A new application is being developed that must be hardware independent. The application includes an administrative component which is accessed using a Windows desktop GUI. Installation and management of the environment must be fully automated. Which application deployment type meets the requirements?
Refer to the exhibit.
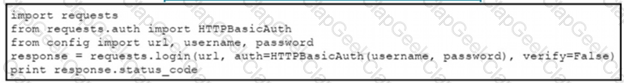
The script returns an output of 401. To use the supplied URL. an HTTP GET request must Be sent with an Authorization header. The header value is a BaseG4 encoded concatenation of the username and password. Which action must be taken to return an output of 200?
Refer to the exhibit.
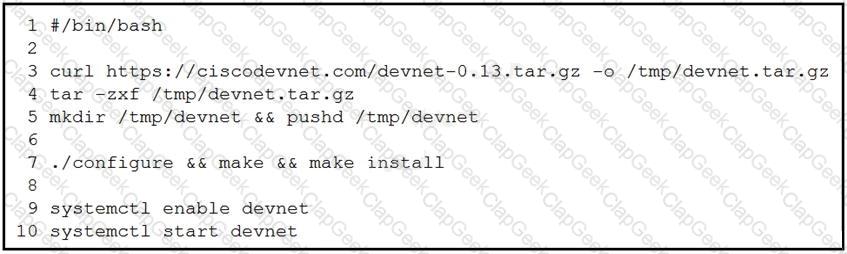
A network engineer works on a Cisco DevNet application that is available for download on the Cisco DevNet website. The engineer prepares a bash script to automate operations that relate to the application. Which workflow is being automated in the bash script?
A developer created a new secure API and is testing the functionality locally. The API was added to a container for further testing, and other team members and applications need to connect to the API. Which command exposes the API in the container as port 8443 and allows connections external to the host?
Which platform is used to programmatically create a space and invite users for collaboration?
Refer to the exhibit.

Which JSON snippet configures a new interface according to YANG model?
A)
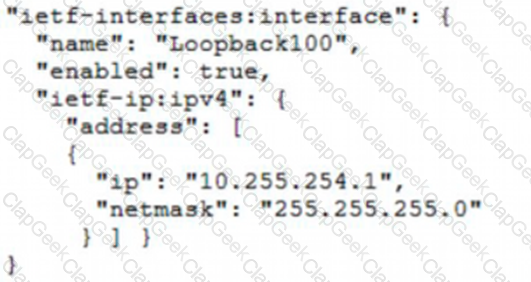
B)
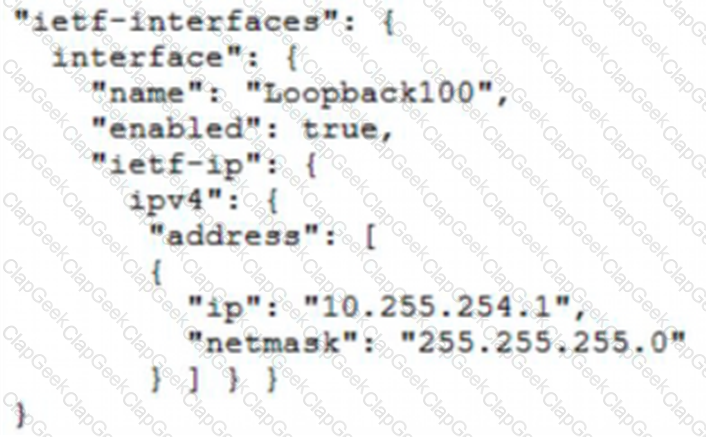
C)
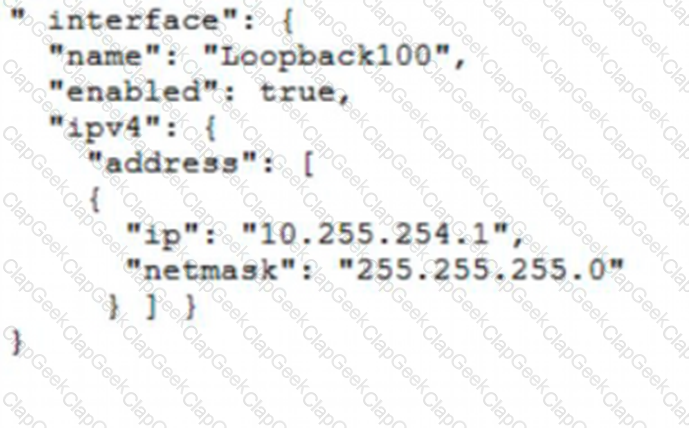
D)
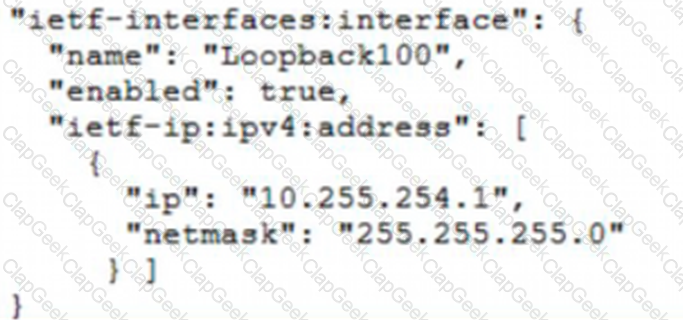
Refer to the exhibit.
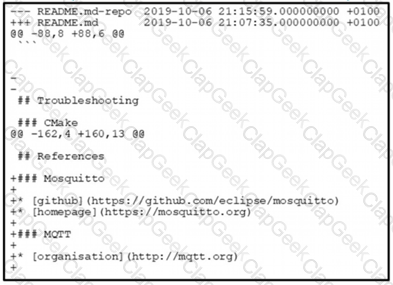
The output of the diff-u README.md-repo README.md command is shown. The original file was 165 lines long How many lines are in the edited copy of the file?
Refer to the exhibit.
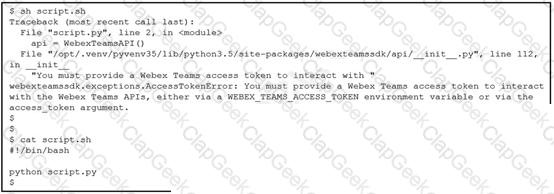
Which line must be included in the Bash script for the Python code to succeed?
Refer to the exhibit.
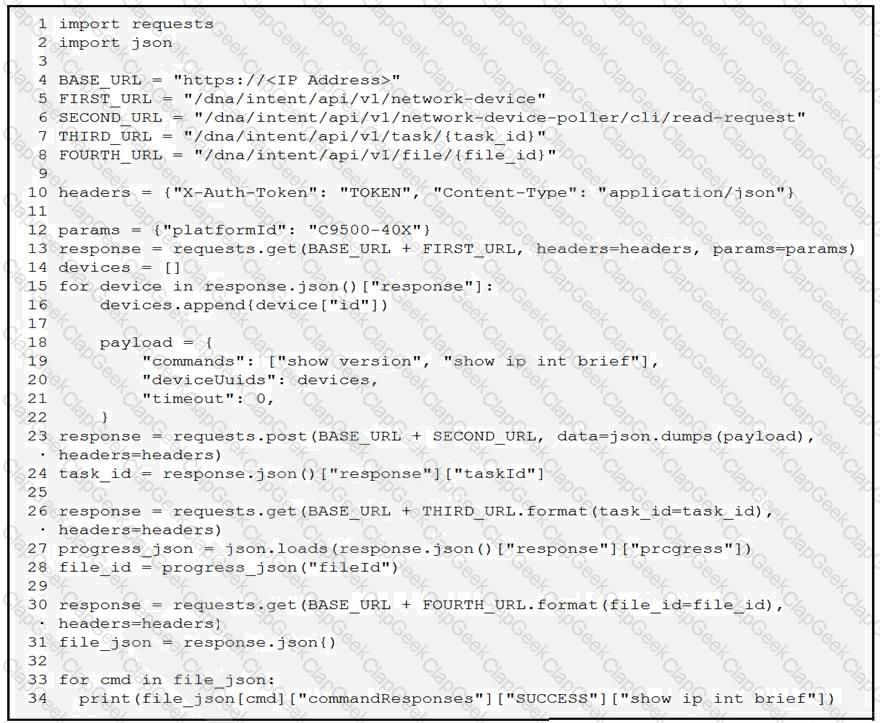
A network engineer must collect information from the network using Cisco DNA Center APIs. The script must query for the devices with 'platformId' 'C9540-x' and then send commands to be executed. Which process is automated by the Python script?
Which HTTP code group is issued when a request is received successfully, understood, and processed?
Refer to the exhibit.
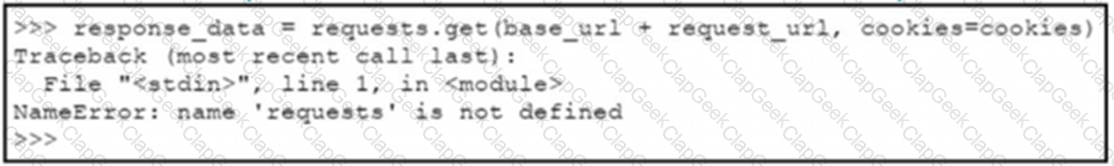
A Python code has been written to query a device. The executed code results in the error shown. Which action resolves the problem?
