A developer has just completed the configuration of an API that connects sensitive internal systems. Based on company policies, the security of the data is a high priority.
Which approach must be taken to secure API keys and passwords?
Refer to the exhibit.
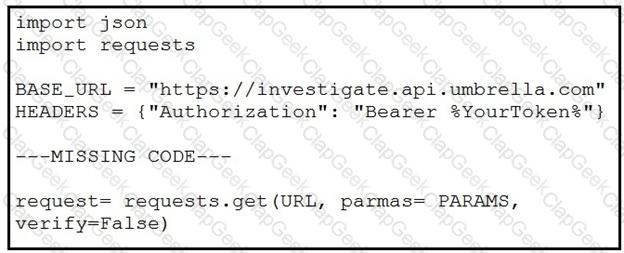
A network operator must create a Python script that makes an API request to Cisco Umbrella to do a pattern search and return all matched URLs with category information.
Which code completes the script?
After changes are made to the Cisco Firepower Threat Defense configuration using the Cisco Firepower Device Manager API, what must be done to ensure that the new policy is activated?
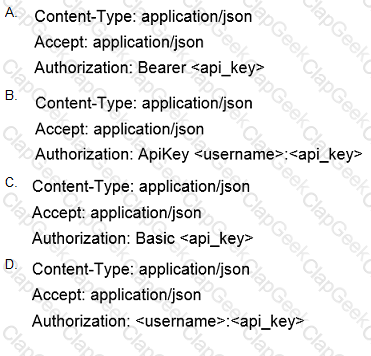
Which header set should be sent with all API calls to the Cisco Stealthwatch Cloud API?
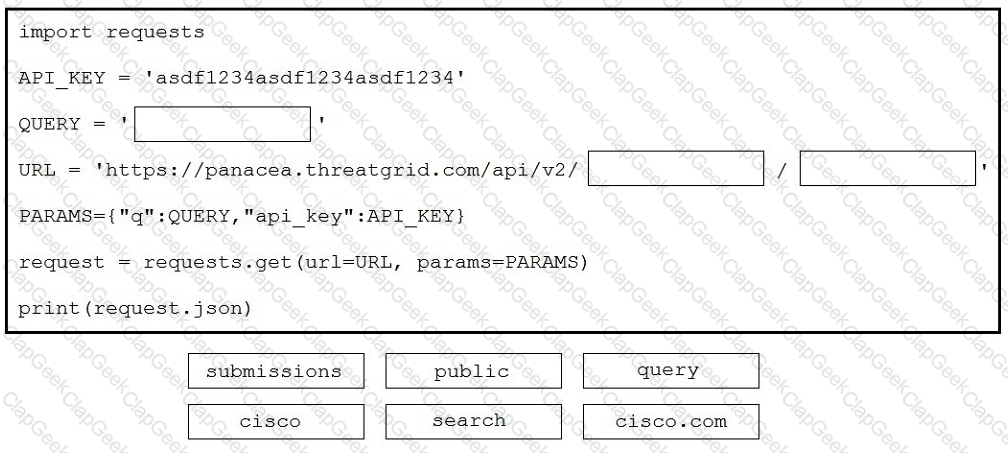
Drag and drop the code to complete the script to search Cisco ThreatGRID and return all public submission records associated with cisco.com. Not all options are used.
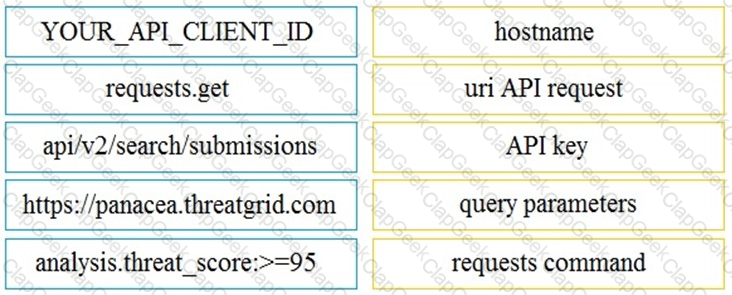
Refer to the exhibit.
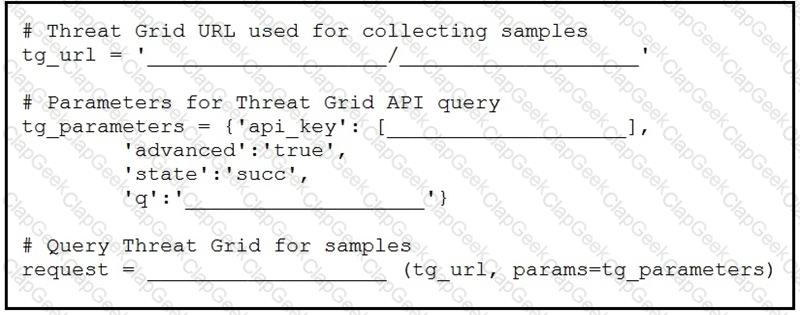
Drag and drop the elements from the left onto the script on the right that queries Cisco ThreatGRID for indications of compromise.