A developer has created a deployment that should launch a pod to run their database service. The pod should launch with a metadata name of “Cisco-DB," and the developer has added it to the "Cisco" namespace in their deployment.
Which Kubernetes command confirms that the service is running and usable?
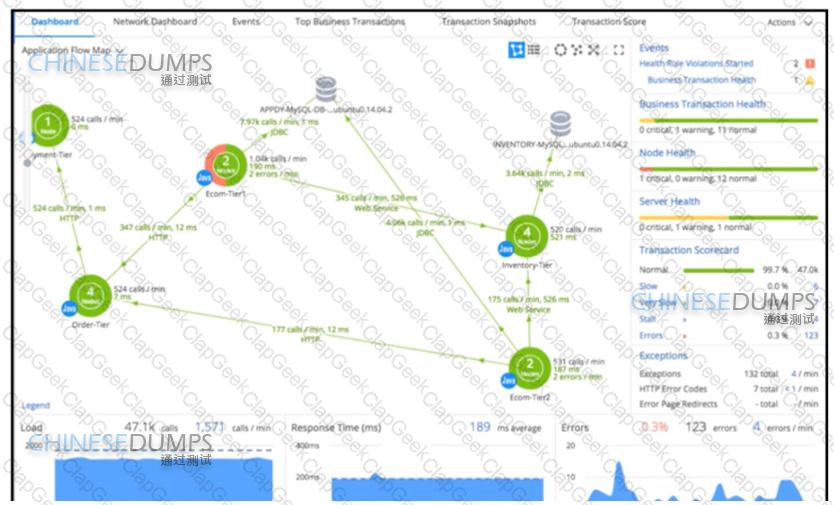
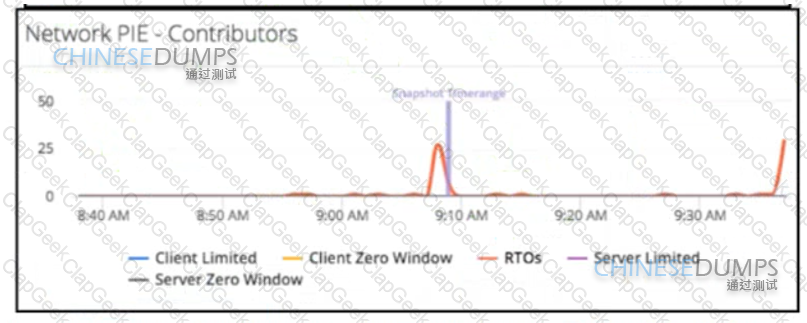
Refer to the exhibit A DevOps engineer is responsible for monitoring a mission-critical app During normal operations, when opening the application dashboard, it has been noticed that Ecom-Tier1 suddenly turns partially red Which action must be taken to address the Ecom-Tier1 turning red?
An application for storing and categorizing has been developed. The application uses dual-factor authentication for user access. After authentication, users can upload sensitive data. The application has been hacked through system exploits and most of the saved data has been lost.
Which action prevents new security threats in the environment?