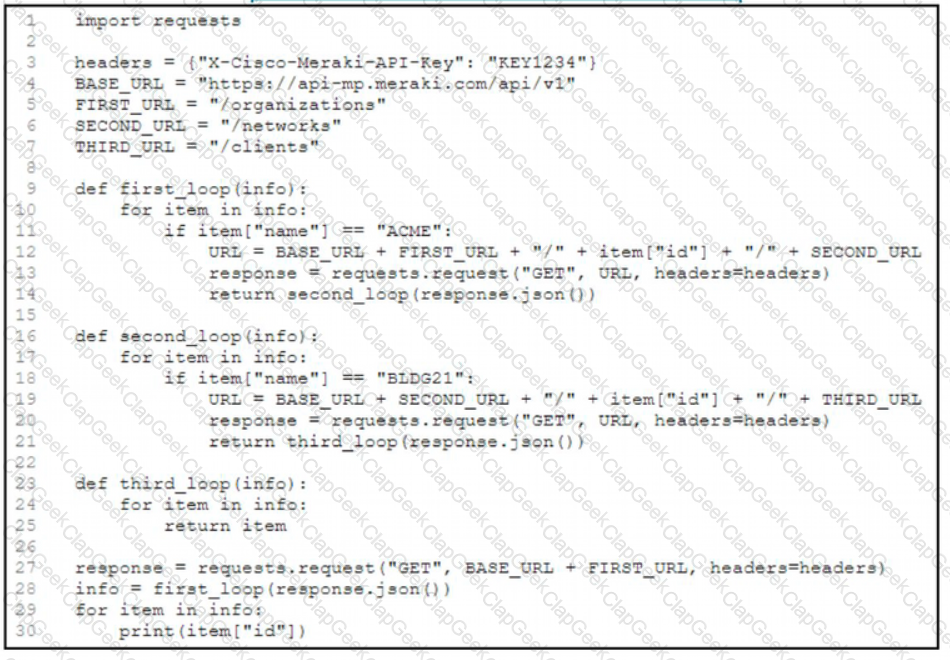
Refer to the exhibit. A network engineer must collect information from the network. The engineer prepares a script to automate workflow by using Cisco Meraki API. The script must run over nested loops to collect organization and network information and uses the collected data for final collection. Which process is being automated by using the Python script?
Refer to the exhibit.
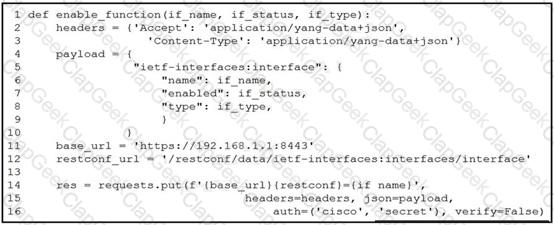
A network engineer wants to automate the port enable/disable process on specific Cisco switches. The engineer creates a script to send a request through RESTCONF and uses ietf as the YANG model and JSON as payload. Which command enables an interface named Loopback1?
Several teams at a company are developing a new CRM solution to track customer interactions with a goal of improving customer satisfaction and driving higher revenue. The proposed solution contains these components:
• MySQL database that stores data about customers
• HTML5 and JavaScript UI that runs on Apache
• REST API written in Python
What are two advantages of applying the MVC design pattern to the development of the solution? (Choose two.)
A developer creates a web application that receives a username and password and uses them to sync the credentials to other services through HTTPS. API keys to services are part of the configuration files of the application, but the credentials to the database that stores the synchronization logs are obtained through an external vault service. What is the security issue in this scenario?
Refer to the exhibit.
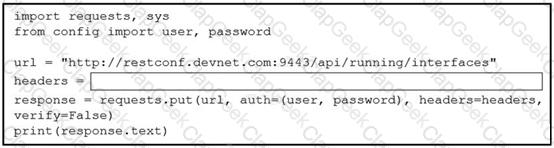
A network engineer wants to use an API to update information about device interfaces. The network devices are deployed in a Cisco DevNet Sandbox and have running interfaces. Which line of code needs to be placed in the snippet where the code is missing?
How does a developer create and switch to a new branch called "my-bug-fix" to develop a product fix?
Refer to the exhibit.
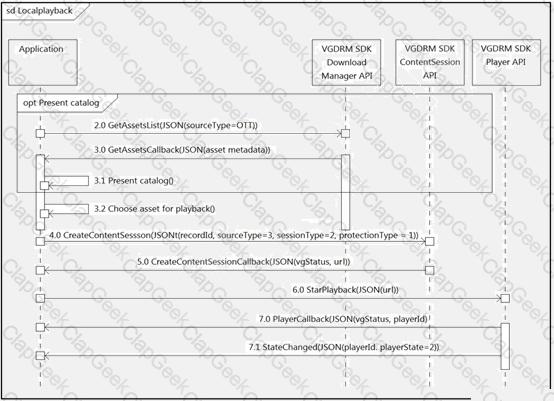
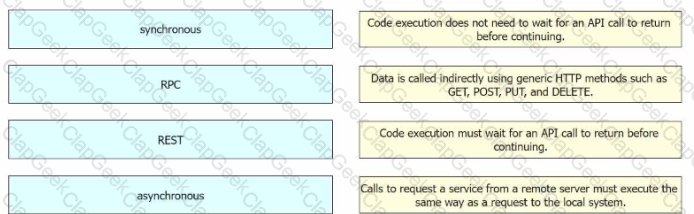
What do all the calls shown in the sequence diagram have in common?
Which tool is used to block all traffic to the domain by using a single API call?
Refer to the exhibit.
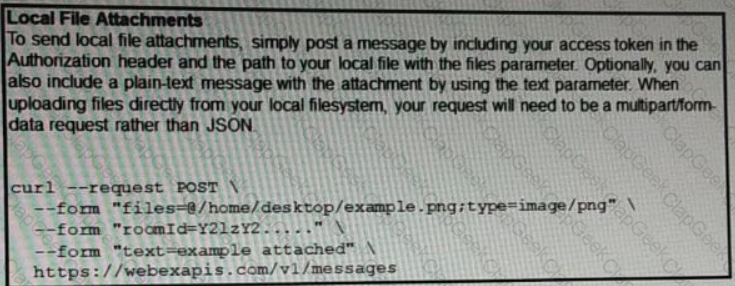
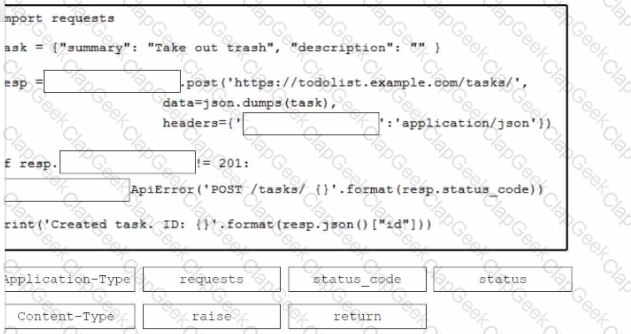
A developer needs to upload a local file by using the REST API. The developer gathers information according to the documentation and sends the request by using the cURL command in the exhibit but gets an error code. Which action should be followed to get valid response?
Refer to the exhibit.
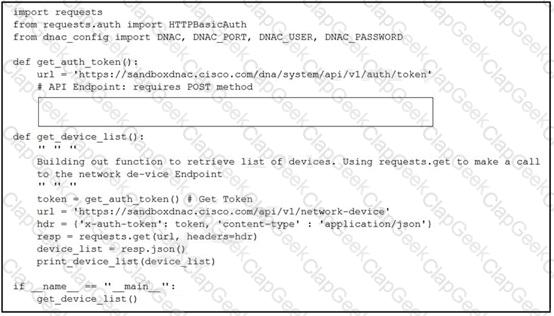
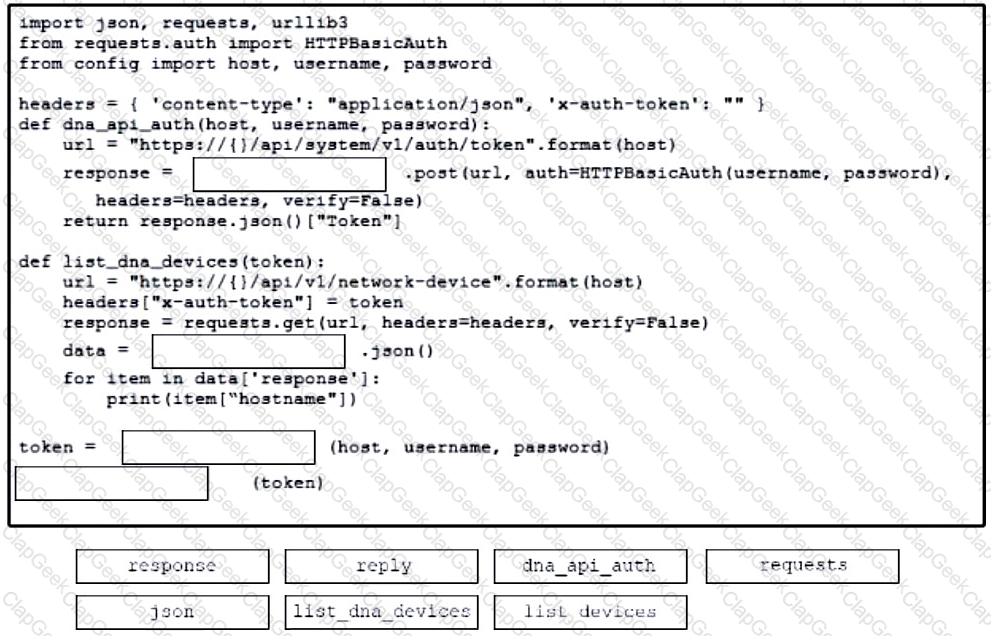
A developer creates a script to obtain a list of devices by using the Cisco DNA Center API. The remote server authorizes the request only if an authentication token is supplied in the headers. A function named get_auth_token() must retrieve a valid token by using HTTP Basic Authentication. Which code must be added to complete the get_auth_token() function?
