the highest priority to the cc command process?
Dilbert wants to have a script run on his Windows server every time Wally logs into it. Where should he place this script?
You are implementing wireless access at a defense contractor. Specifications say, you must implement the AES Encryption algorithm. Which encryption standard should you choose?
What is the purpose of notifying stakeholders prior to a scheduled vulnerability scan?
When you log into your Windows desktop what information does your Security Access Token (SAT) contain?
Which of the following SIP INVITE lines indicates to the remote registrar the VoIP phone that initiated the call?
Which of the following statements best describes where a border router is normally placed?
Which of the following is a term that refers to unsolicited e-mails sent to a large number of e-mail users?
You work as a Network Administrator for NetTech Inc. To ensure the security of files, you encrypt data files using Encrypting File System (EFS).
You want to make a backup copy of the files and maintain security settings. You can backup the files either to a network share or a floppy disk. What will you do to accomplish this?
A Network Engineer is charged with maintaining and protecting a network with a high availability requirement. In addition to other defenses, they have chosen to implement a NIPS. How should the NIPS failure conditions be configured to ensure availability if the NIPS is installed in front of the Firewall that protects the DMZ?
You are examining an IP packet with a header of 40 bytes in length and the value at byte 0 of the packet header is 6. Which of the following describes this packet?
In PKI, when someone wants to verify that the certificate is valid, what do they use to decrypt the signature?
Your organization is developing a network protection plan. No single aspect of your network seems more important than any other. You decide to avoid separating your network into segments or categorizing the systems on the network. Each device on the network is essentially protected in the same manner as all other devices.
This style of defense-in-depth protection is best described as which of the following?
Which of the following is TRUE regarding the ability of attackers to eavesdrop on wireless communications?
What would the file permission example "rwsr-sr-x" translate to in absolute mode?
Which Terraform command should be run immediately after creating a new configuration file for a cloud-based virtual machine?
A web application requires multifactor authentication when a user accesses the application from a home office but does not require this when the user is in the office. What access control model is this describing?
When trace route fails to get a timely response for a packet after three tries, which action will it take?
You have set up a local area network for your company. Your firewall separates your network into several sections: a DMZ with semi-public servers (web, dns, email) and an intranet with private servers. A penetration tester gains access to both sections and installs sniffers in each. He is able to capture network traffic for all the devices in the private section but only for one device (the device with the sniffer) in the DMZ. What can be inferred about the design of the system?
Fill in the blank with the correct answer to complete the statement below.
The permission is the minimum required permission that is necessary for a user to enter a directory and list its contents.
Which of the following processes Is used to prove a user Is who they claim to be based upon something they know, have, are, and/or their physical location?
Which of the following describes software technologies that improve portability, manageability, and compatibility of applications by encapsulating them from the underlying operating system on which they are executed?
How often is session information sent to the web server from the browser once the session information has been established?
You have been hired to design a TCP/IP-based network that will contain both Unix and Windows computers. You are planning a name resolution strategy. Which of the following services will best suit the requirements of the network?
In an Active Directory domain, which is the preferred method of keeping host computers patched?
When are Group Policy Objects (GPOs) NOT applied automatically to workstations?
You ask your system administrator to verify user compliance with the corporate policies on password strength, namely that all passwords will have at least one numeral, at least one letter, at least one special character and be 15 characters long. He comes to you with a set of compliance tests for use with an offline password cracker. They are designed to examine the following parameters of the password:
* they contain only numerals
* they contain only letters
* they contain only special characters
* they contain only letters and numerals
" they contain only letters and special characters
* they contain only numerals and special characters
Of the following, what is the benefit to using this set of tests?
While building multiple virtual machines on a single host operating system, you have determined that each virtual machine needs to work on the network as a separate entity with its own unique IP address on the same logical subnet. You also need to limit each guest operating system to how much system resources it has access to. Which of the following correctly identifies steps that must be taken towards setting up these virtual environments?