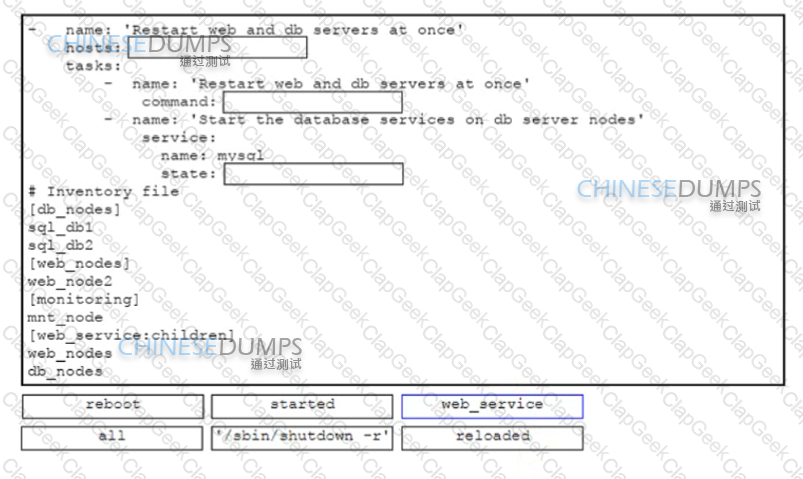
Drag and drop the code snippets from the bottom onto the boxes in the code in the Ansible playbook to restart multiple services in the correct sequence Not all options are used
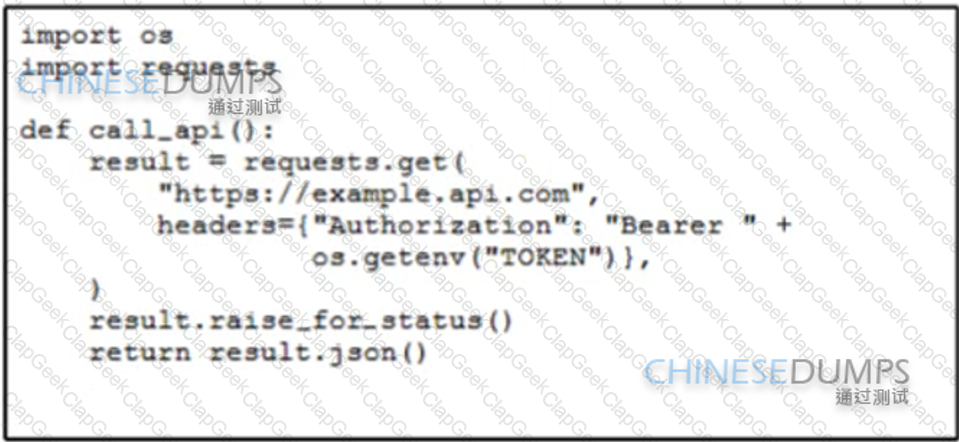
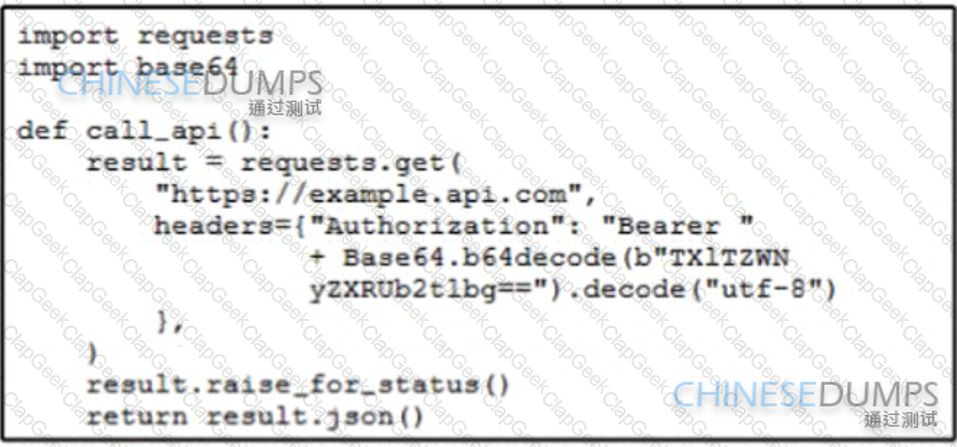
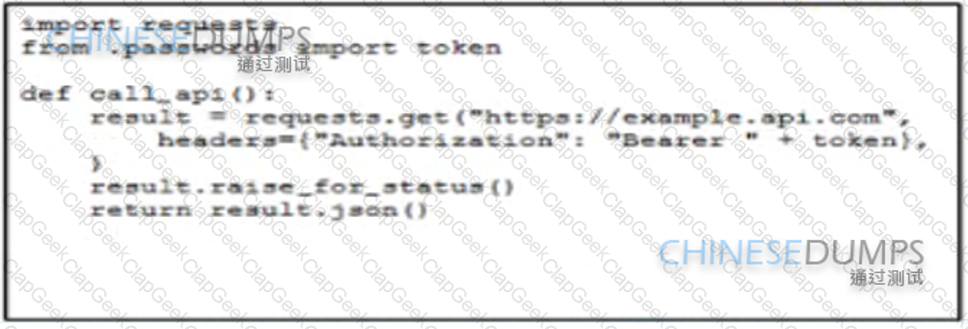
An engineer is developing a script that must call an API using a static Bearer token Which solution securely protects the credentials from being retrievable from the source code?
A)
A)
B)
C)

D)
Fill in the blanks to describe the concepts of extending DevOps practices to the network for NetDevOps.
NetDevOps builds and manages networks as a system that enables network services to be consumed in a DevOps approach. Organizations practicing NetDevOps see changes in the__________ as routine and expected activities, with a well-defined and practiced process for_____________, testing, and _____________ network changes. By making them routine, network changes can be small and simple.