A developer has created a new image to use in a Docker build and has added a tag for the image by using the command:
$ docker tag 84fe411926287 local/app:0.4
Which command must be executed next to build the Docker image using the tag?
Refer to the exhibit.
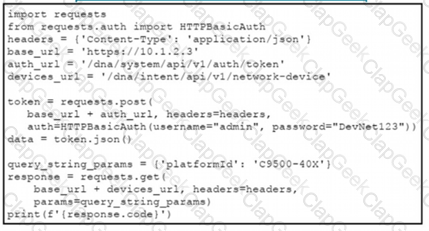
A network engineer must manage the network devices. The engineer prepares a Python scripts to authenticate to the Cisco to DNA Center API and request a device list. The device request fails and returns errors code 401. Which action solves the problem?
Refer to the exhibit.
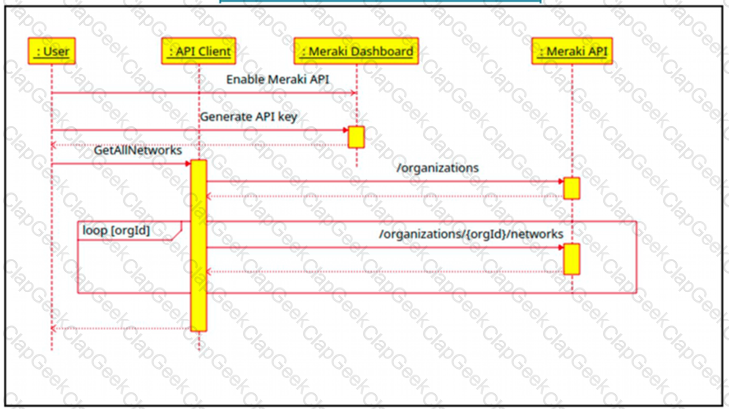
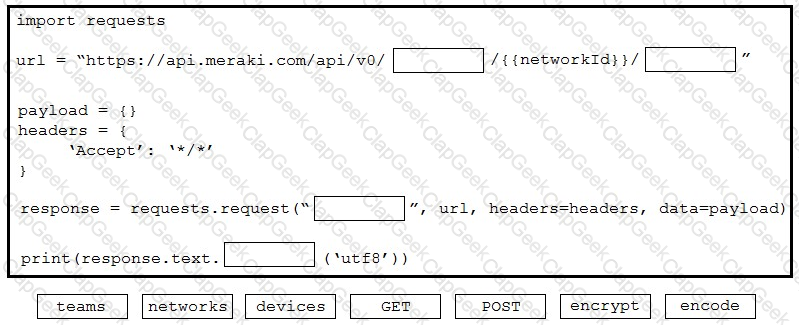
The Cisco Meraki API manages two organizations. In each organization, two independent networks are defined. How many calls to the /organizations/(orgid)networks endpoint will be run parallel by the GetAllNetwork function of the API client?
Refer to the exhibit.

A network engineer must change the configuration on devices daily. The Python script must collect CLI arguments from the user, organize data according to the Cisco-IOS-XE-native YANG model, and utilize Cisco REST APIs to make the configuration. Which workflow is being automated by the Python script?
Refer to the exhibit.
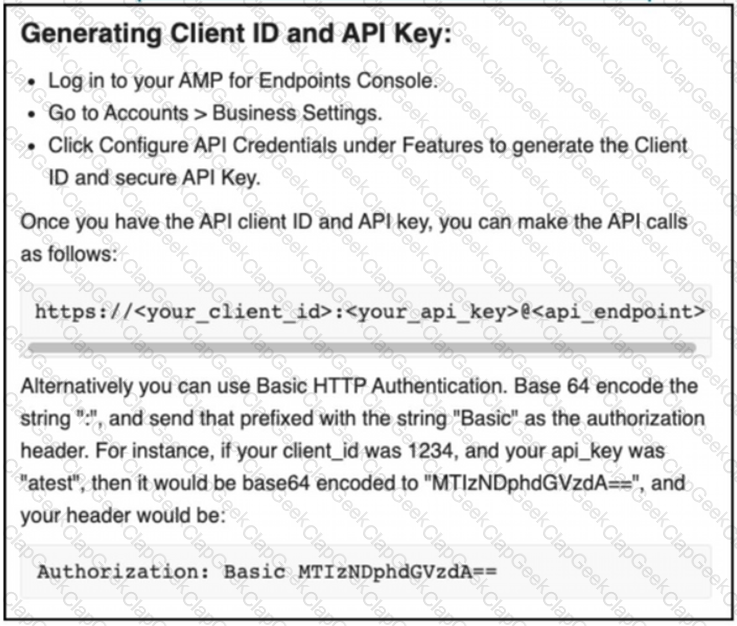
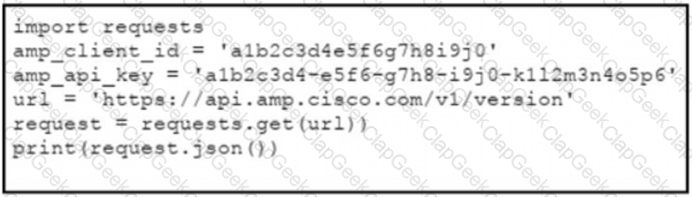
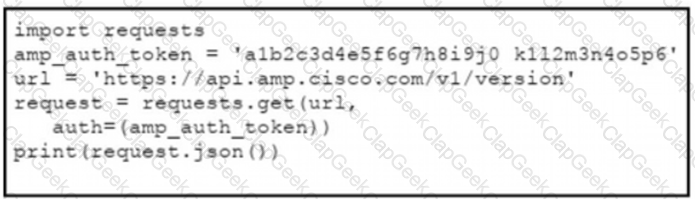
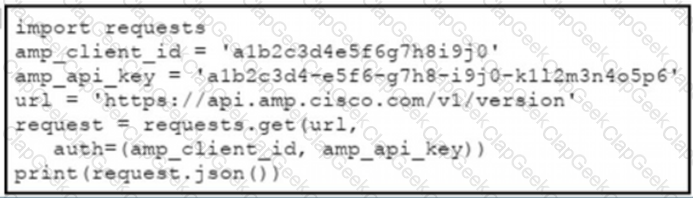
The documentation outlines how to use credentials for the AMP API Which script successfully performs an API call using basic authentication?
A)
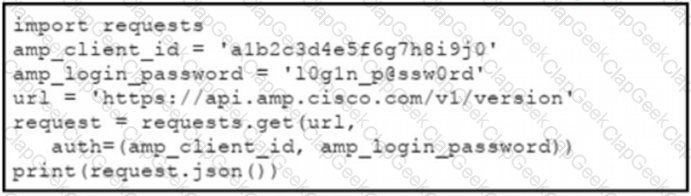
B)
C)
D)
Refer to the exhibit.
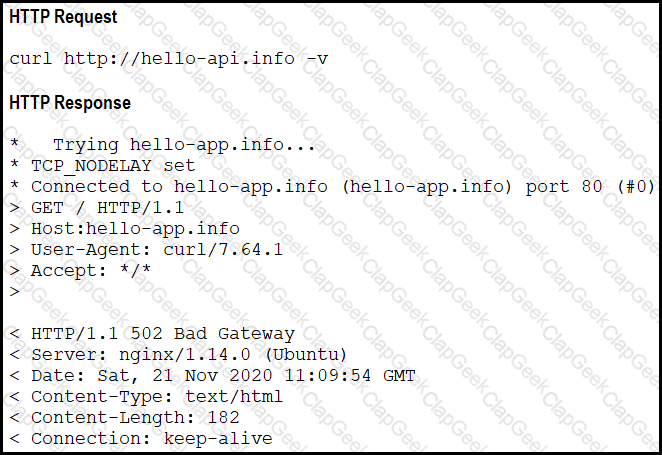
A developer cannot reach the web application behind an NGINX load balancer. The developer sends a request to an application FQDN with cURL but gets an HTTP 502 response. Which action solves the problem?
A developer must test the performance and reliability of an application. After functional and load tests are run, the application crashes due to traffic spikes from users. Which type of API constraint must be implemented to maintain reliability?
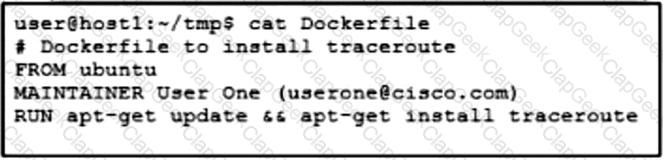
Refer to the exhibit. Drag and drop the Dockerfile contents from the left onto the functions on the right that create a container image to run traceroute to track network path to specific targets. Not all options are used.
