The Samba configuration file contains the following lines:
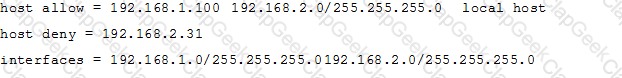
A workstation is on the wired network with an IP address of 192.168.1.177 but is unable to access the Samba server. A wireless laptop with an IP address 192.168.2.93 can access the Samba server. Additional trouble shooting shows that almost every machine on the wired network is unable to access the Samba server.
Which alternate host allow declaration will permit wired workstations to connect to the Samba server without denying access to anyone else?
Which of the following values can be used in the OpenLDAP attribute olcBackend for any object of the class olcBackendConfig to specify a backend? (Choose three.)
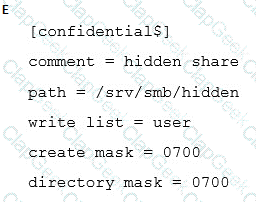
A user requests a “hidden” Samba share, named confidential, similar to the Windows Administration Share. How can this be configured?


To allow X connections to be forwarded from or through an SSH server, what configuration keyword must be set to yes in the sshd configuration file?
The content of which local file has to be transmitted to a remote SSH server in order to be able to log into the remote server using SSH keys?
In the main Postfix configuration file, how are service definitions continued on the next line?
What command displays NFC kernel statistics? (Specify ONLY the command without any path or parameters.)
How must Samba be configured such that it can check CIFS passwords against those found in /etc/passwd and /etc/shadow?
Which of the following commands can be used to connect and interact with remote TCP network services? (Choose two.)
In response to a certificate signing request, a certification authority sent a web server certificate along with the certificate of an intermediate certification authority that signed the web server certificate. What should be done with the intermediate certificate in order to use the web server certificate with Apache HTTPD?
When trying to reverse proxy a web server through Nginx, what keyword is missing from the following configuration sample?

The following Apache HTTPD configuration has been set up to create a virtual host available at www.example.com and www2.example.com:
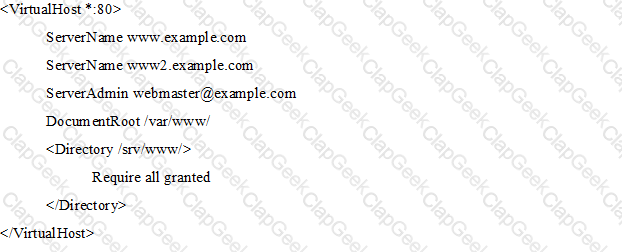
Even though Apache HTTPD correctly processed the configuration file, requests to both names are not handled correctly. What should be changed in order to ensure correct operations?
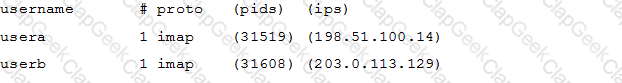
Which doveadm sub-command displays a list of connections of Dovecot in the following format? (Specify ONLY the command without any parameters.)
What option in the client configuration file would tell OpenVPN to use a dynamic source port when making a connection to a peer?
What is the name of the network security scanner project which, at the core, is a server with a set of network vulnerability tests?
In order to specify alterations to an LDAP entry, what keyword is missing from the following LDIF file excerpt?

Specify the keyword only and no other information.
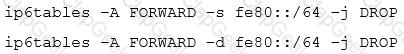
Which of the statements below are correct regarding the following commands, which are executed on a Linux router? (Choose two.)
How is the LDAP administrator account configured when the rootdn and rootpw directives are not present in the slapd.conf file?
Which of the following actions are available in Sieve core filters? (Choose three.)
A company is transitioning to a new DNS domain name and wants to accept e-mail for both domains for all of its users on a Postfix server.
Which configuration option should be updated to accomplish this?
Which option within the ISC DHCPD configuration file defines the IPv4 DNS server address(es) to be sent to the DHCP clients?
Which action in a Sieve filter forwards a message to another email address without changing the message? (Specify ONLY the action’s name without any parameters.)
The program vsftpd, running in a chroot jail, gives the following error:

Which of the following actions would fix the error?
Using its standard configuration, how does fail2ban block offending SSH clients?
Which command is used to configure which file systems a NFS server makes available to clients?