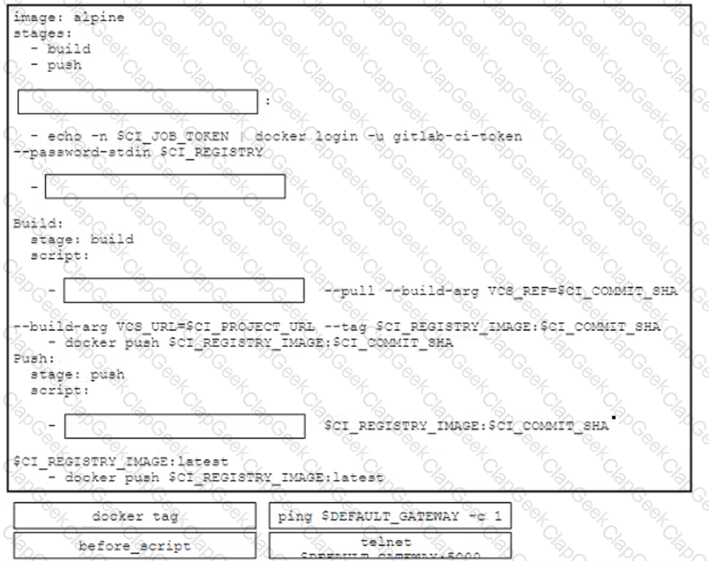
A DevOps engineer is designing a precheck validation of the network state in a CI/CD pipeline and must implement this workflow:
• Take a source Docker image named alpine
• Define two stages named build and push
• Check network connectivity before the stages run
• Fetch the latest Docker image
• Create a new Docker image and push it to the registry
• Tag the new Docker image as the latest version
Drag and drop the code snippets from the bottom onto the boxes in the GitLab CI configuration to achieve the requirements for the design. Not all options are used.
A security team is running vulnerability scans against a CI/CD pipeline. The reports show that RDBMS secrets were found hardcoded in Ansible scripts. The RDBMS resides in the internal network but is accessible from a jump server that resides in a public network.
If an attacker gains access to the scripts, what is the risk exposure?
An organization is developing an application using Git. Each team member is assigned to work on specific parts of the application. At the end of each task, individual code parts are merged in the main build.
Which two requirements should be implemented to increase the likelihood of continuous integration? (Choose two.)
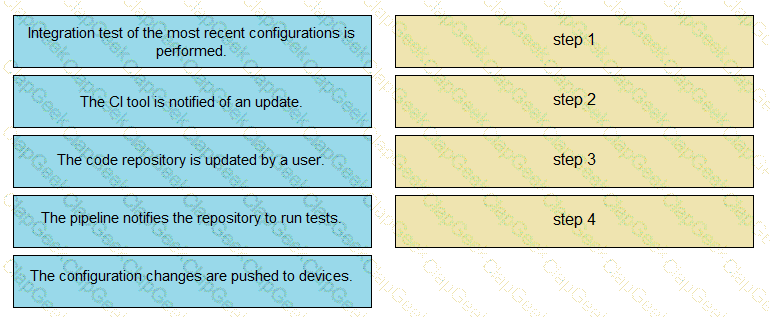
The IaC configuration for an application is being deployed using a CI/CD pipeline. Drag and drop the steps for this pipeline from the left into the correct order that they would be executed on the right. Not all options are used.
A team is developing an application for end users. The application will use microservices. For user access, dual-factor authentication will be used. Which type of test must be performed by the CI/CD tool to replicate user behavior and to verity that various user actions work as expected?
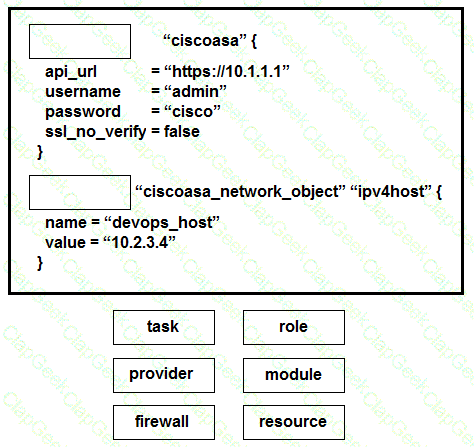
Drag and drop the commands from the bottom onto the correct Terraform code in the exhibit to push a network object to a Cisco ASA Firewall device.