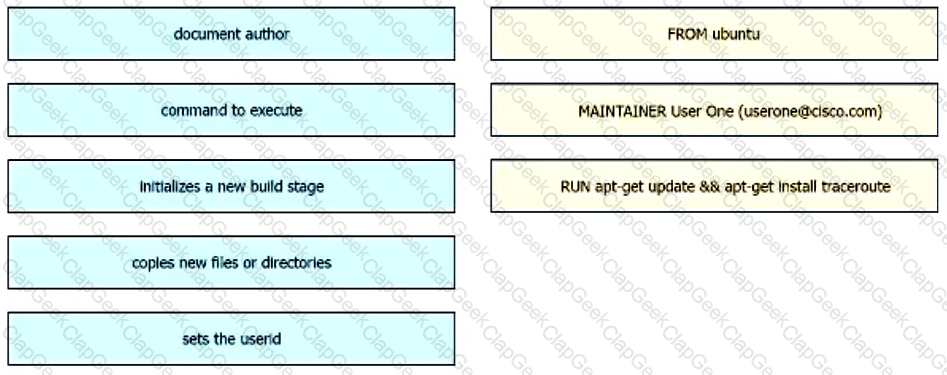
Refer to the exhibit.
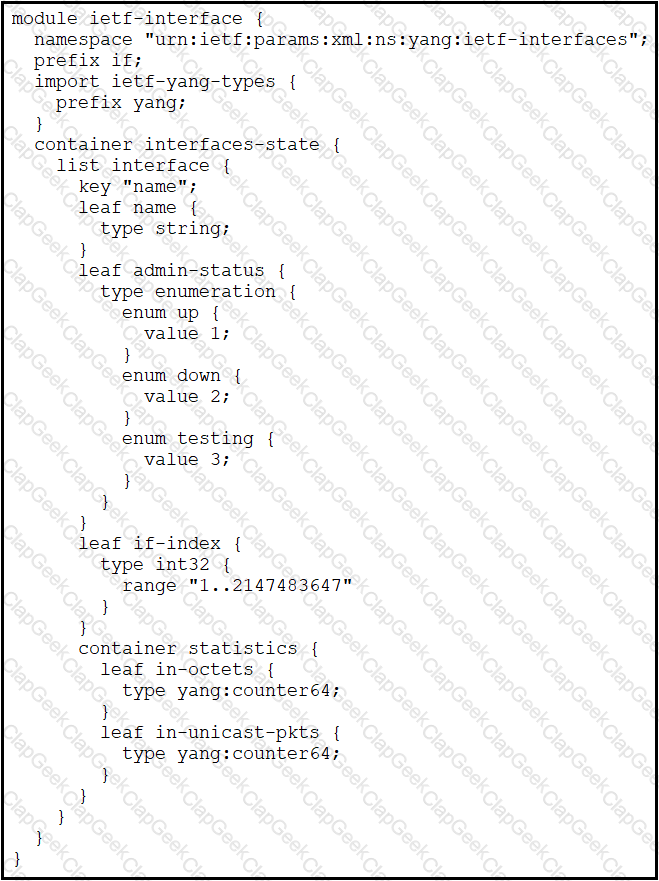
Which XML snippet has interface information that conforms to the YANG model?
A)
B)
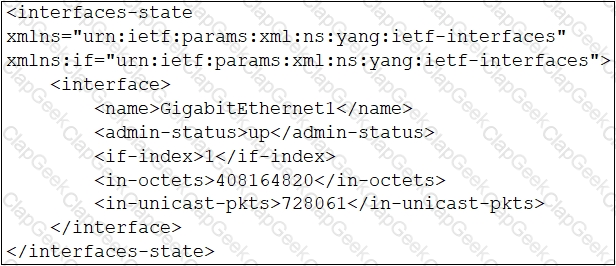
C)
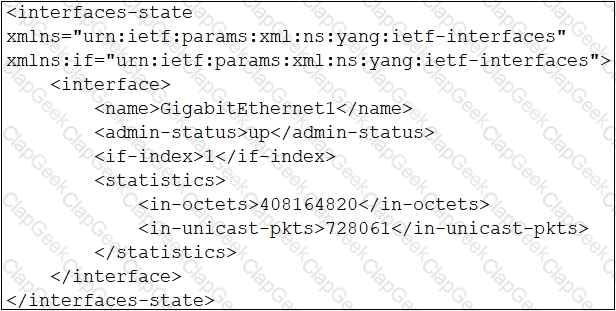
D)
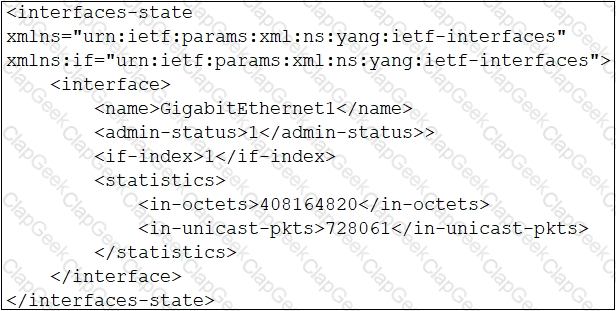
A developer attempts to refactor and improve the application code. It is noticed that the code contains several pieces of key information that could be a security threat if this code is accessible by those who are not
authorized to this data. Which approach addresses the security concerns noticed by the developer?
A developer is running an application that connects to the Cisco website and collects data. The application will be hosted in a local data center and the data will need to be collected on a frequent basis. The application client requires certain environmental variables to be set before the run. Which Bash command sets the environmental variables for a Linux system?
A developer creates an application that must provide an encrypted connection or API keys. The keys will be used to communicate with a REST API. Which command must be used for the secure connection?
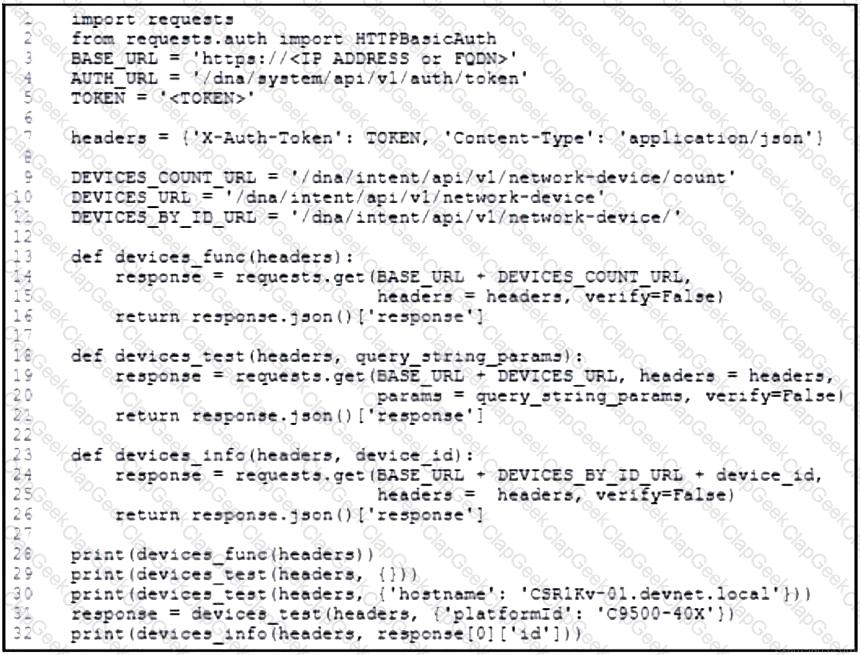
Refer to the exhibit. An engineer prepares a script to automate workflow by using Cisco DNA Center APIs to display:
total count of devices
list of the network devices
information of one device with a hostname filter
What is displayed in the final step after the Python script is executed?
Which type of OWASP threat forges a malicious HTTP request into an application?
A group of software developers wants to improve its collaboration with the operations team. The group wants to deliver release-ready code that merges code changes back to the main branch and runs the automated testing as often as possible. Which DevOps concept does this scenario represent?
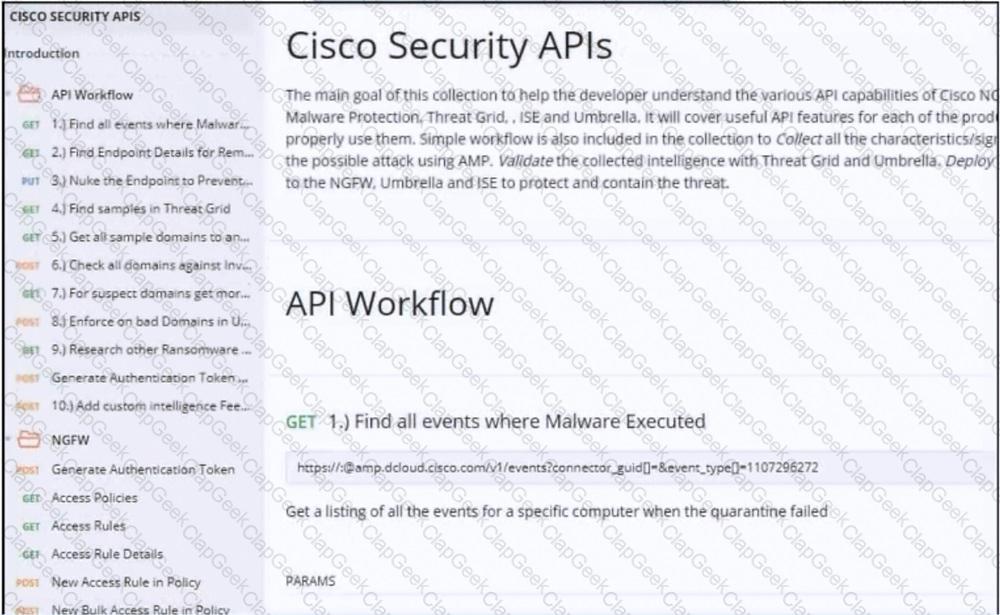
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script that calls a REST API request. Not all options are used.