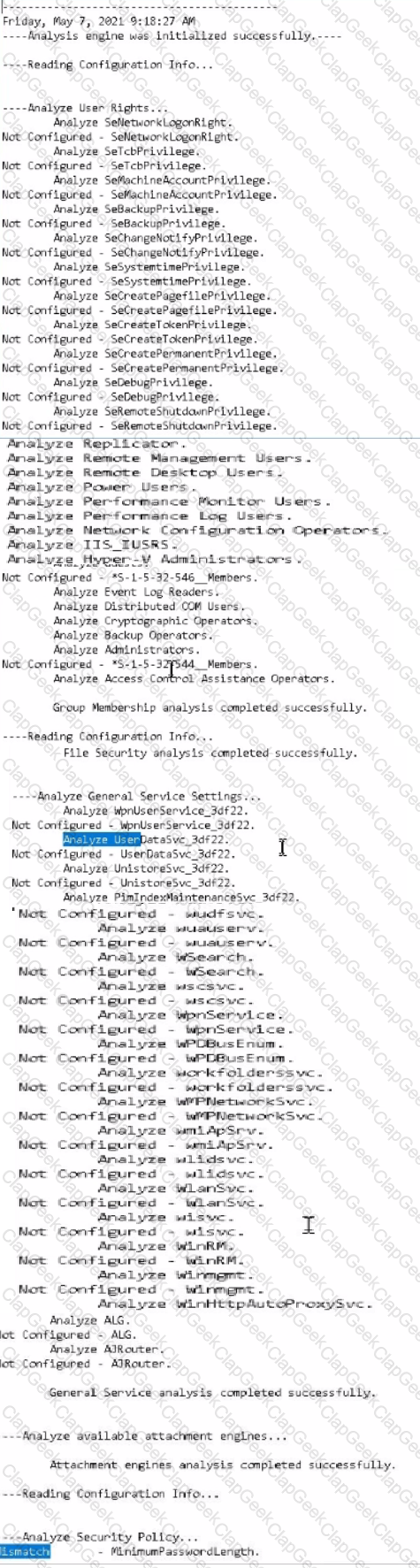
Using PowerShell ISE running as an Administrator, navigate to the
C:\hlindows\security\tevplatesdirectory. Use secedit.exe in analyze mode to compare the temp.sdb and uorkstdtionSecureTmplate.inf files, and output the findings to a file called log.txt. Which configuration setting under Analyze User Rights reports a mismatch?
Hints:
Use files located in the C \windows\security\templates\ directory
The log. txt file will be created in the directory the secedit.exe command is run from

The process of enumerating all hosts on a network defines which of the following activities?
Which of the following is more commonly used for establishing high-speed backbones that interconnect smaller networks and can carry signals over significant distances?
An email system administrator deploys a configuration blocking all inbound and outbound executable files due to security concerns.
What Defense in Depth approach is being used?
What is the term for a game in which for every win there must be an equivalent loss?
There is not universal agreement on the names of the layers in the TCP/IP networking model. Which of the following is one of the functions of the bottom layer which is sometimes called the Network Access or Link Layer?
What is the function of the TTL (Time to Live) field in IPv4 and the Hop Limit field in IPv6 In an IP Packet header?
What requirement must an administrator remember when utilizing Security Configuration and Analysis (SCA) to apply security templates to Windows systems?
Which of the following is NOT typically used to mitigate the war dialing threat?
Which attack stage mirrors the Information Gathering phase used in penetration testing methodology?
Which of the following applications would be BEST implemented with UDP instead of TCP?
Which of the following are network connectivity devices?
Each correct answer represents a complete solution. Choose all that apply.
The Return on Investment (ROI) measurement used in Information Technology and Information Security fields is typically calculated with which formula?
Which command would allow an administrator to determine if a RPM package was already installed?
If you do NOT have an original file to compare to, what is a good way to identify steganography in potential carrier files?
Which AWS service integrates with the Amazon API Gateway to provision and renew TLS encryption needs for data in transit?
Which of the following is a Layer 3 device that will typically drop directed broadcast traffic?
Many IIS servers connect to Microsoft SQL databases. Which of the following statements about SQL server security is TRUE?