An end user is seeing long web page load times on the internal business application that they are trying to view. The user is seeing this issue across multiple web browsers, and other users encounter the same issue. Which action should the system administrator take to start looking for the cause of this issue?
Which type of testing should be integrated into a CI/CD pipeline to ensure the correct behavior of all of the modules in the source code that were developed using TDD?
A developer is creating an application based on microservices. The application will be used as a central repository for all company's documents. One of the microservices in the application will perform image processing. This microservice must autoscale to meet the current load and avoid down time.
Which metric must be used to trigger autoscaling events?
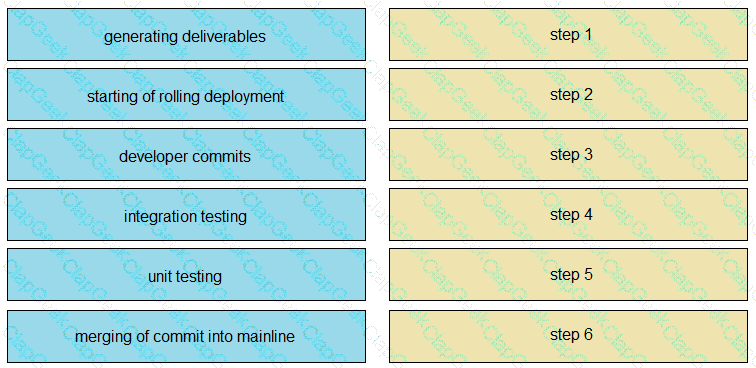
Drag and drop the operations from the left into the correct order on the right when using CI/CD, assuming that there are no failures or conflicts.
A development team uses Kubernetes for application development. Any changes on ConfigMap are performed manually for each development, test, and production environment. The edits are performed to deploy applications. This approach causes inconsistent deployments across all environments.
Which practice improves the consistency of the deployments?
Refer to the exhibit.
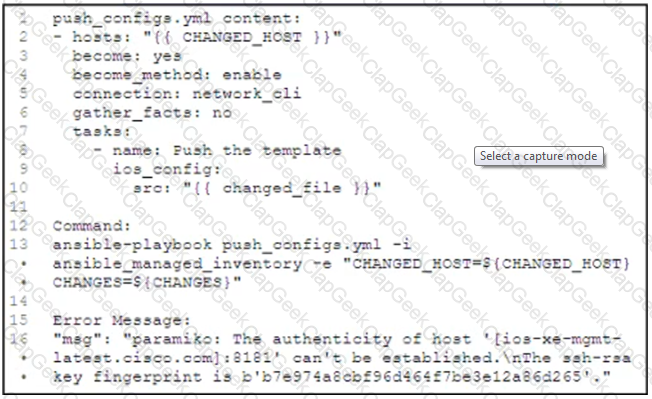
The push_configs.yml playbook returns the error shown.
Which action resolves the error?
A DevOps engineer must validate the working state of the network before implementing a CI/CD pipeline model. Which configuration management tool is designed to accomplish this?
What is an advantage of using configuration management tools to automate infrastructure services?
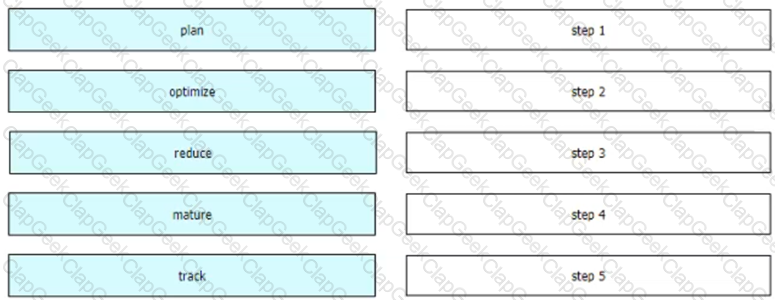
Drag and drop the steps in Gartner's public cloud cost management framework from the left into the order on the right.
A CI/CD pipeline that builds infrastructure components using Terraform must be designed. A step in the pipeline is needed that checks for errors in any of the .tf files in the working directory. It also checks the existing state of the defined infrastructure.
Which command does the pipeline run to accomplish this goal?
Refer to the exhibit.

A Python script implements a logger server. The log receives a message from Base that contains this text: TextMessage. How is the log formatted?