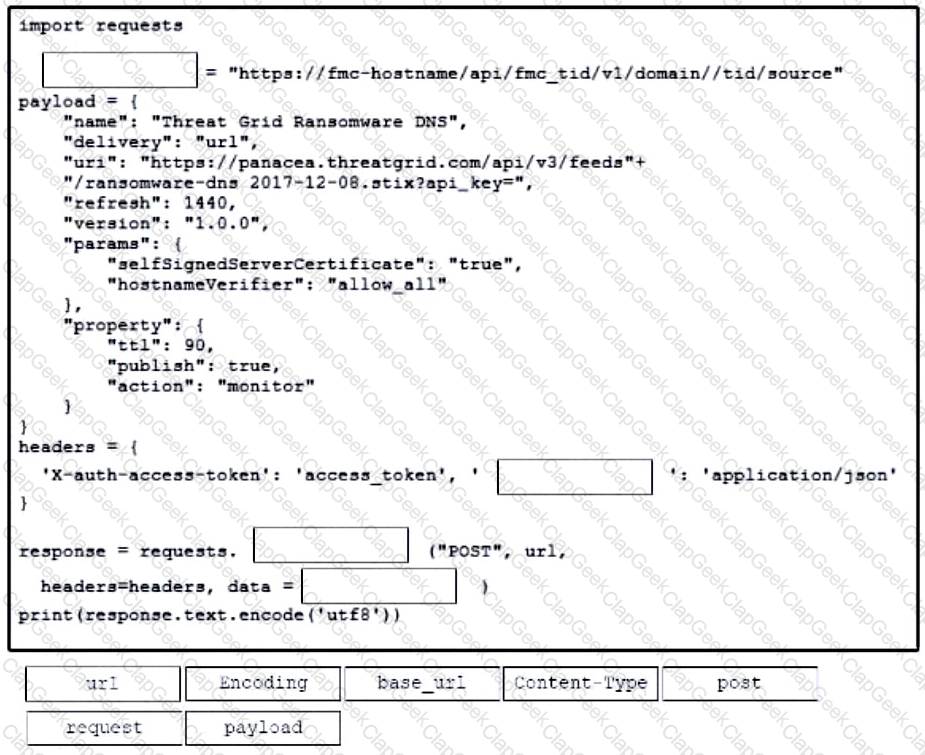
Refer to the exhibit. A network engineer executes the bash script shown. Which two things are achieved by running the script? (Choose two.)
Refer to the exhibit.
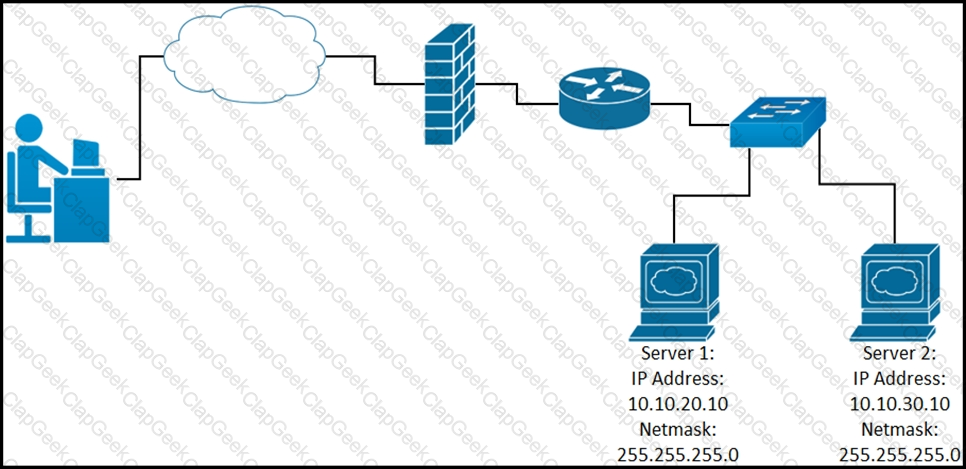
While developing a Cisco Webex bot, an application reaches the public IP address of the firewall, but traffic is forwarded to the IP address of server 1 instead of the IP address of server 2. What causes this issue?
Users cannot access a webserver and after the traffic is captured, the capture tool snows an ICMP packet that reports "time exceeded in-transit". What is the cause of this webserver access issue?
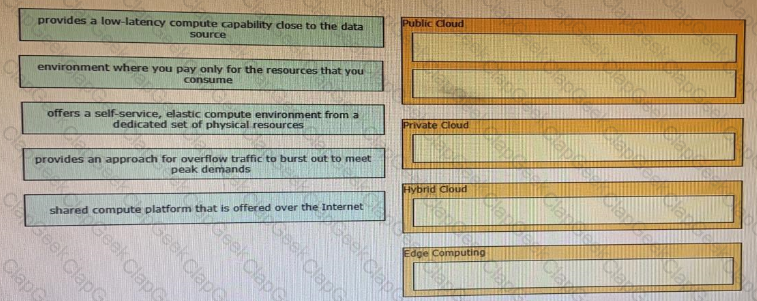
Drag and drop characteristics from the left onto the infrastructure management methodologies on the right.
A development team is creating an application used for contactless payments. The application must:
Be web-based
Capture and process the credit card information for a purchase.
Which security action must the web application use to gather and process the private customer data?
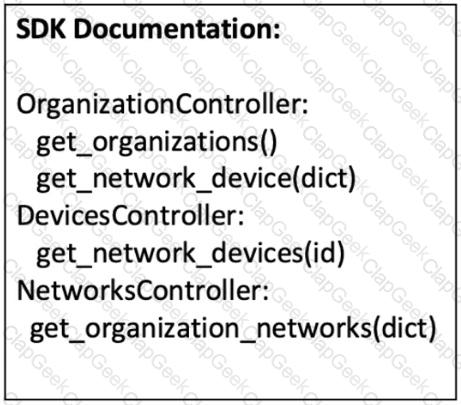
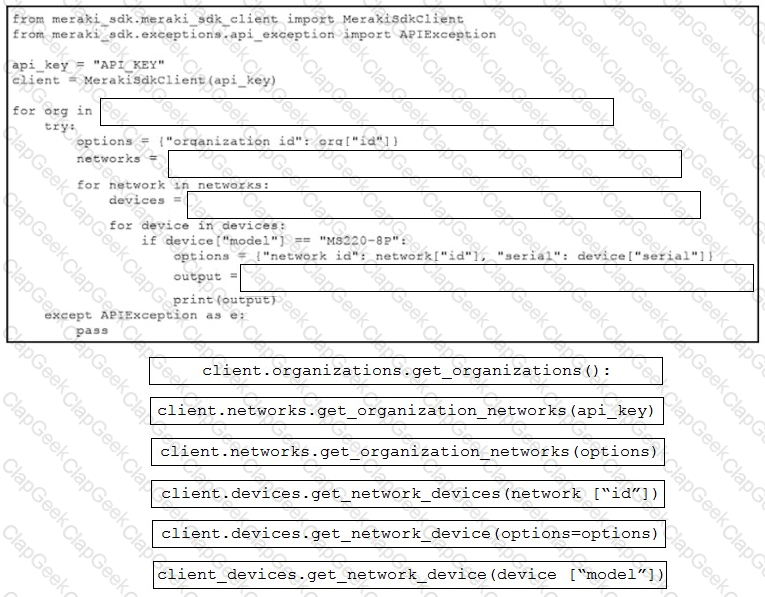
Refer to the exhibit. A script must output details of all the Cisco Meraki MS220-BP switches across all organizations and networks. Drag and drop the code snippets from the bottom onto the boxes in the code to complete the script. Not all options are used.
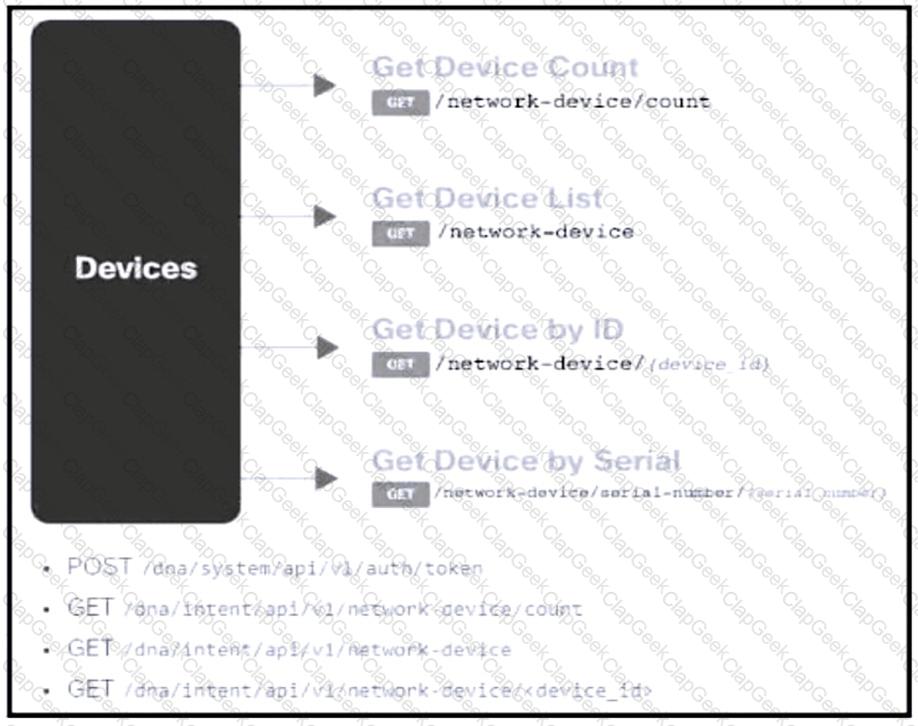
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to construct a request that generates a security token and gets a list of network devices. Not all options are used.
