Assume a multicore processor with coherency management based on the MESI protocol. When a core changes the contents of a shared cache line, what is the final status of that line in the local cache?
In the Generic Interrupt Controller (GIC), when an interrupt is requested, but is not yet being handled, it is in which of the following states?
An Advanced SIMD intrinsic has the prototype:
uint8xl6x2_t vld2q_u8 (uint8_t const * ptr);
How many bytes does this intrinsic load from memory?
Consider the following instruction sequence:
STR r0, [r2] ; instruction A
DSB
ADD r0, r1, r2 ; instruction B
LDR r3, [r4] ; instruction C
SUB r5, r6, #3 ; instruction D
At what point will execution pause until the STR access is complete?
The following pair of functions implement a simple mutex spinlock which might be used to protect a critical code section in a multi-threaded application. The address of the lock variable is in r0.
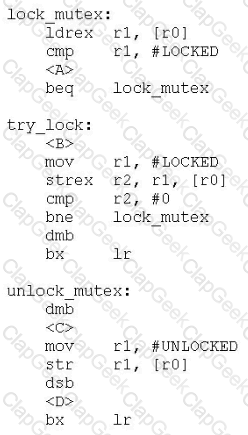
In order to minimize power while waiting for the lock to be available. SEV and WFE instructions can be used to place the processor in a low power state while waiting for the lock to become available. At which points should these instructions be placed?
A Just-In-Time compiler writes instructions to a region of memory that is configured using a writeback cache strategy. For the locations that have been written, what is the MINIMUM cache maintenance that MUST be performed before the new instructions can be reliably executed?
When developing a product using the standard ARM C library, what is the minimum effort required to re-target all platform-specific functions in the library?
In a Cortex-A9 processor, when the Memory Management Unit (MMU) is disabled, which of the following statements is TRUE? (VA is the virtual address and PA is the physical address)
According to the AAPCS, how many bytes are used to store a C variable of type 'int' in memory?
A C code segment contains three calls to a function, foobar ().
This code segment is to be linked with a static library that defines foobar ().
Ignoring inlining, how many copies of foobar () will the ARM linker place in the output?
According to the AAPCS, which of the following statements is TRUE with regard to preservation of register values by a function?
On an ARM processor that does not implement Security Extensions, which one of the following can be the starting address of the exception vector table?
In an ARMv7-A processor, with which level of the memory system is the Memory Management Unit (MMU) associated?
In the Generic Interrupt Controller (GIC) architecture, which of the following ID numbers are reserved for interrupts that are private to a CPU interface?
A message passing system between two CPUs is implemented using data stored in a shared area of memory. To pass a message, the first CPU executes the instructions:

The second CPU receives the message using the instructions:
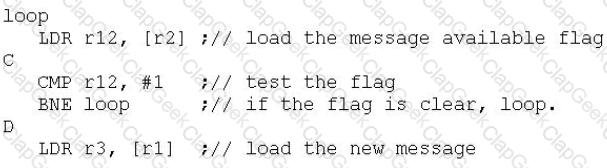
On both CPUs, r1 = 0x5000 and r2 = 0x6000. At which of the points A, B, C and D must Data Memory Barrier (DMB) instructions be placed in order to ensure messages are passed reliably and efficiently?
When using an Operating System, which of the following operations can NOT typically be done by user processes?
A simple method of measuring the performance of an application is to record the execution time using the clock on the wall or a wristwatch.
When is this method INAPPROPRIATE?
How many bytes of stack are needed to pass parameters when calling the following function?
int foo( short arg_a, long long arg_b, char arg_c, int arg_d )
For Cortex-A series cores, what instruction(s) are recommended to implement a mutex or semaphore?
Which of these C99 keywords can be used to indicate that two arrays do not overlap?