Refer to the exhibit.
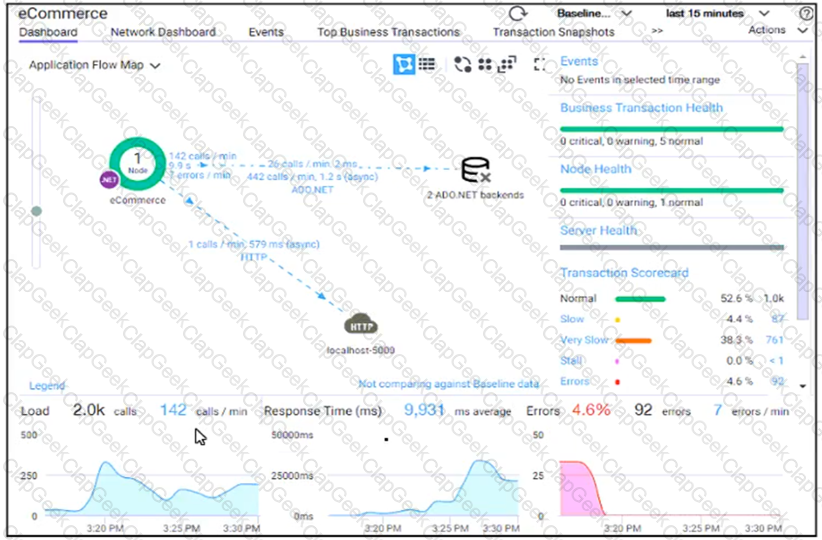
An application for data storing and processing has been created. The application is time-sensitive and manages confidential data AppDynamics identifies error transactions within a distributed application.
Which action will help resolve the errors?
A user wants to deploy a new service to a Kubernetes cluster. Which two commands accomplish this goal? (Choose two.)
Refer to the exhibit.
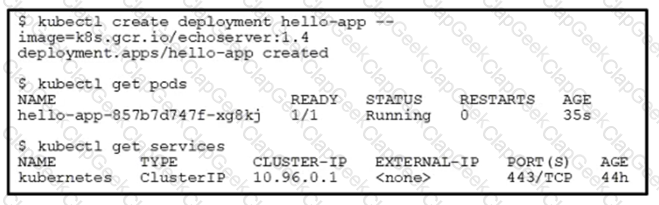
Which action allows the development team to reach the deployed application?
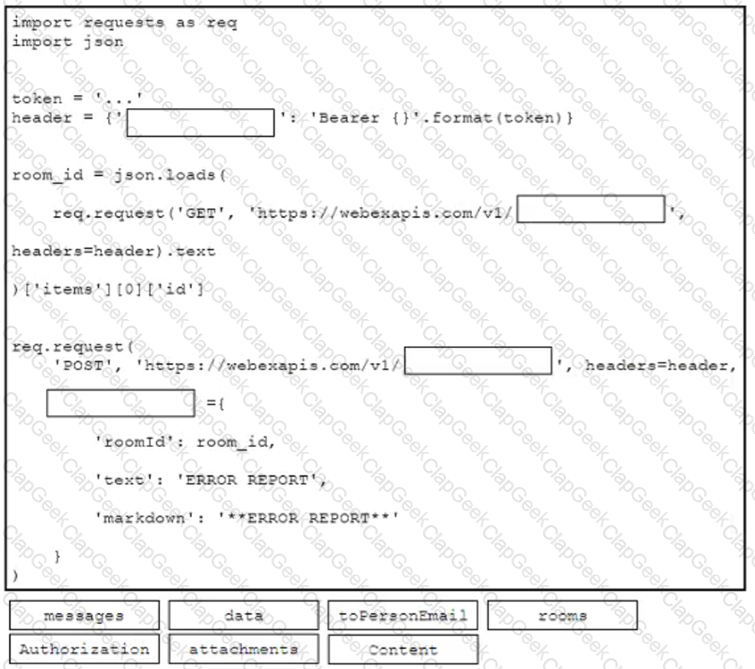
Drag and drop the code from the bottom onto the box where the code is missing to post a message to a Cisco Webex space. Not all options are used.
Which two characteristics of a build tool that is used in an automated build pipeline? (Choose two.)
To make logging searches more efficient and useful in Kibana, an Administrator wants to implement index patterns around the hostname of some software systems. Where should this be configured?