What is the impact on an application from having a large distance between a client device and a host server?
Which Cisco compute management platform controls server, network, storage, and virtual resources with policy-driven management for up to 10000 physical Cisco servers?
A developer checks the performance of a web application. The application is in the local data center and uses a REST-based API. Based on the API logs, it is discovered that many its abandon API requests. Also, the response is taking too long to get back. What is the reason for this issue?
Drag and drop the code from the bottom onto the box where the code is missing to obtain a list of network devices by using the Cisco Meraki API. Not all options are used.
A team of developers is responsible for a network orchestration application in the company. The responsibilities also include:
developing and improving the application in a continuous manner
deployment of the application and management of CI/CD frameworks
monitoring the usage and problems and managing the performance improvements
Which principle best describes this DevOps practice?
When a Cisco IOS XE networking device is configured by using RESTCONF, what is the default data encoding method?
Which two situations align with infrastructure as code principles? (Choose two.)
A developer is developing a web application that uses username and password to authenticate to the next service. The user credentials must be available at any time in the application. The developer must choose and implement a secure method of storing the authentication credentials that are used in the automation code. Which password handling method must be used to minimize the security risk?
Refer to the exhibit.

What are two results of running the RESTCONF query? (Choose two.)
Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script that calls a REST API request. Not all options are used.
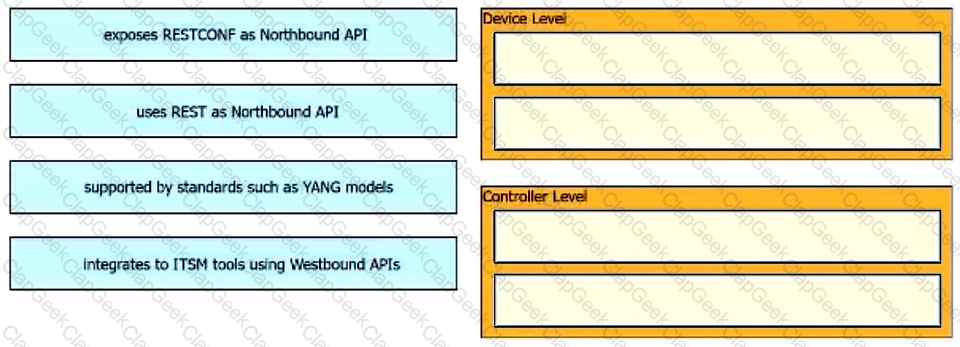
Drag and drop the common API styles from the left onto the requirement on the right.
What is a capability of model-driven programmability for infrastructure automation?
Refer to the exhibit. Drag and drop the code snippets from the bottom onto the blanks in the Python script to retrieve a list of network devices from Cisco DNA Center. Not all options are used.
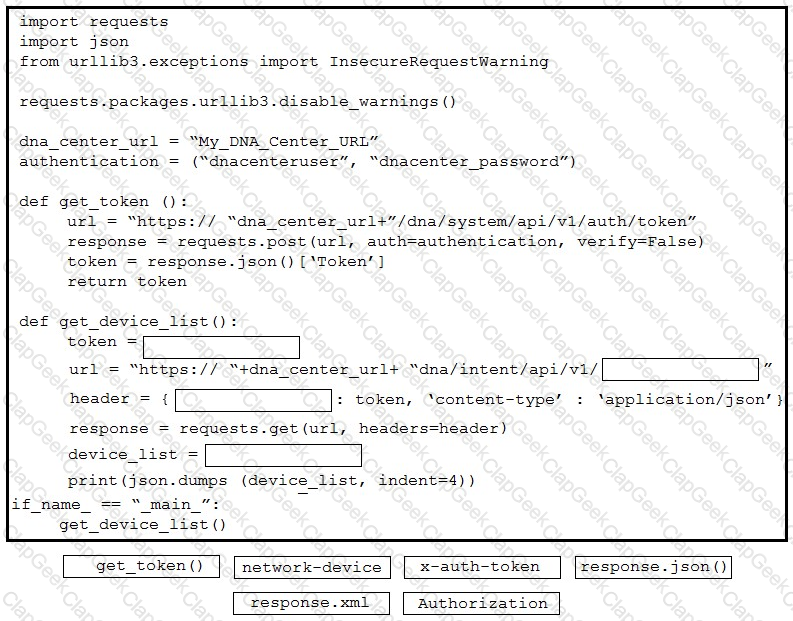
A developer starts to learn about building applications that use Cisco APIs. The developer needs access to Cisco security products in a development lab to test the first new Dlication that has been built. Which DevNet resource must be used?
Refer to the exhibit.
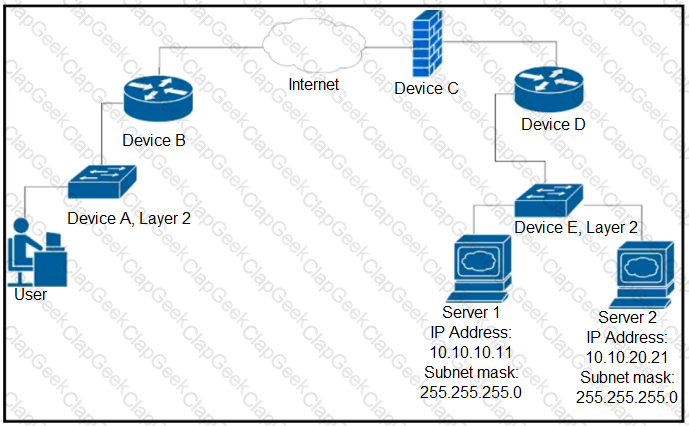
Up to which device does the communication server 1 and server 2 go?
Which REST architectural constraint indicates that no client context should be stored on the server between requests?
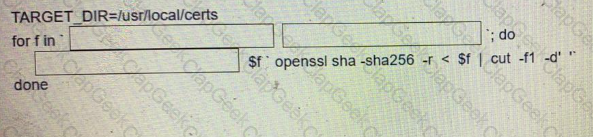
Fill in the blanks to complete the Bash script in which each file in a directory is renamed to Its SHA256 hash?
Fill in the blanks to complete the cURL command that invokes a RESTful API to retrieve a resource in JSON format using OAuth.
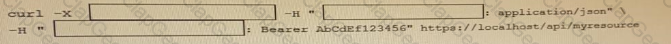
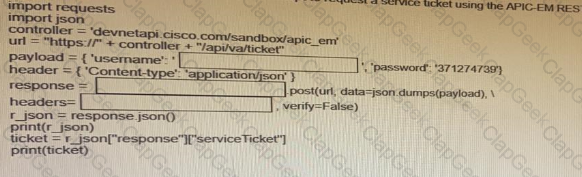
Fill in the blanks to complete the python script to request a service ticket using the APIC-EM rest API for the user “devnetuser”.
Drag and drop the descriptions from the left onto correct application deployment models on the right.
Which two descriptions can be given to an application that is interacting with a webhook? (Choose two.)
Refer to the exhibit.
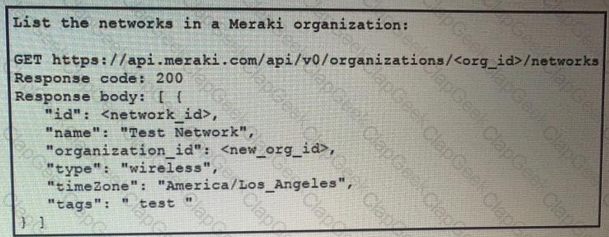
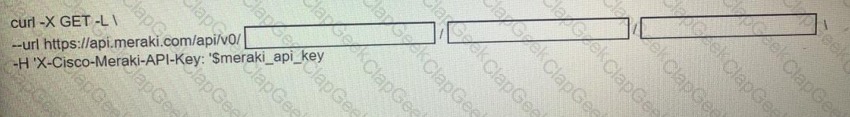
Fill in the blanks to complete the cURL command to the list of networks in the Meraki organization with an id of 384279060
Refer to the exhibit.
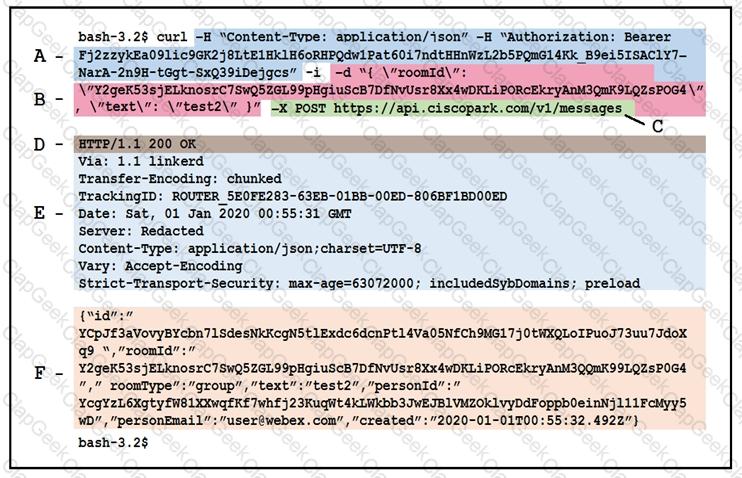
Drag and drop the descriptors from the left onto the correct parts of the API request and response on the right.
Refer to the exhibit.
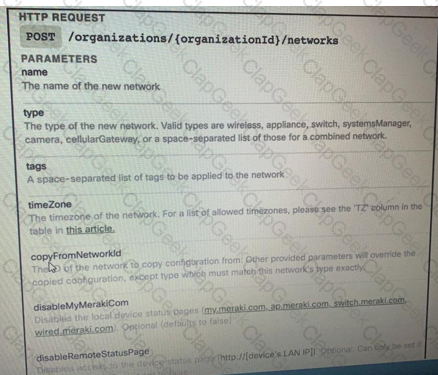
Drag and Drop the code from the bottom onto the box where the code is missing on the Meraki Python script to create a new network
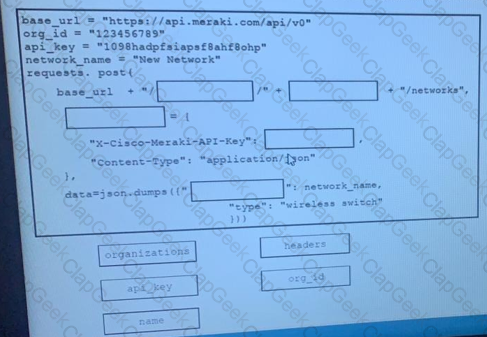
Refer to the exhibit.
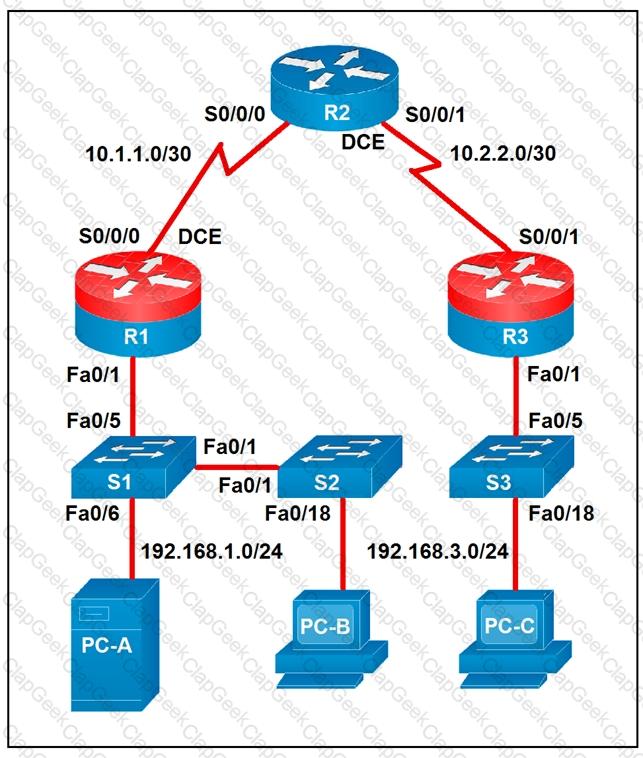
Which two statements about the network diagram are true? (Choose two.)
Drag and drop the network automation interfaces from the left onto the transport protocols that they support on the right. Not all options are used.
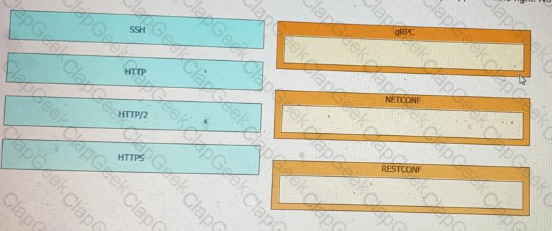
Refer to the exhibit.
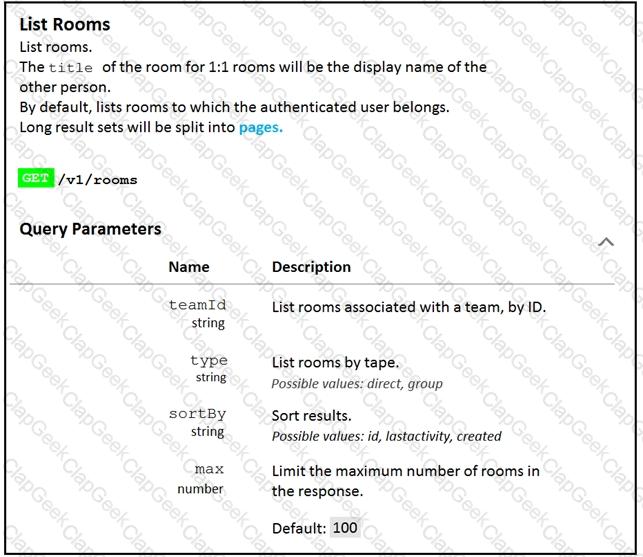
Fill in the blank to complete the query parameter and value so that the result set is returned in reverse chronological order (most recent first) based on when message were entered.

Drag and drop the element of the Finesse API on the left onto the description of its functionally on the right.
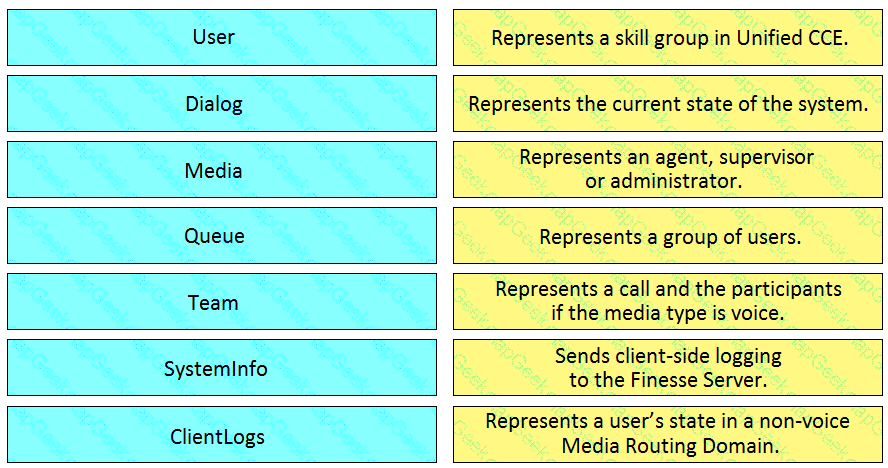
Refer to the exhibit.
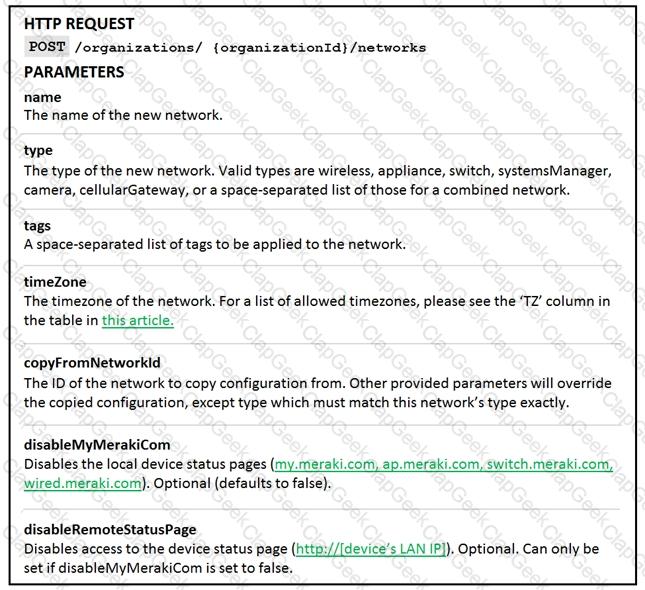
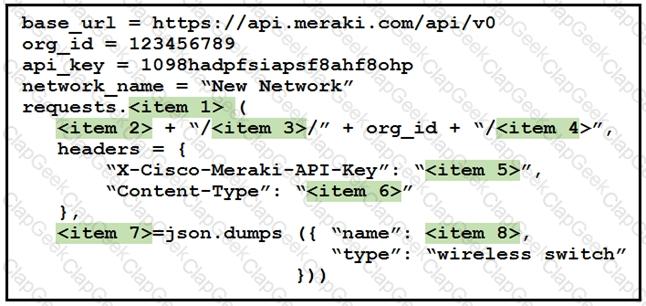
Drag and drop the code from the left onto the item numbers on the right to complete to Meraki python script shown in the exhibit.
Refer to the exhibit.
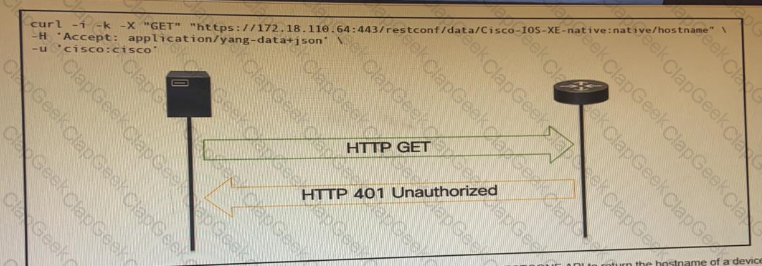
OR
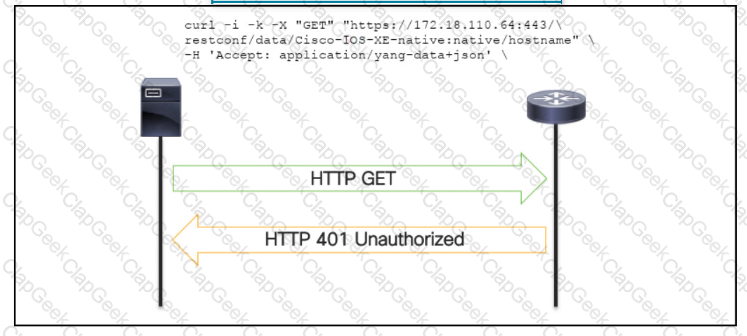
An administrator attempts to perform a GET using the Cisco IOS XE RESTOCNF API to return the hostname of a device. The sequence diagram illustrated the HTTP message observed. Which change to the API request resolves the issue?
Which two statements describe the advantages of using a version control system? (Choose two.)
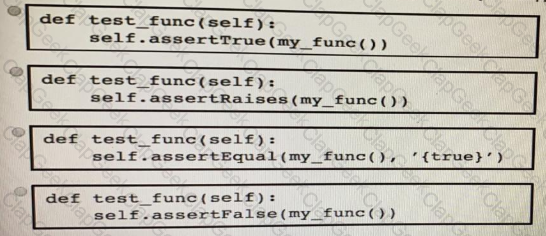
A function my_func() returns True when it executes normally. Which python snippet tests my_func()?
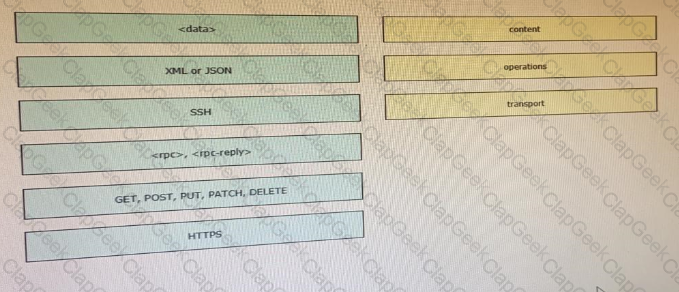
Drag and drop elements of the RESTCONF protocol stack from the left onto the correct description on the right. Not all elements on the left are used.
A company has written a script that creates a log bundle from the Cisco DNA Center every day. The script runs without error and the bundles are produced. However, when the script is run during business hours, report poor voice quality of phones calls. What explains this behavior?
Which two statements are true about Cisco UCS manager, Cisco Intersight APIs? (Choose two.)
Which device is used to transport traffic from one broadcast domain to another broadcast domain?
Refer to the exhibit.
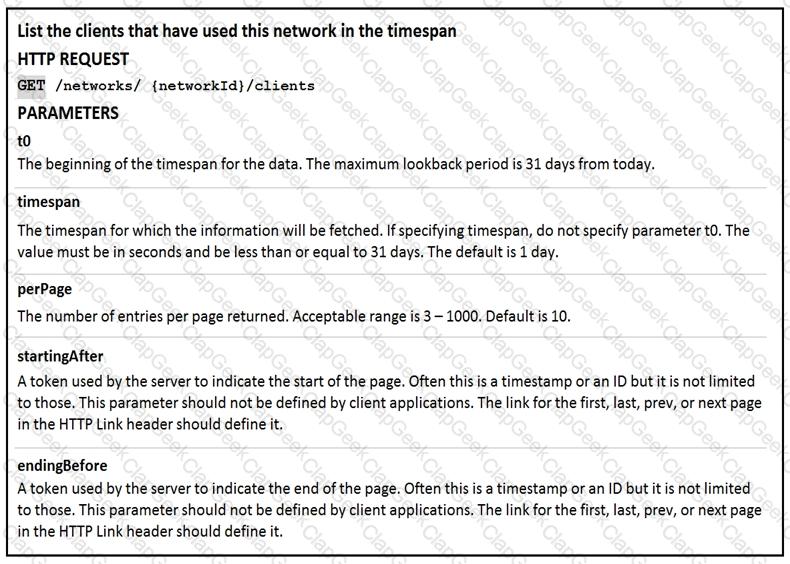
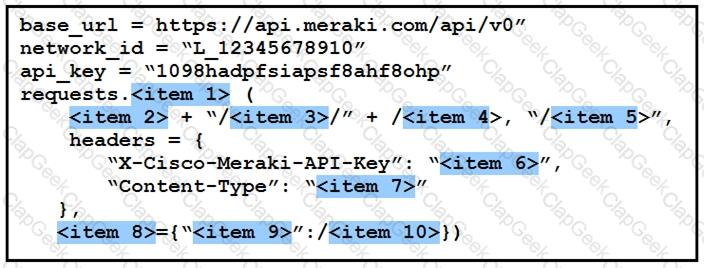
Drag and drop the code from the left code from the left onto the item number on the right to complete the Meraki code to obtain a list of client which have used this network.
Refer to the exhibit.

A REST API retune this JSON output for a GET HTTP request, Which has assigned to a variable called “vegetables” Using python, which output is the result of this command?

Which type of HTTP method is used by the Meraki nad webex teams APIs to send webhook notifications?
Which two statement describe the role of an artifact repository in a CI/CD pipeline? (Choose two.)
What is used in Layer 2 switches to direct packet transmission to the intended recipient?
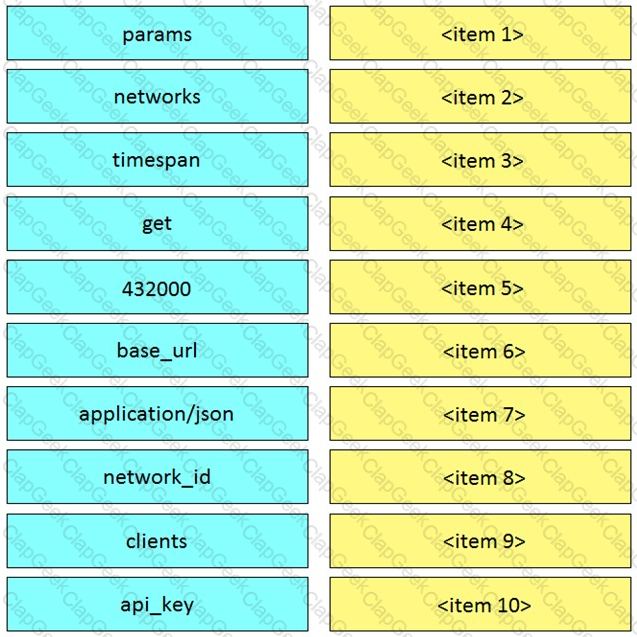
Drag and drop the function on the left onto the type of plane that handles the function on the right.
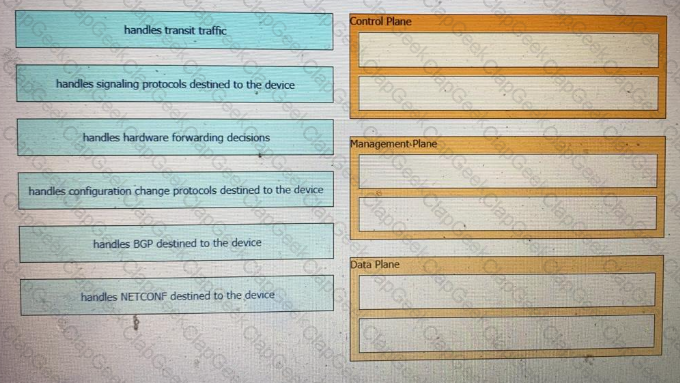
Drag and Drop the GIT commands from the left onto the right that add modified local files to a remote repository. Not all options are used
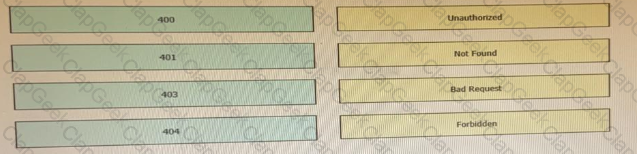
Drag and drop the HTTP status codes from the left onto the correct descriptions on the right.
Which mechanism is used to consume a RESTful API design when large amounts of data are returned?
Refer to the exhibit.
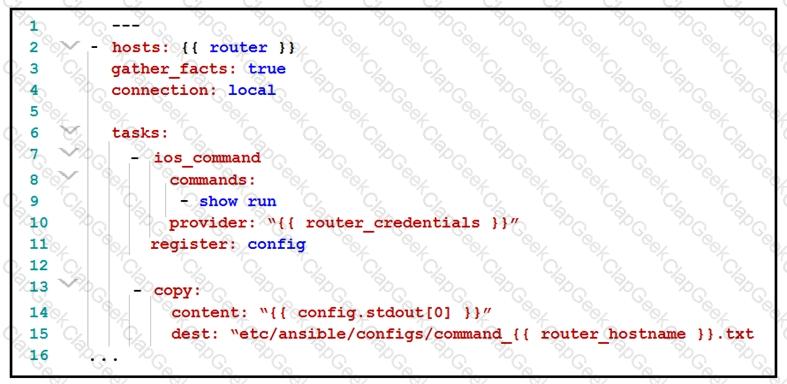
What is the effect of this Ansible playbook on an IOS router?
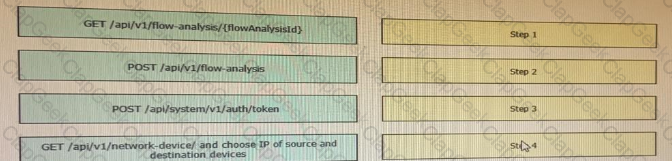
Drag and drop the requests from the left into the correct order on the right to create and check the path trace between two devices using Cisco DNA center API.
Package updates from a local server fail to download. However, the same updates work when a much slower external repository is used. Way are local updates failing?